Identifying and Protecting Devices Vulnerable to Ripple20
Executive summary
- A set of 19 vulnerabilities, collectively called Ripple20, affecting the widely used Treck embedded IP stack, have been disclosed by the cybersecurity research company JSOF. Four of the vulnerabilities have a critical CVSS score, with impact including Remote Code Execution and Exposure of Sensitive Information.
- The vulnerabilities potentially impact tens of millions of devices across over 50 vendors, exposing a very complex supply chain for IoT devices. An IP stack is a basic connectivity software component used in every connected device. Essentially, in the IoT world, there is no public bill of materials that allow users and organizations to know what components are part of the devices they use. Meanwhile, these components can cause significant cybersecurity risks.
- Forescout Research Labs partnered with JSOF using data from our unique Device Cloud, a knowledgebase of more than 12 million devices, to identify dozens of potentially affected vendors. We analyzed data from more than 90,000 potentially vulnerable devices from over 50 vendors embedding Treck into their IoT and OT products. Examples of affected devices include infusion pumps used in hospitals, UPS (uninterruptible power supply) systems used in data centers and video conferencing systems used in enterprises.
- Treck issued a confidential security advisory and patch to its customers in March. We believe major vendors will have a patch available, but the difficulty of patching a device will depend on whether it receives automatic updates or whether it is mission-critical and cannot have downtime. Some small vendors or those that are already out of business may not issue patches, which means some devices probably cannot be patched.
- Forescout solutions can help organizations manage the remediation process by:
- Discovering and creating an inventory of affected devices to identify the risk surface, enforce mitigating controls and then prioritize patch updates
- Segmenting, isolating and controlling network access for vulnerable devices to mitigate risk
- Alerting security and operations teams when attacks exploiting these vulnerabilities occur in their networks
- Forescout will continue to monitor the evolving situation as it relates to these vulnerabilities and their impact, and will provide ongoing updates and best practice recommendations to our customers and the community.
Introduction – what is Ripple20?
On June 16, 2020, a set of 19 vulnerabilities, collectively called Ripple20, affecting the Treck embedded IP stack were publicly disclosed by JSOF.
Treck is used by over 50 vendors and millions of devices, including mission-critical devices for healthcare, data centers and critical infrastructure. Four of the issues discovered have a critical CVSSv3 rating, and at least two can lead to Remote Code Execution – essentially, full control of a targeted device.
Most of the issues relate to the implementation of the TCP/IP stack, which means they do not depend on a specific application, and the adversary only needs network access to the targeted device to leverage the vulnerabilities and take control of the device.Table 1 presents a summary of the vulnerabilities.
Table 1 – Summary of the vulnerabilities
The role of Forescout in the disclosure process
The vulnerabilities were first discovered by JSOF at the end of 2019 and disclosed to vendors beginning in February 2020, following industry best practices for coordinated vulnerability disclosure. The disclosure process included multiple coordination agencies, such as the DHS-CISA and the JPCERT. The process is ongoing as more vendors continue to confirm that their products are vulnerable and new vulnerable vendors are discovered. During this process, JSOF partnered with Forescout Research Labs to identify more affected vendors and devices.
This innovative approach to vulnerability disclosure, involving another cybersecurity vendor to identify vulnerable devices, was necessary because Treck is a basic connectivity component used by a range of device vendors in many different ways. For instance, the stack can be used with or without a real-time operating system, is highly configurable and is licensed under different names (For instance, Elmic commercializes the stack for the Asian market using the name KASAGO).
Vendors usually do not advertise that they use this particular IP stack, just as they rarely advertise the many other software and hardware components that go into their devices. Essentially, in the IoT world, there is no public bill of materials that allow users and organizations to know the components that are part of the devices they use.
To complicate matters further, the supply chain for IoT devices can be very long. Between a software component such as Treck and an end-user device, there can be a convoluted network of ODMs, OEMs, system integrators and white-label products.
Although Treck has contacted their immediate customers, there is still a long tail of potentially affected vendors and devices to be identified (customers of customers of Treck and so on). Forescout Research Labs used Forescout’s Device Cloud, a unique data lake with information from more than 12 million devices categorized in more than 150 device types, to identify potentially impacted vendors and devices. Using the Device Cloud, we were able to identify characteristic network signatures of Treck in close to 30 potentially affected vendors.
