Vedere Labs recently developed a proof-of-concept (PoC) ransomware for IoT (R4IoT) using as an example attack scenario a hospital network containing IoT devices such as IP cameras, IT workstations and OT in the form of building automation controllers. The goal of R4IoT was to:
- Gain access via the IoT devices
- Move laterally to the IT network
- Exfiltrate and encrypt data on the IT systems
- Launch denials of service (DoSs) on the building controllers, thus switching off important physical functions of a building, such as lights and ventilation
This type of attack exploits an increased IoT attack surface and adds a new layer of extortion to common ransomware threats by targeting IoT and OT. We developed the concept based on threat intelligence we collected about the direction that ransomware actors could soon be moving to and the intent of helping organizations prepare for it. In the technical report accompanying the PoC, we describe in detail readily available detection and response actions for an R4IoT attack that serve as a playbook for organizations looking to defend against both current and future threats.
While novel, the R4IoT threat applies to almost every industry and organization nowadays. However, we chose a hospital for our attack scenario because of the diversity of IT, OT, IoT and Internet of Medical Things (IoMT) devices that healthcare delivery organization (HDO) bioengineers and SOC teams must manage. In this blog post, we explore why healthcare organizations would be a perfect target for an R4IoT-like attack, what that attack might look like and, most importantly, what you can do to avoid becoming a victim.
Why is healthcare vulnerable?
Healthcare was either the most or second-most affected vertical in Vedere Labs’ recent vulnerability research. That is true whether we look at vulnerabilities we found and disclosed on TCP/IP stacks (Project Memoria), IoT remote management platforms (Access:7) or OT equipment (OT:ICEFALL).
As mentioned above, that distinction is mainly due to the diversity of devices in HDOs. These complex institutions host a broad range of devices that are increasingly interconnected, frequently run legacy software and are often poorly segmented. IT devices process and exchange sensitive data, such as patient health records and financial information. OT and IoT devices are used for diverse functions such as building automation and patient entertainment. Unique to healthcare is the Internet of Medical Things (IoMT) – connected medical devices essential to clinical care that can generate and exchange patient data with other devices.
These new connected technologies improve efficiency and quality of care. They also introduce new security risks. Especially since the COVID-19 pandemic, there has been an increase in the number and sophistication of cyberattacks on hospitals. So far, these attacks have been mainly ransomware targeting IT systems. But the increased connectivity and associated vulnerabilities are not restricted to IT devices.
Relevant ransomware activity in healthcare
Ransomware attacks on HDOs increased 94% from 2021 to 2022, with 41% of these attacks targeting U.S. institutions. More important than the increase of attacks is their growing sophistication. Three points stand out from recent activity:
- Changing tactics for initial access – The top ransomware groups impacting healthcare in the first quarter of 2021 were LockBit, Conti, SunCrypt, ALPHV/BlackCat and Hive. Vedere Labs has previously reported on both Conti and ALPHV targeting non-traditional devices, specifically IoT and network infrastructure for initial access. On April 18, the U.S. Department of Health and Human Services (HHS) released an analysis singling out Hive as an “exceptionally aggressive” and “sophisticated” ransomware group that replicated several of ALPHV’s practices and targeted the health sector.
- State-sponsored activities – On July 6, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released an alert about North Korean state-sponsored threat actors using Maui ransomware to target healthcare organizations. The incidents were observed since May 2021 and encrypted servers used for electronic health records, diagnostics services, imaging services and other applications. Maui was designed for manual operation and lacks some features common to major ransomware strains such as an embedded ransom note.
- Extortion doesn’t always require encryption – An attack by the Quantum ransomware group on accounts-receivable recovery company PFC led to a data breach affecting more than 600 HDOs. This breach could be used to force victim organizations to pay to avoid having their data published, an extortion technique that does not encrypt data or prevent access to systems.
Although these characteristics are similar to trends we have observed in other industries and organizations, they point to a changing ransomware landscape where attackers are constantly looking for new ways to gain access to and impact their targets.
