Network segmentation projects are on everyone’s radar for 2019. These projects are a massive undertaking that can drastically improve the security of an organization, but they also touch every part of the business and introduce considerable risks. So what is network segmentation for security and what does it provide?
- It splits the network into zones that contain data with similar compliance requirements
- By segmenting the network this way, you reduce the scope of compliance and simplify security policies
Generally speaking, the more you segment a network the more secure that network will be. A key challenge is avoiding under or over segmentation and maintaining the segmentation integrity over time.
Over the past year, we would estimate that 90 percent of the companies that we have talked to have segmentation projects in their plans this year. It is something everyone wants to do, but it is not always clear where to start, what the risks are, or if it’s worth the money and effort. A successful segmentation project can have tremendous benefits for improving security, network manageability, and yield a positive return on investment (ROI) to the business. But it is not without risk.
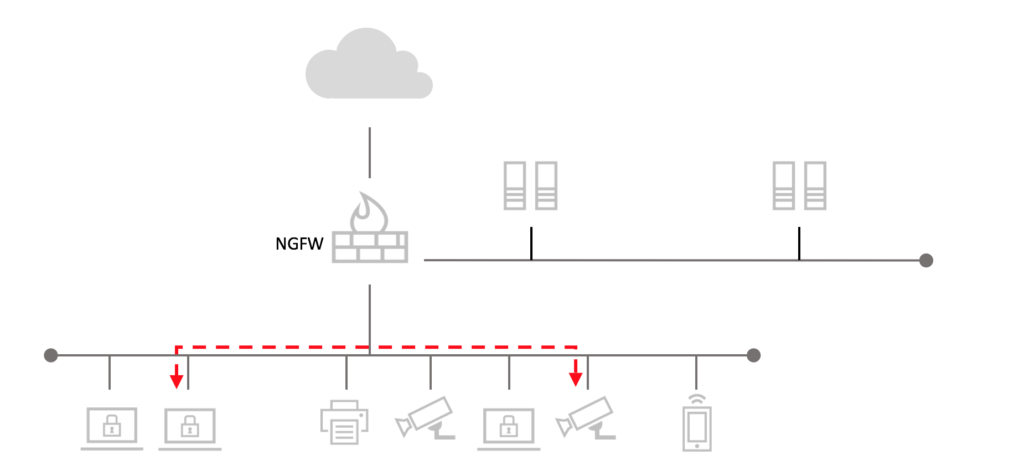
Many companies know their enterprise networks are not as secure as they would like. They have a perimeter firewall—and possibly other tools like Security Information and Event Management (SIEM), Intrusion Prevention System (IPS), Advanced Threat Detection (ATD) protecting the network perimeter, but behind that is the internal “trusted” network, with no standardized segmentation methodology. This is affectionately known as the crunchy shell/gooey center network architecture. This delicious-sounding design poses a major security risk, because if malware gets past the perimeter, there is nothing to stop it from attacking every other device on the internal network. Email, Dropbox, and USB drives are just a few ways malware tries to bypass that perimeter, and once inside it can remain undetected for days, weeks or even months (pg 38 of Verizon’s 2016 Data Breach Investigations Report).
So how should a company approach a segmentation project? To start, think from the inside out. Start with full network visibility, then use that visibility to identify networks, data, and devices requiring segmentation. The last step is to deploy policies to automatically segment devices and users to the appropriate network.
In 2009, Forrester created the Zero Trust Model of Network Security. This model stems from the conclusion that for today’s digital business, the traditional perimeter-based security model is ineffective against malicious insiders and targeted attacks. NextGen Firewalls (NGFW) were some of the first vendors to adopt the “Trust-but-Verify” approach and play a key role in the Zero Trust Model. Google developed its own solution, BeyondCorp, which is based on the concept that the perimeter no longer exists and organizational borders are disappearing.
