IoT Security
Automate IoT Security and Eliminate Blind Spots for Every Device
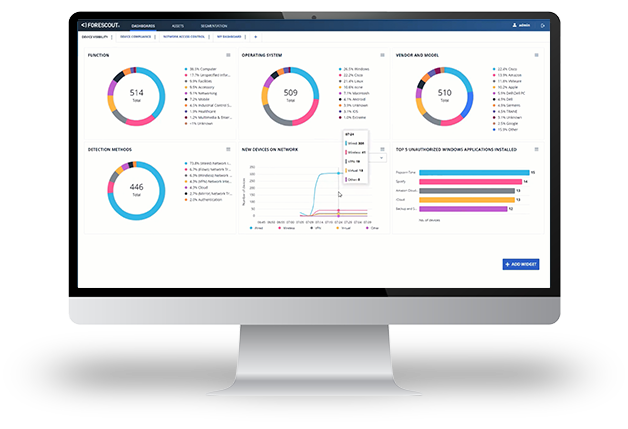
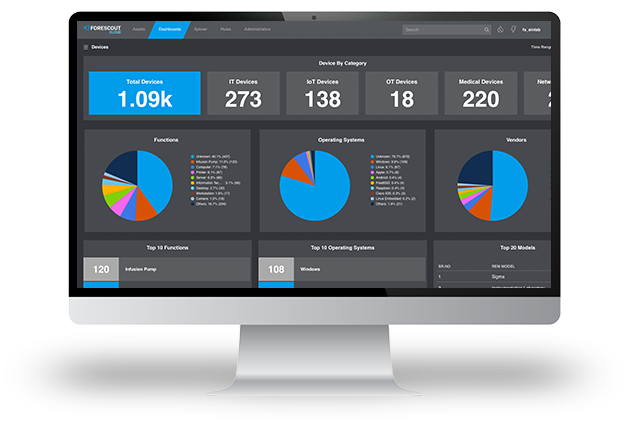
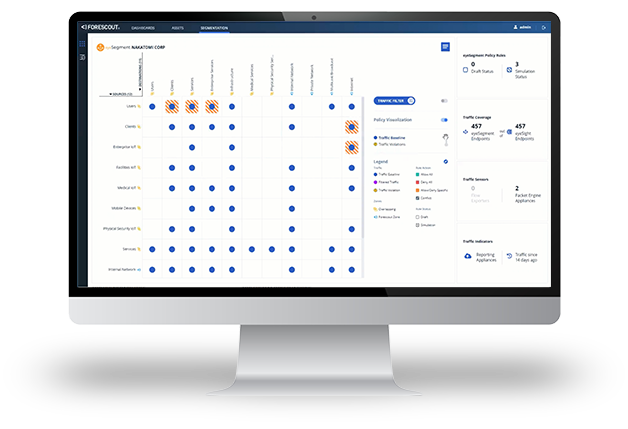
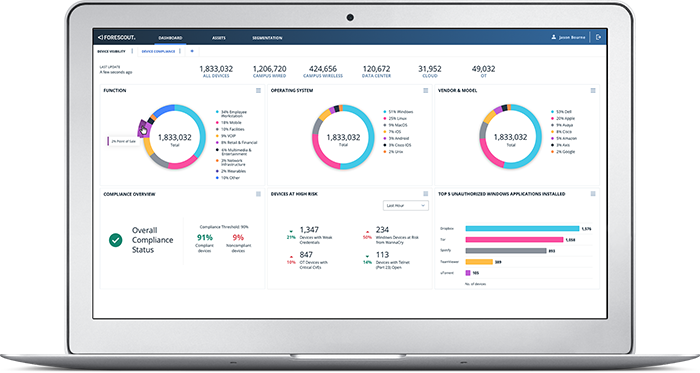
Increasing reliance on Internet of Things (IoT) devices for business operations, efficiency, automation and digital transformation initiatives comes with additional risks of an ever-expanding attack surface. Forescout’s zero trust approach provides actionable visibility and automated risk-based segmentation and compliance enforcement of every IoT, OT, Internet of Medical Things (IoMT) and IT device the instant they connect to your network without ever requiring an agent. From connection to a device’s end of life, the Forescout Platform efficiently manages asset inventory and lifecycle management of every device.