OT:ICEFALL
A Decade of Insecure-by-Design Practices in OT
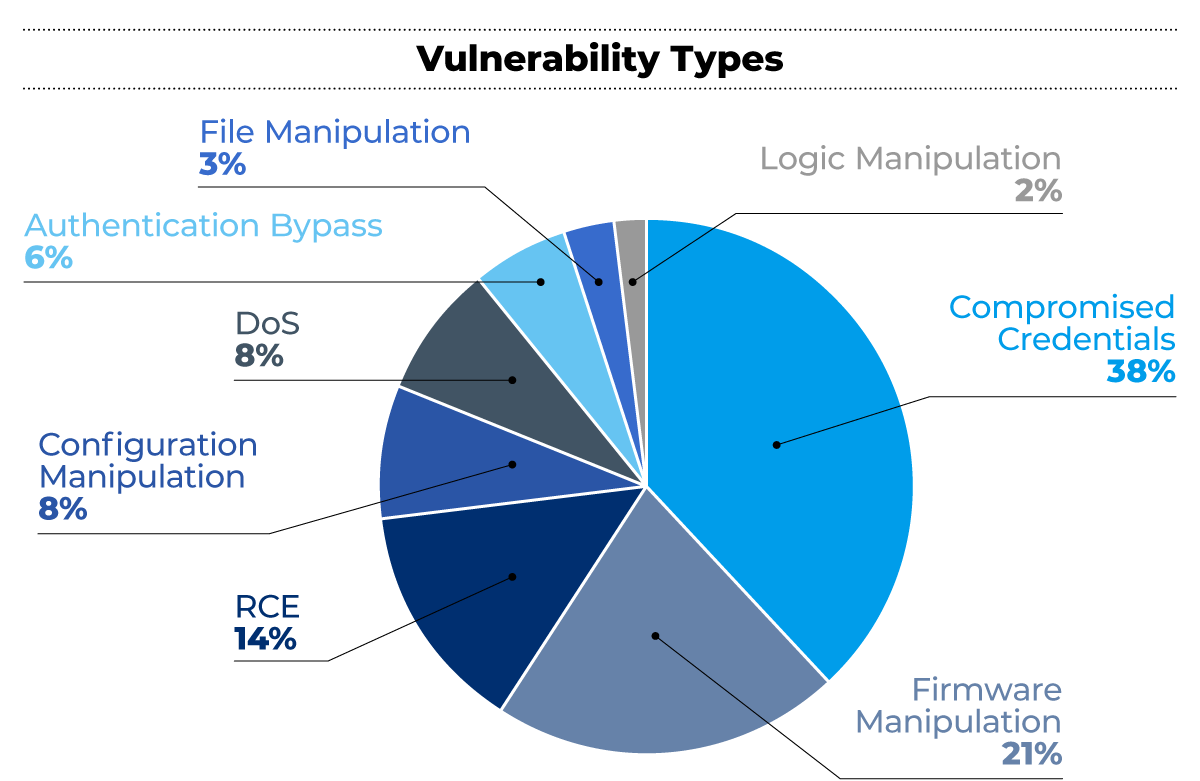
Forescout Vedere Labs has discovered a set of 61 vulnerabilities affecting devices from 13 operational technology (OT) vendors caused by insecure-by-design practices in OT. The affected products are known to be prevalent in industries such as oil and gas, chemical, nuclear, power generation and distribution, manufacturing, water treatment and distribution, mining, and building automation.