Affected devices and vendors
Treck is a widely deployed embedded IP stack used by companies such as HP, Intel, Schneider Electric, DIGI and many others to create products that range from home and enterprise printers to Industrial Control Systems (ICS) and healthcare equipment.
To further identify and classify the impacted devices, we analyzed the Forescout Device Cloud to see how many and what kind of devices run Treck. Identifying devices running Treck is not easy, as discussed above. To do so, we used a combination of network signatures provided by JSOF based on DHCP and TCP/IP fingerprints and post-processing to eliminate potential false positives. Therefore, all the numbers below are a lower bound of the actual number of devices that may be running Treck.
Table 2 shows a breakdown of the number of devices matching Treck signatures per vertical. More than 90,000 devices were found running the Treck embedded IP stack, with Healthcare, Retail, and Manufacturing being the most impacted verticals.
Table 2 – Population devices matching Treck signatures in Forescout Device Cloud: Top 5 verticals
The most common device types running Treck include infusion pumps, printers, UPS systems, networking equipment, Point of Sale devices, IP cameras, video conferencing systems, building automation devices and ICS devices.
Impact and exposure
To exploit Ripple20 vulnerabilities, an attacker needs a direct connection to an affected device or a routed path to internal networks. This means devices directly connected to the internet are those most at risk. An attacker could target these devices first, compromise them and move laterally within the network to access or infect other devices.
As an example of the impact of these vulnerabilities, a series of Shodan searches for 37 specific device models from 18 vendors (including printers, IP cameras and video conferencing systems, networking equipment and ICS devices) reveals there are around 15,000 internet-connected instances of these affected devices that could potentially be directly compromised by anybody on the internet.
Figure 3 shows the category breakdown for the example of affected devices found on Shodan. Figure 4 shows more details about affected HP LaserJet printers found on Shodan. Figure 5 shows some example screens of these devices seen online.
Figure 3 – Examples of internet-connected affected devices found on Shodan
Figure 4 – Instances of HP LaserJet printers on Shodan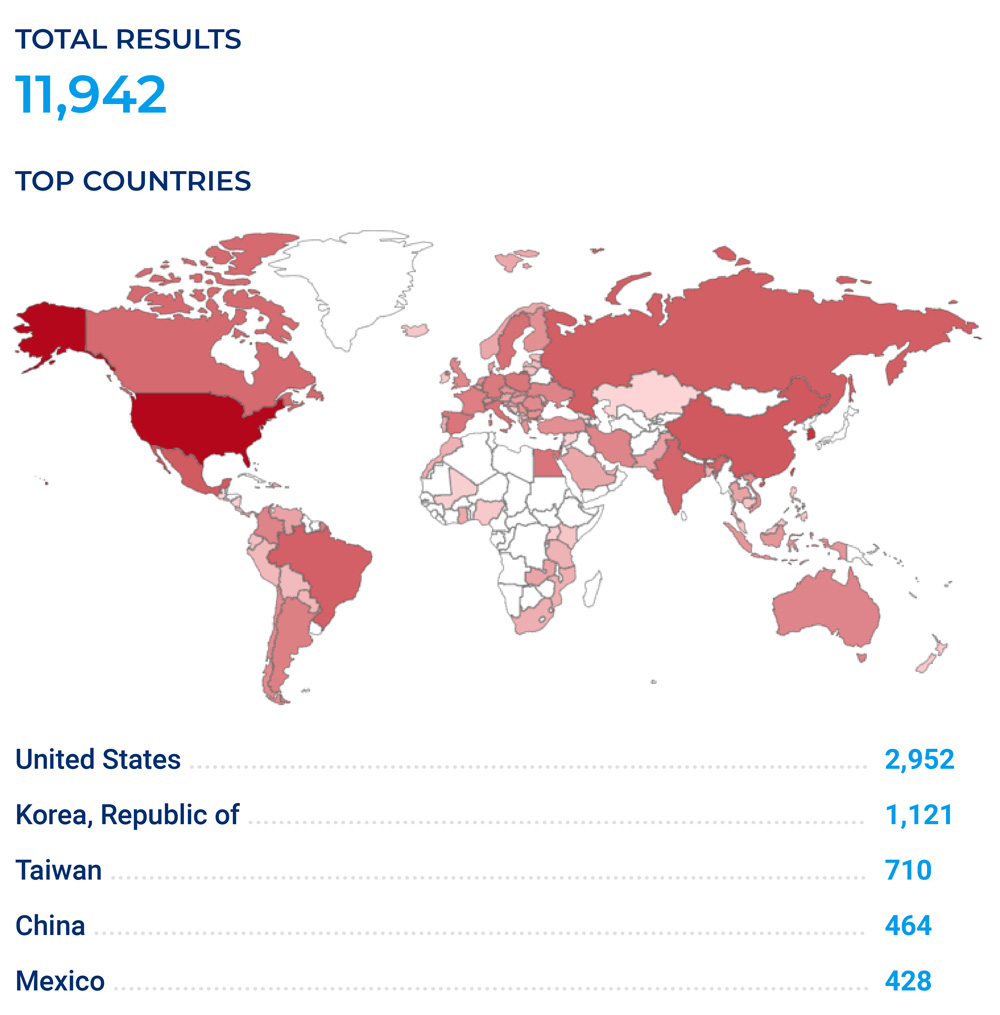
Figure 5 – Example configuration screen of an internet-connected affected printer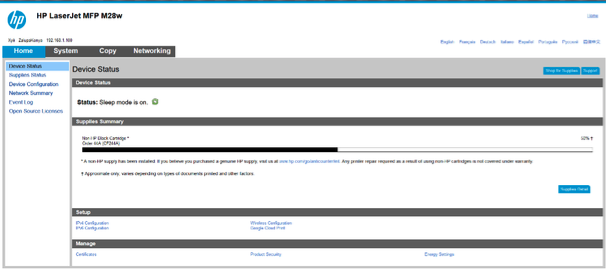
Notice that these numbers are based on only a few vendors and models that are known to be vulnerable and that some of the most popular devices such as infusion pumps and point of sale are not mentioned since they are not usually directly connected to the internet. As mentioned in the beginning of this post, the actual number of affected devices is likely in the tens of millions.
