Security Automation
Beat the cyber skills shortage by automating discovery, assessment, compliance, enforcement, detection, orchestration and response
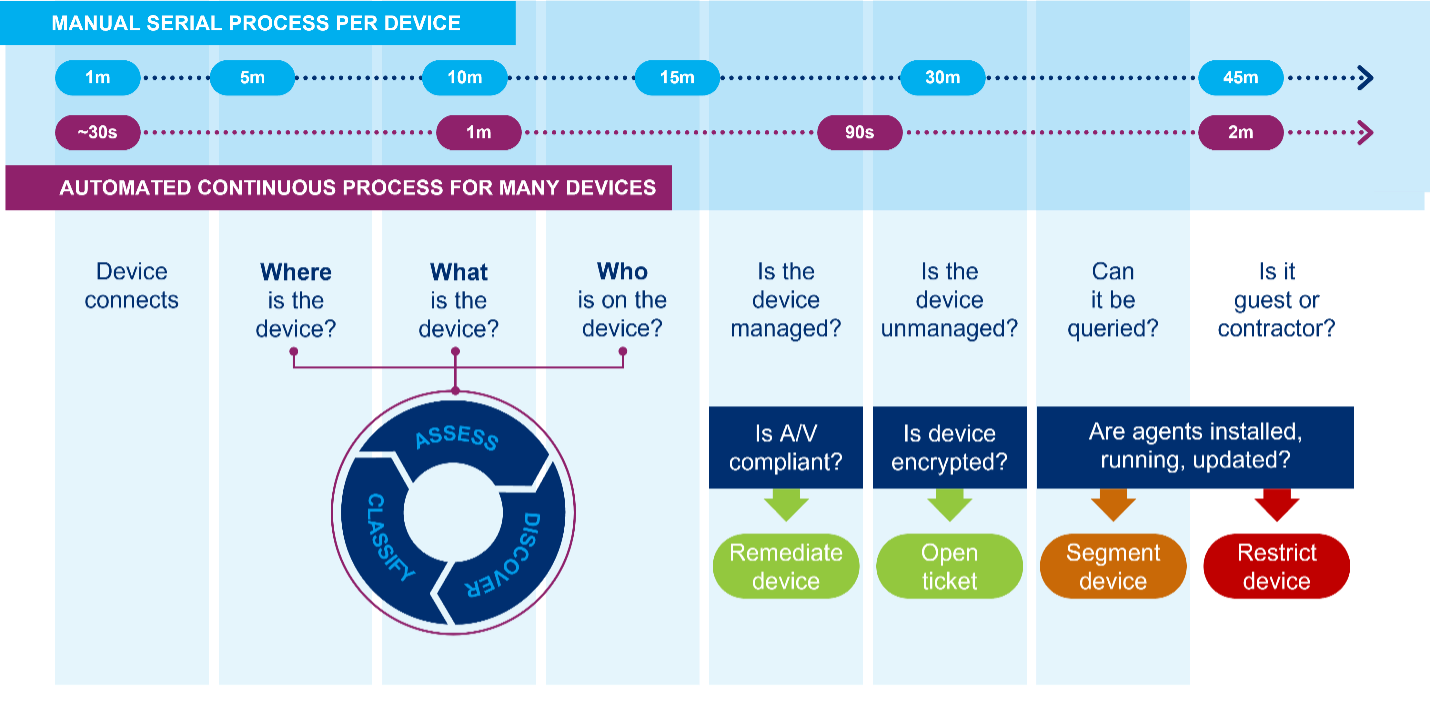
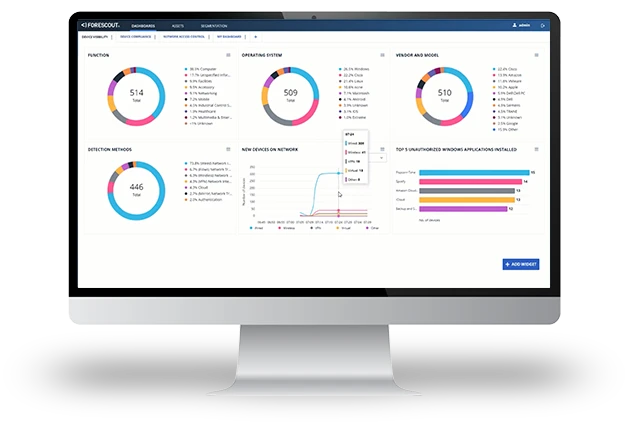
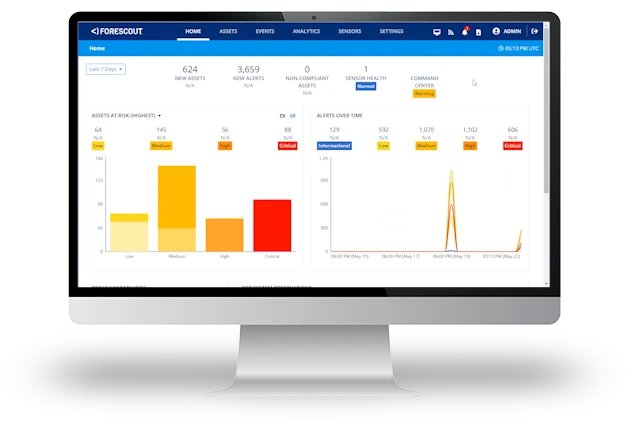
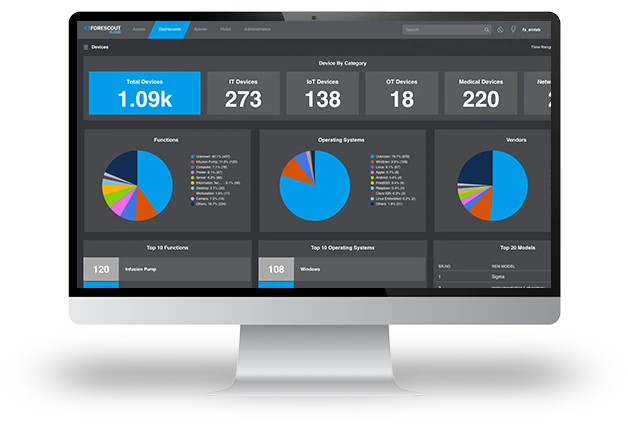
The cybersecurity skills gap, exploding number and type of connected assets and evolving threat landscape are compelling SOC teams to embrace security automation so they can focus on what can’t be automated. Fortunately, many of the routine tasks traditionally handled by SOC teams can be translated into automated policies that drive orchestrated actions among security products.