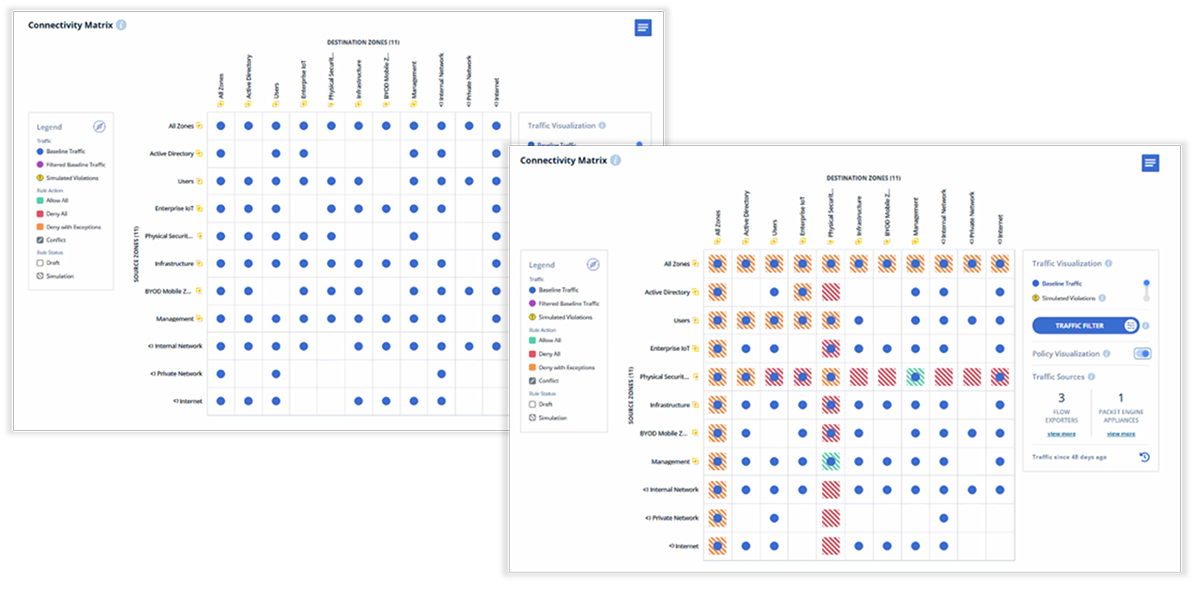
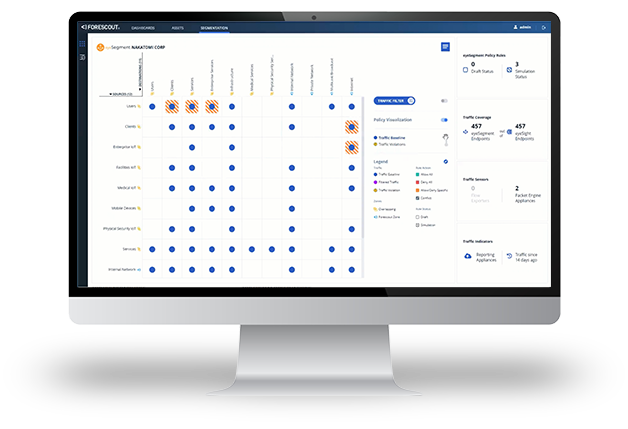
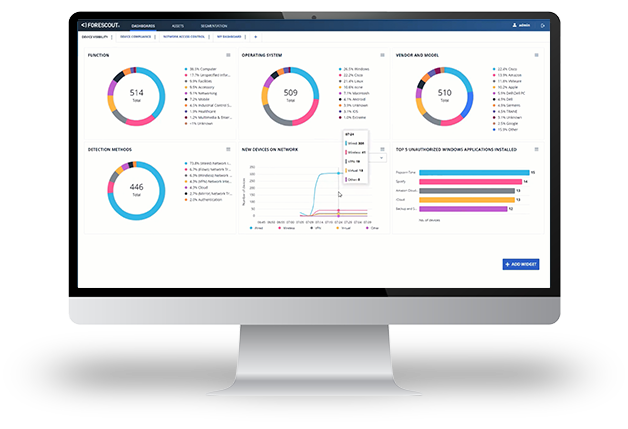
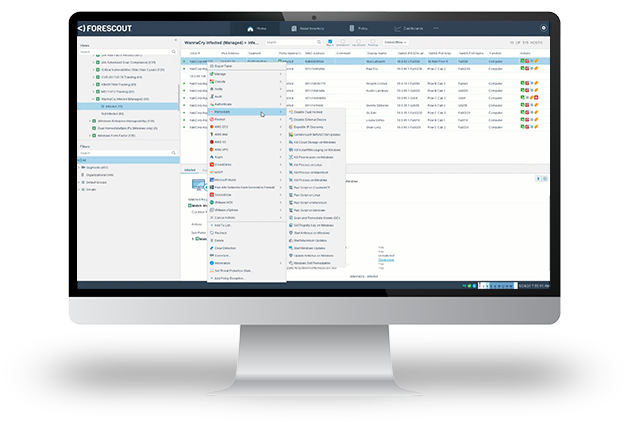
Customer Success with Network Segmentation Management

Read More“Segmentation is an absolute must-have, but to get there, you need full visibility and a clear understanding of your assets. Forescout is invaluable for identifying, consolidating and segmenting assets as we continue to grow by acquisition.”
— CISO, Fortune 500 Manufacturing Company

Read More“In short, Forescout is the front line of our active defense. It gives us the information we need to make smart decisions about security as well as infrastructure and operations.”
— Hector Mendez, Chief Security Officer, Mobility ADO

read more“To gain the functionality that Forescout provides – from seeing and managing assets to triggering control actions and accelerating zero trust segmentation – we would have needed multiple tools. Going with Forescout was far more cost-effective.”
— Jeff Haidet, Director of Application Development and Architecture, South Central Power Co.