Rough Around the Edges
The State of OT/IoT Routers in the Software Supply Chain
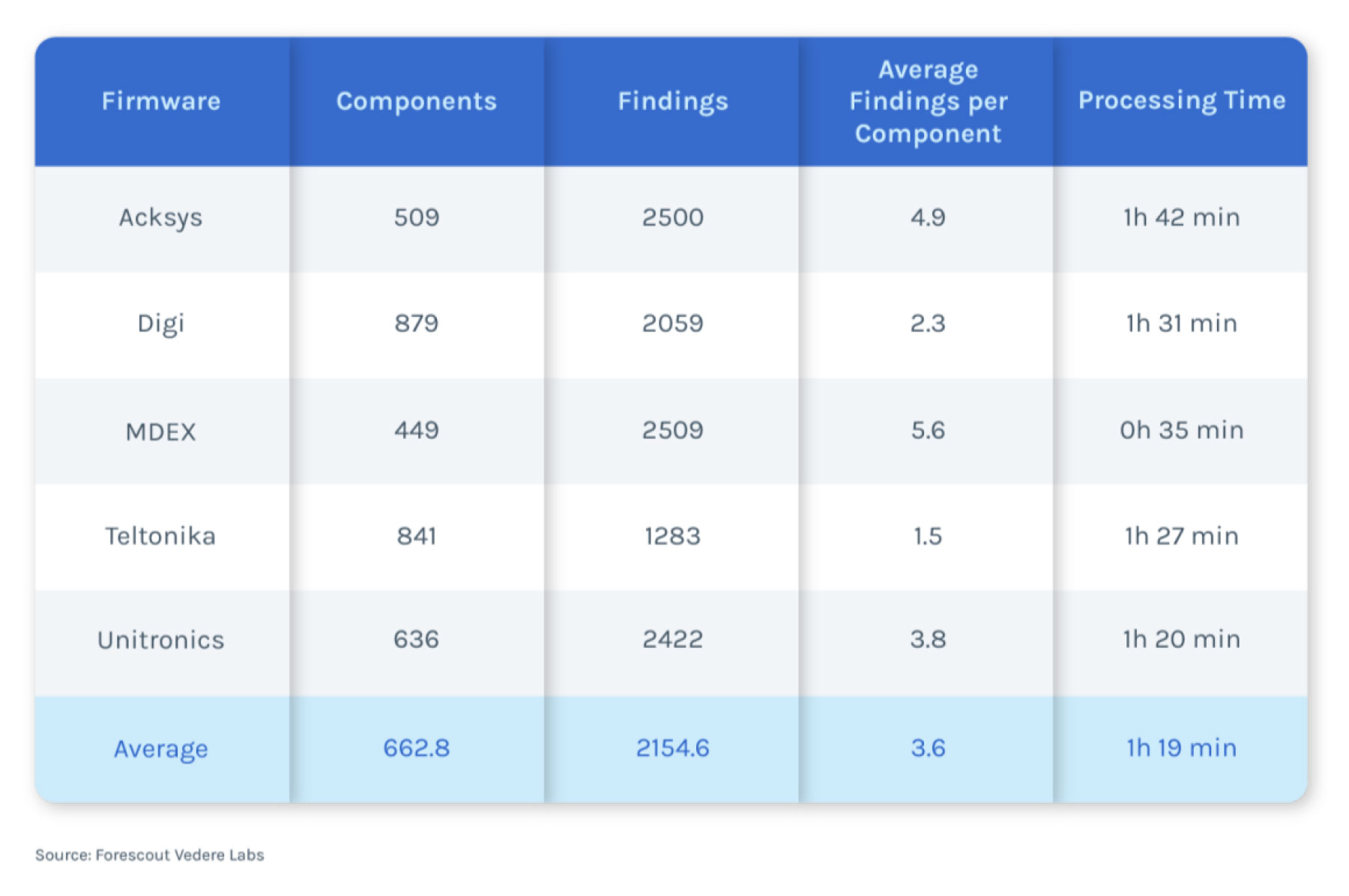
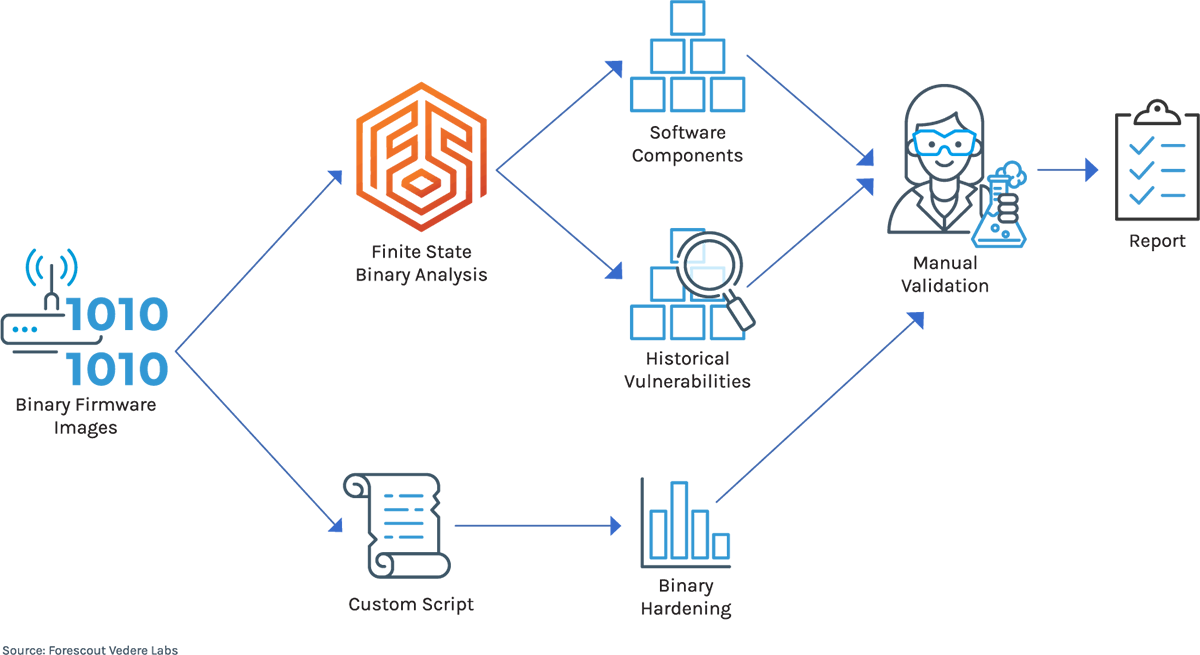
Under the surface of assets connecting the internet to remote, industrial operations are a world of vulnerabilities. Picture a rural electrical substation or an offshore oil rigging site out in the ocean. The problem? Understanding the risk scale means gathering the full scope of firmware components – and the open-source software used within cellular routers. To more precisely understand the problem, Forescout partnered with SBOM experts Finite State to identify common models of a specific class of devices.
See which vendors. Know the risk. Take control and reduce the threat.