Asset Visibility and Behavior: The Keys to Segmentation Success
Recently, Gartner® refreshed one of its foundational cybersecurity research, “The 6 Principles of Successful Network Segmentation Strategies.”1 The principles covered in the research are tried and true. Segmenting networks to improve security and performance is nothing new to security teams, yet the same challenges persist year after year. Gartner analysts are keenly aware of that, having based their findings on “hundreds of network segmentation inquiries over the past two years with network security and I&O analysts.”
The research lays out six key principles correlated with success:
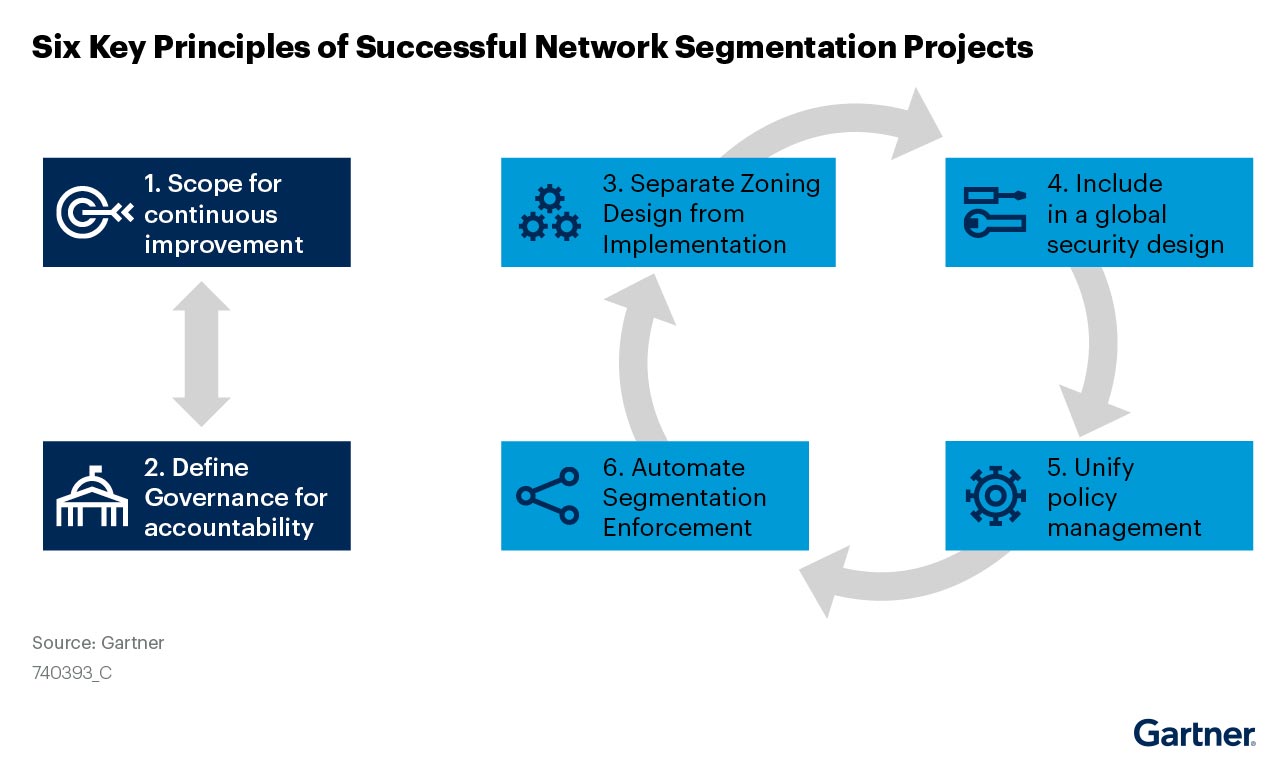
While all six principles are important, in Forescout’s experience with customers, we believe the overriding determinant of success is #3: Separate zoning design from implementation.
Why? Gartner says it best:
Mixing segmentation design with implementation tools is the canary in the coal mine of a doomed-to-fail network segmentation project.1
Let’s examine why separating zoning design from implementation is so essential, based on hundreds of Forescout customer segmentation projects.