R4IoT in healthcare
The original R4IoT attack, shown in Figure 1, leverages internet-exposed IoT devices (such as IP cameras) for initial access and their connection to corporate assets (such as network video recording and other workstations) for lateral movement. Once the attacker reaches a machine that can communicate with a building automation controller, that device is taken offline by exploiting DoS vulnerabilities.
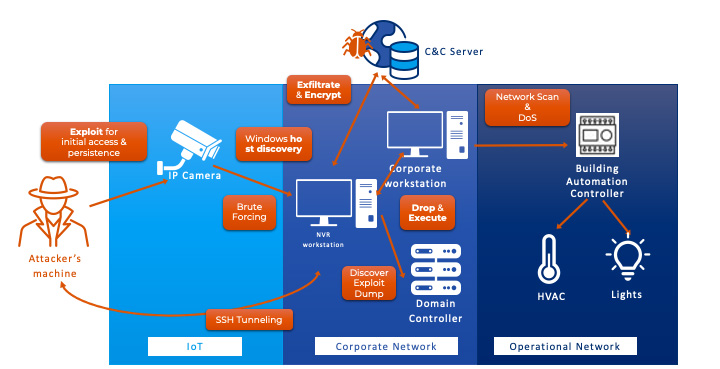
Figure 1 – The original R4IoT scenario
Building automation devices are used in hospitals to control functions such as physical access control, fire alarm systems, lighting and HVAC (heating, ventilation and air conditioning). These functions are not directly connected to patients, but they are critical to delivering patient care.
HVAC systems, for instance, maintain temperature, humidity and air quality throughout a hospital per regulations. Changing some of these parameters can have disastrous consequences: reduced ventilation can increase the spread of airborne diseases such as influenza and COVID-19, and drastic changes in temperature can render operating rooms unusable or spoil biological samples.
So clearly, by taking building automation systems offline, the original R4IoT attack could impact HDOs well beyond data encryption. However, that original scenario stopped short of what singles out healthcare as a target: the clinical network hosting connected medical devices or IoMT, which all too often lacks appropriate segmentation and hosts vulnerable devices. Examples include:
- Infusion pumps running firmware vulnerable to Project Memoria. For instance, BD Alaris is vulnerable to NAME:WRECK while Baxter and B. Braun are vulnerable to Ripple20.
- Imaging devices running the Axeda remote management solution, which is vulnerable to Access:7. Examples include scanners from Bayer, Carestream, GE and Varian.
- Patient monitors running legacy operating systems. Not only patient monitors but also many connected medical devices run legacy versions of Windows that have decades-old vulnerabilities. Two examples we have in our lab running Windows XP are a Smith & Nephew 660HD image management system and a GE CIC Pro central monitoring system.
An R4IoT attack on a surgery center
Figure 2 shows a scenario like the original R4IoT, but instead of leveraging a workstation to attack building automation devices, the attacker leverages a doctor’s workstation to take offline connected medical devices on the clinical network. This obviously has an even greater effect on patient care, since some of these devices are critical to monitor a patient’s condition, sustain life support, or in some cases enable surgeries and other urgent procedures.
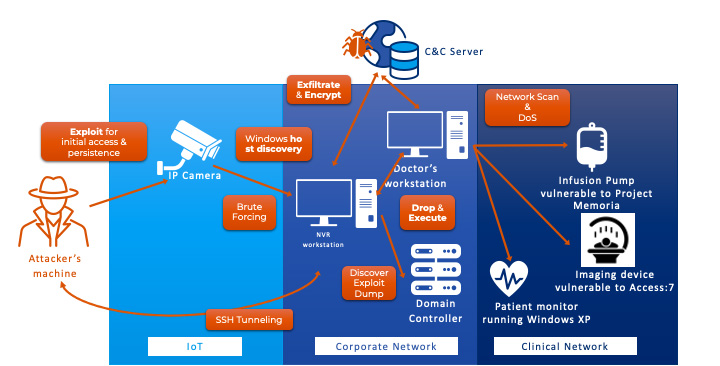
Figure 2 – An R4IoT scenario targeting infusion pumps, imaging devices and patient monitors
Several variations of R4IoT attacks are possible in HDOs. Another example would be the attacker gaining access via vulnerable internet-connected patient telemetry devices, moving laterally to an unpatched nurse’s workstation connected to that telemetry device, then moving to a server hosting patient records, where communication with command-and-control servers is established, and finally attacking either the building automation system or other connected medical devices as in previous scenarios.
