Network Security
Discover, assess and enforce the compliance of all connected assets.
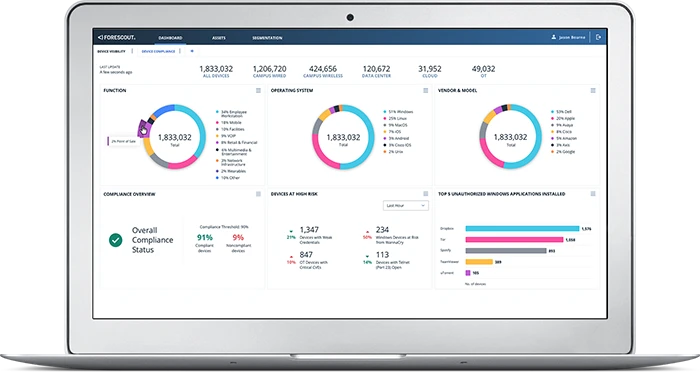
Today’s enterprise networks combine traditional IT devices with smart IoT sensors and OT assets that interact with the physical world to generate business value. This growth in connected assets increases the attack surface and creates new network blind spots where cyber risk goes unchecked.
It’s time to rethink your approach. Learn more in our Five Steps to Combating Emerging Threats with Network Security ebook.