First things first: device visibility and behavior
Segmentation is all about understanding how assets are communicating with each other, but that behavior is predicated on knowing what’s on your network. Designing policies based on partial visibility of some of your assets is a waste of time. You need to have a continuously updated, real-time inventory of all connected assets. Moreover, you want to design policies based on the desired behavior of compliant assets only. That requires automatic assessment and remediation of noncompliant assets upon discovery as a starting point.
We believe the process that Forescout guides customers through aligns with Gartner research:
- IP classification: Discover/assess compliance of all connected assets and group them into a logical business hierarchy.
- Flow visibility: Map all endpoints and visualize traffic flows in an intuitive matrix to observe current behavior.
- Flow determination: Analyze flows to determine what should/shouldn’t be happening based on policy.
- Policy creation: Write policies to enforce desired behavior, which are automatically recorded in the policy decision point (PDP).
- Policy simulation: Turn on policies in simulation mode to visualize their impact on traffic flows and refine them without causing harm.
- Continuous monitoring: Ensure your segmentation design withstands dynamic changes and alert on deviations from intended policies.
This process also aligns closely with the steps described in NIST SP 800-207 part 7.3: Steps to Introducing ZTA to a Perimeter-Based Architected Network:
- Identify actors on the enterprise
- Identify assets owned by the enterprise
- Identify key processes and evaluate risk associated with executing process
- Formulate policies for the zero trust architecture (ZTA) candidate policy enforcement point (PEP)
- Identifying candidate solutions
- Initial deployment and monitoring
- Expand the ZTA
Note that NIST advises organizations not to think about implementation tools (or PEPs) until step 4, after the segmentation design is completed. Or, as Gartner says,
Build your zoning strategy separate from the specific implementation constraints of the environment. Design first, pick the tool second. Don’t let the tool drive the design. 1
The streetlight effect, or the drunkard’s search
Despite these consistent recommendations, here’s how segmentation planning plays out among security teams all too often:
- Mistake #1: You start by evaluating enforcement technologies first, bringing in every kind of security vendor – endpoint-centric (VMware, Crowdstrike, IBM), boundary centric (Palo Alto, Check Point, Fortinet), network centric (Cisco SDA, Juniper, HP) and workload centric (AWS, Illumio, Azure).
- Mistake #2: You choose one or more of these implementation tools without visibility into all the assets in your environment and how they communicate with each other. Instead, you make a leap of faith and, for example,assume your campus is your biggest risk. How can you be sure without seeing all connected assets, and their behavior?
- Mistake #3: You write allow/deny policies based on how you want your assets to communicate, but when it comes time to enforce those policies, the segmentation tool(s) you purchased don’t cover every asset. Agents only work on agented systems, Azure only sees what’s in Azure’s cloud, the firewall only sees the traffic that goes through it, and so on. This approach is like the famous streetlight effect – a type of observational bias that describes someone’s tendency to only search for something where it is easiest to look.
That’s not to say that you won’t need to buy various enforcement tools… later. They are each very good at what they do. But they also have no way of visualizing your enterprise traffic and can’t write policies across all assets, so how can they be good starting points? You may need to buy a next-generation firewall and perhaps upgrade to the latest switches, later. Just be sure to design your segmentation first, and don’t base it on any one tool.
Foolproof your project with design-first segmentation
The failure rate for network segmentation projects is high, and most projects last longer than the average tenure of a CISO. 1
To steer clear of a failed segmentation project, focus on asset visibility and behavior so you understand your risk upfront and select your segmentation tools last. If you’re looking for a tool to facilitate a design-first segmentation approach, Forescout® eyeSegment is the only one on the market with an intuitive matrix for real-time traffic analysis. It lets you see upfront what your risks are and what your policies need to be, so you can confidently write them and simulate their impact without causing actual business disruption. This is how you determine exactly what implementation tools you need to enforce your design.
1 The 6 Principles of Successful Network Segmentation Strategies, Jeremy D’Hoinne, Andrew Lerner, 19 November 2022.
Disclaimer: GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.