Mitigation: How Forescout helps
There are multiple ways to mitigate the impact of ransomware for IoT and minimize the risk of this threat. Here are three mitigation steps based on the NIST Cybersecurity Framework that could be applied to ransomware attacks:
- Identification and protection – Ransomware families tend to be very active with numerous simultaneous attacks. For example, Conti launched more than 400 attacks in 2021. Analyzing such a high volume of attacks can reveal which vulnerabilities are being exploited, so remediation and mitigation actions can be shared.
- Detection – Most tactics, techniques and procedures (TTPs) that ransomware threat actors use are well known and can be detected on the network. For example, tools such as Cobalt Strike and malicious PowerShell scripts are among the favorites for these attacks.
- Response and recovery – The average dwell time for ransomware attacks is five days. Although ransomware attacks are very efficient, they are not fully automated, which often leaves time for incident response and recovery before data encryption.
Implementing the right mitigation requires extensive visibility and enhanced control of all assets in a network. The Forescout Continuum Platform helps to achieve that via:
- Unparalleled insight across your entire asset landscape without disrupting clinical functions. After discovering connected devices, the Forescout Continuum Platform auto-classifies and assesses those devices against company policies. The powerful combination of these three capabilities – discovery, classification and assessment – delivers the asset visibility to drive appropriate policies and action.
- In-depth visibility and cyber resilience with asset and communications inventory based on deep packet inspection (DPI). This allows for network monitoring and threat hunting capabilities, such as threat and vulnerability indicators.
- Accelerated design, planning and deployment of dynamic network segmentation across the extended enterprise to reduce your attack surface and regulatory risk. It simplifies the process of creating context-aware segmentation policies and allows visualization and simulation of policies prior to enforcement for proactive fine-tuning and validation.
- Sharing device context between the Forescout Continuum Platform and other IT and security products to automate policy enforcement across disparate solutions and accelerate system- wide response to mitigate risks.
Figure 3 shows several possible mitigation actions enabled by Forescout against R4IoT, such as visibility of vulnerable assets, detection and stopping of malicious communications.
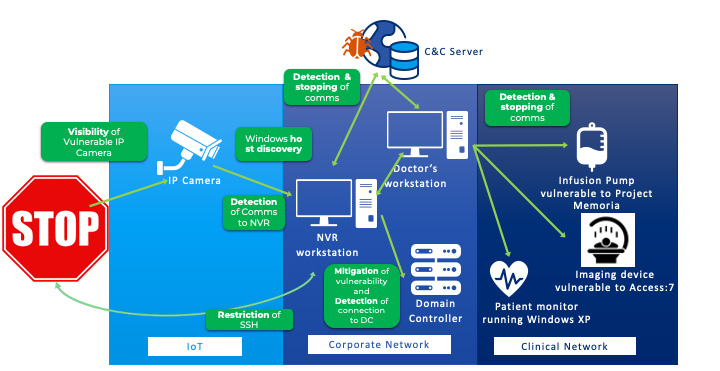
Figure 3 – Possible mitigations against R4IoT
As a concrete example, Figure 4 shows eyeInspect raising an alert for an RDP brute forcing attack from the IP camera to the NVR workstation, which is the first malicious action the attacker takes after gaining a foothold, to be able to move laterally to the corporate network. Figure 5 then shows an eyeSight policy to block the IP camera on the network switch once the malicious RDP brute forcing is detected. This effectively severs the attacker’s connection to the network, thus preventing the rest of the attack from ever taking place.
