Cybersecurity for Manufacturing
Industrial Resilience: Securing Manufacturing Operations in the Digital Age
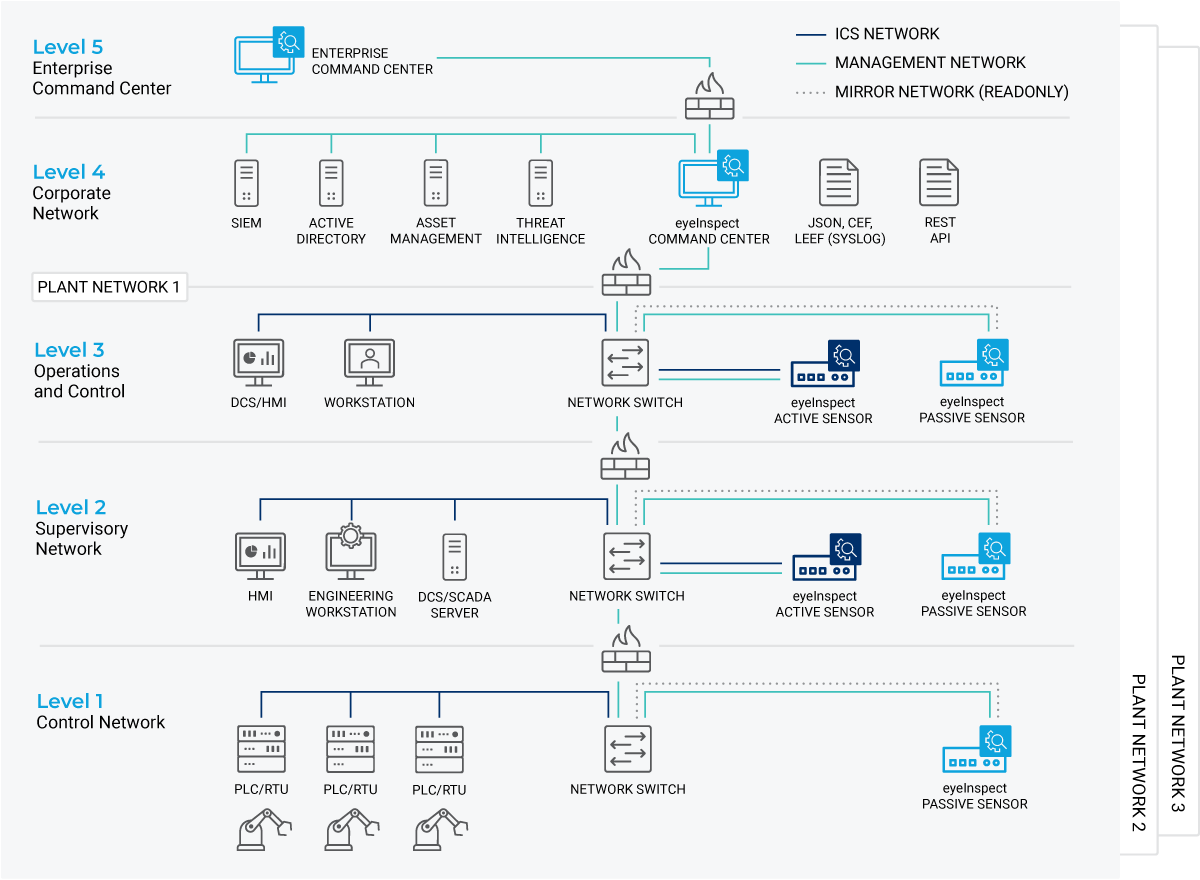
If you thought increasing efficiency was your only goal, it’s time to rethink your priorities. The rise of digitalization in industrial operations brings increased flexibility and performance but also creates new security challenges.
Ransomware attacks, supply chain vulnerabilities, and the growing use of remote connections all contribute to this increasingly complex threat landscape. Now, it’s not just about boosting productivity—it’s about protecting your systems from threats that could bring everything to a halt.
You’ve already made key investments in security technologies. So, what more do you need? The answer isn’t more tools, it’s about making what you already have work seamlessly together to effectively protect your operations.