Updates:
January 26, 2021: Forescout has found no evidence of compromise by SuperNova or Raindrop
December 19, 2020: Forescout has temporarily disabled product downloads as a precautionary measure.
JANUARY 26 UPDATE
In light of recent public disclosures by Symantec and other security agencies, we have conducted further investigations in this fluid and ongoing situation.
Forescout has reviewed the recent disclosures around the additional vulnerabilities found in context of SolarWinds, named Raindrop and SuperNova. As previously stated, Forescout does not currently run any versions of SolarWinds Orion software.
Prior to the SolarWinds revelations, Forescout previously ran SolarWinds version 2018.2 and 2016.1.5300, which may be vulnerable according to the SolarWinds security advisory. We conducted further investigations and analyzed our logs, backups and the potentially vulnerable SolarWinds files and found no evidence that Forescout has been compromised by SuperNova or Raindrop.
We will continue to provide updates as the situation dictates.
JANUARY 6 UPDATE
Forescout recently disabled product downloads for Per-Appliance Licensing (PAL) customers from the Product Updates Portal in order to conduct a precautionary security review following the SolarWinds incident. Following the review and validation of our software delivery systems, Forescout is now re-enabling product downloads for PAL customers through the Forescout Customer Support Portal.
PAL customers will have access to all product downloads starting from platform version 8.0 (CounterACT). Downloads for CounterACT version 7.0 are currently unavailable from the site. If you need to access these downloads, contact Forescout Customer Care.
Our security teams continue to conduct precautionary security reviews in order to protect our customers. These reviews are being taken in an abundance of caution as Forescout does not currently use SolarWinds software and has never used the known affected versions of the SolarWinds products within our environment.
DECEMBER 24 UPDATE
After an extensive validation of the integrity of our product binaries and review of our software delivery chain, we are re-enabling product downloads from our Flexx customer entitlement portal. Other product download mechanisms will be enabled at a later phase.
While we do not currently use SolarWinds software and have never used the affected versions in our environments, we felt this was a precautionary step we could take to validate our systems and protect our customers. We will continue to provide additional updates on this blog.
DECEMBER 22 UPDATE
Forescout has released updated policy templates and scripts to help customers detect vulnerable software versions and presence of SUNBURST malware.
eyeSight Security Policy Template for Vulnerability Detection
Customers can now leverage a new Security Policy Template (SPT) dedicated to this issue, that evaluates Windows endpoints to identify vulnerable systems. To deploy this policy, customers can download SPT Module version 20.0.13 here, the Help File here, and the Release Notes here.
This policy uses passive and/or active inspection methods to evaluate endpoints. Vulnerability detection is based on the presence of “SUNBURST” malware and other suspicious SolarWinds applications and services, related open ports and other factors. This vulnerability is tracked as FireEye UNC2452. The SPT also detects CVE 2019-9546. See the full advisory here.
Recommendations for policy deployment:
- To allow detailed inspection of SolarWinds servers, we strongly recommend ensuring they can be managed using Remote Inspection or SecureConnector to run in-depth inspection
- As information about this exploit develops, modify your policies to search for other application installation locations.
Endpoints evaluated as Vulnerable or Potentially Vulnerable are labeled and assigned to Malware sub-groups for further policy actions. In addition, the policy populates a set of new Inventory views:
|
Vulnerable devices (SUNBURST) |
Known SUNBURST malware components detected. |
|
Vulnerable devices (other) |
Evidence of compromised SolarWinds components. |
|
End of Life |
SolarWinds applications that are no longer supported were detected. These builds are still vulnerable but may not be patched. |
|
Potentially Vulnerable devices (by version) |
Vulnerable SolarWinds application builds detected. |
|
Not Vulnerable |
Windows environment and/or SolarWinds applications that are not vulnerable. Non-Windows endpoints are cleared to this group. |
|
Potentially Vulnerable devices (high certainty) |
Open communication ports and/or SolarWinds services associated with this exploit were detected. |
|
Potentially Vulnerable devices (medium certainty) |
|
|
Offline |
Endpoint not available for evaluation. |
|
Other |
Endpoint could not be assigned to other groups, or vulnerability could not be evaluated. |
Recommended remediation and risk mitigation actions:
- On endpoints with SolarWinds applications, install patches or hotfixes provided by SolarWinds and/or upgrade to protected builds.
- Review endpoints with SolarWinds services or open ports associated with this exploit to see if these artifacts are legitimately present.
- Optional Virtual Firewall actions in the policy template can be enabled to provide an initial response upon detection.
- Customize your response with other eyeControl actions and eyeSegment policies.
