On December 8th, Forescout Research Labs publicly disclosed the AMNESIA:33 set of vulnerabilities, affecting four open-source TCP/IP stacks. The response from the community has been overwhelming.
Upon identifying more than 150 component and device vendors that could be using the affected stacks, we knew that these bugs have far-reaching implications. However, we did not expect that, after the public disclosure, even more vendors would ask us for help in understanding whether their products are vulnerable.
This is one more example that assessing the reach of vulnerabilities in TCP/IP stacks and identifying affected devices is very challenging since the use of the stacks is rarely described in device documentation or clearly advertised.
In addition to the vendors, we have also received requests from network operators and CERTs around the world, asking for help in detecting vulnerable devices.
Therefore, today we decided to release an open-source script that detects network characteristics indicating the use of the four vulnerable TCP/IP stacks. This script uses detection capabilities provided to Forescout customers on day one as part of a Security Policy Template (SPT). Please note, the script does not rely on extra features enabled by the Forescout platform, such as device classification, passive monitoring and infrastructure to run it at scale on very large networks.
The script is available to be freely used by any interested party, and full documentation is available on GitHub. Below, we briefly discuss how it works and call on the security community to help us improve it.
How does it work?
The script identifies the use of four TCP/IP stacks (uIP, picoTCP, FNET and Nut/Net) on a target device (or set of target devices) via three active fingerprinting methods:
- ICMP probing: the script performs a malformed ICMPv4 echo request and checks for characteristics of the reply, including changes in the Time-to-Live (TTL) value and specific payload content, which varies per stack.
- TCP options signatures: the script sends a TCP SYN packet and monitors the TCP SYN-ACK response for the format of the TCP options field. Each stack replies with different values for the options, such as a Maximum Segment Size (MSS) and window scale.
- TCP Urgent flag handling: the script sends a TCP packet with the Urgent flag set and monitors the response. Each stack replies with a different set of TCP flags and a different TCP Window size value.
Based on which and how many of the methods above are matched to a stack, the script indicates the use of that stack with a level of confidence, as shown in the image below.
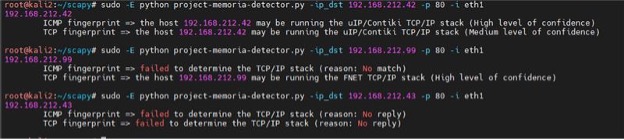
Figure 1 – Example output of the script
The level of confidence is a reminder that the script can still result in false positive (i.e., wrongly indicating the use of a stack) and false negative (i.e., missing the actual use of a stack) matches.
Although the script has been tested with the four stacks affected by AMNESIA:33 in a lab environment, we cannot guarantee its use to be safe against every possible device. Malformed ICMP packets, for instance, could crash a device that is running a different stack. Therefore, we do not recommend using it directly in live environments with mission-critical devices (such as hospitals with patient-connected devices or safety-critical industrial control systems). An ideal approach is to test devices in a lab setting or during a maintenance window.
Contributing to the community
As we described in the AMNESIA:33 research report, this study is part of a larger initiative called Project Memoria, which has the goal of understanding vulnerabilities on TCP/IP stacks and how to mitigate them. The release of this script is part of the latter objective.
We intend to update this script with detections for other stacks in the future as we disclose additional vulnerabilities. We would also like to receive contributions from the community, either for improving detection of the currently vulnerable stacks or for detecting other stacks. To enable these contributions, the script is licensed as GPLv3.
Download and use the Project Memoria TCP/IP Detector script today, then please let us know how it works within your environment and how we can improve it. Also, feel free to send results of potentially vulnerable devices to [email protected], so we can approach the affected vendor identification and disclosure as a community effort.