The Zero Trust Network Architecture advocates using Next-Generation Firewall (NGFW) to enforce network segmentation at every layer of your network. As you start the planning process for your segmentation project, you’ll uncover two issues:
- You realize your internal network traffic does not flow through a NGFW and you need to completely re-architect everything so this internal traffic can be seen and secured. This causes many segmentation projects to come to a screeching halt. Internal traffic not headed for the Internet does not pass through the NGFW (think of a laptop talking to a printer), and therefore can’t be inspected. Migrating from a flat network to a fully segmented network is a massive undertaking. It requires a good deal of operational planning and introduces significant risk to the business.
- After you decide to re-architect your internal network, you will need to account for the increase in traffic that will now be inspected. Intrusion Prevention Systems, ATDs and NGFWs are powerful devices that can solve a lot of problems but they come at a cost, and this increased cost may negatively impact the project’s ROI.
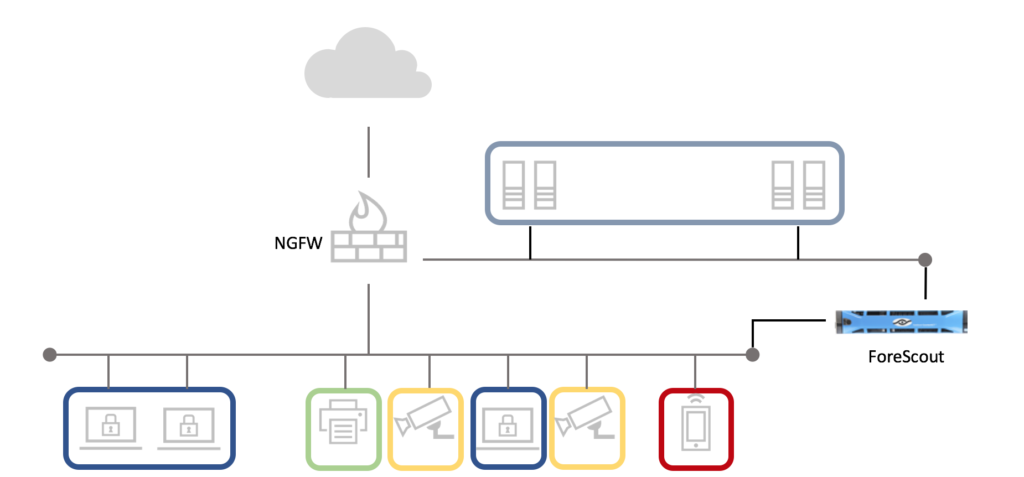
So how do you tackle this project without breaking the bank or completely redesigning your existing network? This is where Forescout comes in. The Forescout platform complements NGFWs and enables you to deploy a “virtually segmented” network on top of your network as it is today. Forescout does this by mapping new network segments onto your existing networks, and integrating with your existing network devices to coordinate access. Because Forescout can integrate with your switches, routers, wireless controllers and firewalls, we can extend the network segments around each device that connects to the network. And Forescout does this automatically, regardless of where or how a device connects, and without installing an agent on the device. Using NGFWs and Forescout together, you can deploy right-sized NGFWs at natural network boundaries to control access between segments, and let Forescout secure the devices within each segment. Armed with this approach, let’s look at a use case that one of my customers wants to implement. This company has thousands of existing IP cameras they want to secure. When a new IP camera attaches to the network, not only do they want it moved to the proper segment, they also want to alert the operations team, log the event and create rules that restrict access to only the server required for the cameras to work. When a device attaches to the network and Forescout classifies it as an IP Camera, the policy will:
- Connect to the wireless controller and assign the camera to the CAMERA network segment.
- Connect to the Palo Alto Networks firewall and create rules to limit the camera’s Internet access.
- Connect to the access switch and create an Access Control List (ACL) restricting network access inbound to the camera.
- Make an API call to Splunk with details of the device, the connection event and the policy actions taken.
- Post a Slack notification to the /#OpsChanel, notifying the admins.
This all happens with no human interaction and no agent is required on the device. By leveraging Forescout’s real-time visibility, classification and posturing capabilities, customers can truly achieve automated, real-time network segmentation.
If this piques your interest, we have two resources that might be valuable to you. One discusses our integration with Palo Alto Networks NGFW. The other outlines Forescout’s approach to network security segmentation. Check them out, and as always, feel free to contact us with any questions.