Segmenting Vulnerable Assets with eyeSegment
Segmentation can limit the risk of remote code execution, denial of service attacks, and exposure of sensitive information from this vulnerability. Forescout eyeSegment can visualize how the groups created in Forescout eyeSight (such as DB Admin, IP Camera, SolarWinds Orion) are communicating with each other.
Administrators can then create policies by pivoting off production flows or following segmentation best practices such as:
- DB Admin can leverage SSH to connect to DB servers but not to other workstations
- IP Cameras can only communicate with an NVR and nothing else
- SolarWinds Orion can leverage RDP to workstations, but not to critical services
eyeSegment example showing SolarWinds Orion communications with Active Directory:
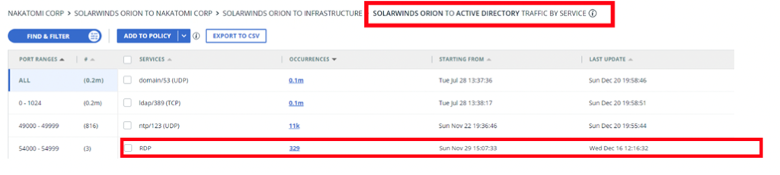
Once eyeSegment policies are in place, they can be run in simulation/monitoring mode to alert on violations, or enforcement mode by hardening ACLs, firewall rules, SGTs, etc.
Detecting SUNBURST Malware in OT Networks with eyeInspect (formerly SilentDefense)
Forescout has released an eyeInspect script that detects the presence of the SUNBURST malware by monitoring network traffic. We recommend installing this on your sensors for improved malware detection. Capabilities include:
- Detection of the SUNBURST backdoor communications related to the SolarWinds supply chain cyberattack
- Detection of the Cobalt Strike Beacon communications related to the SolarWinds supply chain cyberattack
Additionally, as part of regular and on-going updates to our Indicators of Compromise (IOC) database, we will be adding IOCs in our next update to detect SUNBURST threats scrutinizing multiple sources of information for maximum coverage. eyeInspect can also automatically scan historical network logs to look for new SUNBURST IOCs utilizing the Forensic Time Machine function. This is recommended as looking at past logs can, in some cases, identify an attacker’s post compromise activity to evade detection.
To get the latest detection scripts, documentation and product updates, please contact Forescout Customer Care.
DECEMBER 19 UPDATE
Given the widespread nature of the SolarWinds breach and complex software supply chains, Forescout is temporarily disabling product downloads from our customer portals. This action is being taken in an abundance of caution as Forescout does not currently use SolarWinds software and has never used the known affected versions of the SolarWinds products within our environment. Customers who need to urgently download product binaries should contact Forescout Customer Care.
On December 12, 2020, FireEye detailed a sophisticated supply chain attack that used SolarWinds Orion business software (versions 2019.4 to 2020.2 HF1) released between March and June 2020 to compromise networks. Since then, the Department of Homeland Security has issued Emergency Directive 21-01, informing agencies to take immediate action to mitigate this risk.
Our Commitment to Security
The event highlights the importance of our mission to help customers secure their most critical assets. A significant part of that is ensuring the highest level of cyber resilience and security for our products, corporate systems and customer data.
Our Information Technology team has completed a thorough review of all Forescout systems. Forescout does not currently use any SolarWinds software and has never used the known affected versions of the SolarWinds products within our environment.
Forescout’s Security Incident Response Team (SIRT) is taking additional actions including, but not limited to:
- Verifying system hygiene to include patching for all 17 CVEs noted in the FireEye report
- Configuring our Information Security tools to scan for all Indicators of Compromise (IOCs) for this attack and investigating any possible IOCs
- Performing a gap analysis comparing new malware, tools and tactics against existing countermeasures and applying mitigation to gaps found
- Reviewing historical log data to look for any indicators based on new IOCs
- Performing an in-depth review of our supply chain
Forescout is continually testing, updating and monitoring our own networks to maximize our security posture. We employ Forescout products as part of this effort to gain the same real-time visibility and control of all connected things on our networks as our customers.
Protecting Your Network
While information about this attack is still emerging, Forescout customers can immediately begin to identify and address vulnerable versions of the SolarWinds software inside their environment.
Forescout eyeSight discovers and classifies every device on your network and can help identify vulnerable, misbehaving and unauthorized devices. This includes identifying the known affected SolarWinds systems within your environment. Using Forescout, you can then isolate or contain the devices and apply immediate risk mitigation actions to limit your exposure.
Existing Forescout customers can learn more about about how to use Forescout policies to identify at-risk SolarWinds systems via our customer support portal.
Looking Ahead
Our IT security and threat research teams are continuing to monitor the situation closely. We will provide updates as the situation evolves and teams are available to answer any questions you might have.