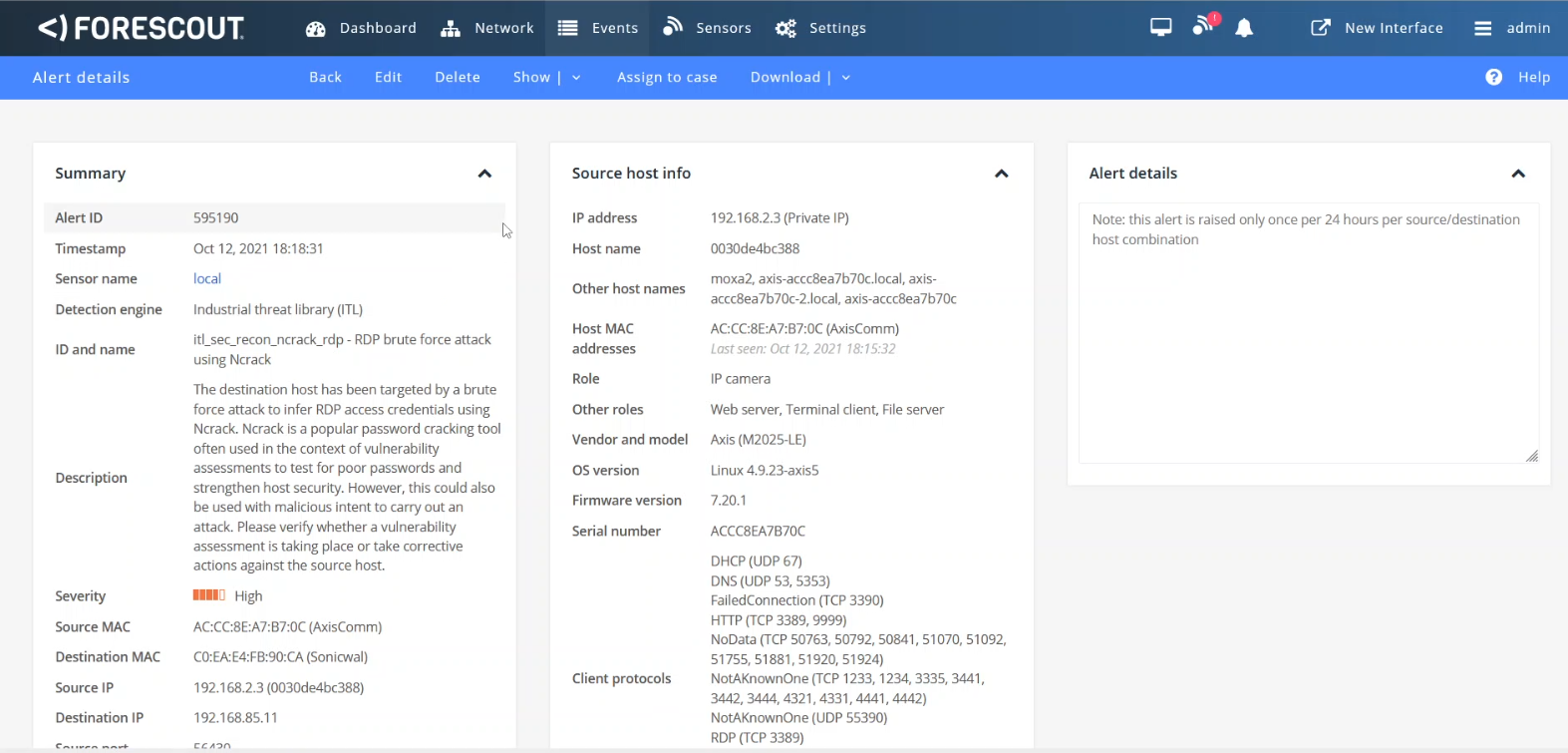
Figure 4 – An eyeInspect alert for the RDP bruteforcing attack from the IP camera to the NVR workstation
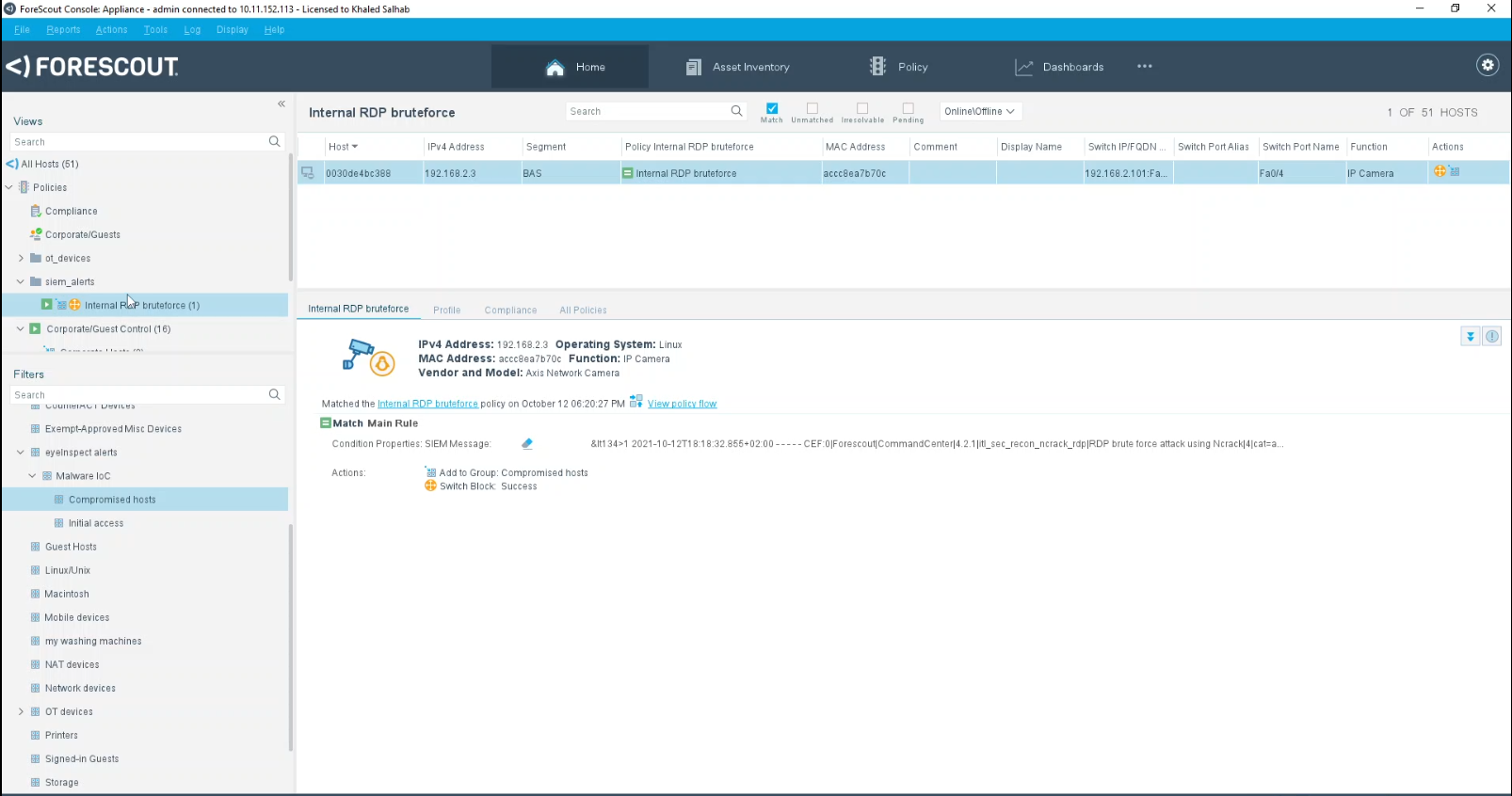
Figure 5 – An eyeSight policy to block the IP camera on the network switch once the malicious RDP brute forcing is detected
Lessons learned from Ryuk
Sophisticated ransomware attacks can take healthcare organizations out of action for weeks or even months, as we saw beginning in 2020 with a series of high-profile Ryuk attacks on hospitals. Take this deep dive into defenses based on Ryuk that you can implement now.