This means mitigation actions like identifying the vulnerable system versions to prioritize patch updates and further isolating them with segmentation techniques need to occur as soon as possible.
Recommended mitigation
Complete protection from Ripple20 requires patching devices running the vulnerable version of the IP stack. However, this is not as easy as it sounds because:
- Devices with embedded systems are notoriously difficult to manage and update, since traditional endpoint agents cannot be installed, and updates usually require a firmware reflash.
- Many of the affected devices are part of critical systems and infrastructure that make patching complicated.
- Patches must be issued by the final vendors of a device. Certain patches might not be available yet or may never become available since some vendors are not active anymore.
For the reasons above, we recommend the following mitigation strategy using Forescout products:
- Discover and inventory devices running Treck with Forescout eyeSight and SilentDefense to understand your risk surface and prioritize mitigation. Forescout has released a Security Policy Template (SPT) for eyeSight that detects and flags the characteristic network signatures of devices using Treck.
- Enforce segmentation controls and proper network hygiene to mitigate the risk from vulnerable devices using eyeSegment and/or eyeControl. Restrict external communication paths, and isolate or contain vulnerable devices in zones as a mitigating control if they cannot be patched or until such time they can be patched.
- Monitor progressive patches released by affected device vendors and devise a remediation plan for your vulnerable asset inventory balancing business risk and business continuity requirements.
- For OT environments, leverage the capabilities of SilentDefense to:
- Spot problematic network communications with SilentDefense LAN CP.
- Devise a remediation plan with SilentDefense Asset Inventory and Reporting.
- Establish out-of-the box protection by ensuring the SilentDefense Malformed Packet Detection engine is enabled and enhance the protection with the SD script released today. The SD script has custom detection for the most critical vulnerabilities, including CVE-2020-11896, CVE-2020-11897, CVE-2020-11898, CVE-2020-11901, CVE-2020-11903, CVE-2020-11909, CVE-2020-11910, and CVE-2020-11911.
- Use SilentDefense intrusion detection alerts to initialize remediation actions such as segmenting or updating devices.
- Leverage Forescout’s extensive integration portfolio to orchestrate risk mitigation and automate response across your entire IT and security stack.
For more information on how to use Forescout products for Ripple20 risk mitigation, please refer to: