The title for the article was not accidentally put in all CAPS; I’m shouting it! In this article, we will focus on learning every MAC and IP address on your network as quickly as possible. This is the foundation for the real-time visibility that CounterACT provides. Like all foundations, there is nothing “sexy” about it. It would be nice to skip it and get to the fun part, but the foundation is critically important and will have a profound impact on the effectiveness of your CounterACT implementation.
CounterACT discovers endpoints in several ways, but the authoritative method is through querying the CAM and ARP tables of switches, wireless access points/controllers and routers. Ensuring that ALL these network devices are being queried by CounterACT is very important because it is the ONLY way to have full visibility of everything on your network. SNMP Traps can speed discovery of newly connected devices, but the confidence comes from the CAM and ARP tables.
If you have difficulties with identifying newly connected devices in CounterACT, the first place to look is the switch, wireless access point/controller and router integrations.. The policy in the screen shot below is a modified version of the PS Switch Integration Policy and EVERY CounterACT implementation should have a similar policy in place (the XML export of this policy is attached). It is possibly THE most important policy in ensuring that you have 100 percent visibility of all devices connected to your network.
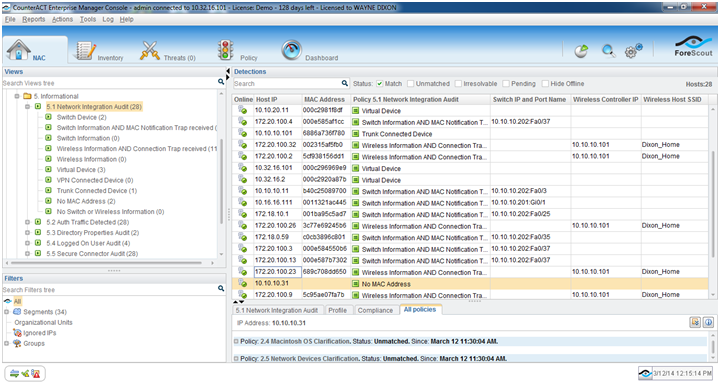
The policy is designed to illustrate any areas on your network where you do not have complete visibility. The following is a breakdown of what the sub-rules are showing:
-
Switch Device – Identifies devices that are switch management interfaces. No further action required.
-
Switch Information AND MAC Notification Trap received – Identifies devices where switch information is present and SNMP notification traps have been received. No further action required.
-
Switch Information – Identifies devices where switch information is present, but SNMP notification traps have NOT been received. This can either indicate devices that have been connected for a long time, or areas where SNMP notification traps are not properly configured. You’ll want to examine these devices for gaps in SNMP Trap coverage, as gaps could be leading to slow device discovery.
-
Wireless Information and Connection Trap received – Identifies devices where wireless information is present and SNMP connection traps have been received. No further action required.
-
Wireless Information – Identifies devices where wireless information is present, but SNMP connection traps have NOT been received. This can either indicate that devices have been connected for a long time, or areas where SNMP connection traps are not properly configured. You’ll want to examine these devices for gaps in SNMP Trap coverage, as gaps could be leading to slow device discovery.
-
Virtual Device – Identifies devices with a VMware Virtual NIC. These devices will legitimately have limited switch and wireless information. No further action required.
-
VPN Connected Device – Identifies devices connected to VPN segments. These devices will legitimately have limited switch and wireless information. No further action required.
-
Trunk Connected Device – Identified devices connected to a trunk port (Requires attached “acl_candidate.sh” script). CounterACT is aware of trunk port connected devices but does not show switch information as it assumes there is an Access switch downstream. While CounterACT does not show any switch information for these devices, if the option to “Block hosts learned via downstream devices” is enabled in the switch configurations, CounterACT will show the “trunk” location for this attribute. You’ll want to examine these devices. Even though there are legitimate cases where a device will connect directly to a trunk port, this could also indicate a gap in switch coverage.
-
No MAC address – Identifies devices where the MAC address has not been learned. You’ll want to examine these devices as they could indicate gaps in switch/WAP/router coverage.
-
No Switch Information – Identifies devices where no network information has been learned. You’ll want to examine these devices as they could indicate gaps in switch/WAP/router coverage.
Leveraging this policy correctly will allow you to effectively identify and remediate any visibility gaps that currently exist. Closing these gaps is a key step in achieving the real-time situation awareness that you purchased CounterACT for in the first place. If you have any questions, please leave comments below. Happy CounterACTing!!!