What Is AMNESIA:33?
AMNESIA:33 is a set of 33 vulnerabilities impacting four open source TCP/IP stacks (uIP, PicoTCP, FNET, and Nut/Net), which collectively serve as the foundational connectivity components of millions of devices around the world.
The details of these vulnerabilities are described in our technical report and will be presented at Black Hat Europe 2020, but can be summarized as follows:
- AMNESIA:33 affects seven different components of the stacks (DNS, IPv6, IPv4, TCP, ICMP, LLMNR and mDNS). Two vulnerabilities in AMNESIA:33 only affect 6LoWPAN wireless devices.
- AMNESIA:33 has four categories of potential impact: remote code execution (RCE), denial of service (DoS via crash or infinite loop), information leak (infoleak) and DNS cache poisoning. Four of the vulnerabilities allow for remote code execution.
Generally, these vulnerabilities can be exploited to take full control of a target device (RCE), impair its functionality (DoS), obtain potentially sensitive information (infoleak) or inject malicious DNS records to point a device to an attacker-controlled domain (DNS cache poisoning). However, different devices may be affected differently by the vulnerabilities depending on how a stack is used.
We estimate that more than 150 vendors and millions of devices are likely vulnerable to AMNESIA:33. We have shared our findings with coordinating agencies (such as the ICS-CERT and the CERT/CC), which have contacted the identified vendors. Some vendors have already confirmed the vulnerabilities and issued their patches, but several are still investigating.
The widespread nature of these vulnerabilities means that many organizations around the world may be affected by AMNESIA:33. Organizations that fail to mitigate this risk are leaving open doors for attackers in IT, OT, and IoT devices across their organization.
The AMNESIA:33 vulnerabilities were discovered by Forescout Research Labs as part of Project Memoria, an initiative that aims at providing the cybersecurity community with the largest study on the security of TCP/IP stacks.
Impact
There has been a lot of prominent research conducted on TCP/IP stacks recently, including studies that have resulted in the discoveries of the Ripple20 vulnerabilities on the Treck TCP/IP stack that affected millions of devices and the Bad Neighbor vulnerability on the ICMPv6 component of the Windows TCP/IP stack. This previous work has highlighted the importance of TCP/IP stacks and their value as targets for attackers.
Exploiting the AMNESIA:33 vulnerabilities could allow an attacker to take control of a device, thus using it as an entry point on a network (for Internet-connected devices), as a pivot point for lateral movement, as a persistence point on the target network or as the final target of an attack.
For enterprise organizations, this means they are at increased risk of having their network compromised or having malicious actors undermining their business continuity. For consumers, this means that their IoT devices may be used as part of large attack campaigns, such as botnets, without them being aware.
AMNESIA:33 could affect both asset vendors and asset owners. For asset vendors, the risk is to inadvertently produce and ship large numbers of devices that contain the faulty stacks. This can happen because open source TCP/IP stacks are so deep into the supply chain that it is not unthinkable that the producer of an end device is unaware of their presence. For asset owners, the risk is to have their network targeted by attackers because of one or more vulnerable devices exposed.
It is difficult to assess the full impact of AMNESIA:33 because the vulnerable stacks are widely spread (across diverse IoT, OT and IT devices in different verticals), highly modular (with several combinations of enabled features and settings) and often incorporated in embedded components, such as systems-on-a-chip (SoCs), that are later used by device manufacturers. For the same reasons, these vulnerabilities tend to be very hard to eradicate.
Figure 1 shows a division, in macro categories, of the potentially vulnerable device models we identified. The largest category is IoT devices, both enterprise and consumer, which includes devices such as cameras, environmental sensors (e.g., temperature, humidity), smart lights, smart plugs, barcode readers, specialized printers, and audio systems for retail. IoT is followed by OT equipment for Building Automation Systems, which includes devices such as physical access controls, fire and smoke alarms, energy meters, and HVAC systems. Then we have OT equipment for Industrial Control Systems, which includes devices such as RTUs, protocol gateways and serial-to-Ethernet gateways. Lastly is IT, which includes devices such as printers, switches and wireless access points.
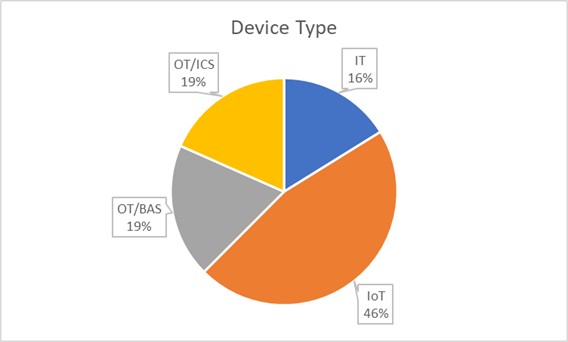
Figure 1 – Device type distribution
Estimating the number of existing individual vulnerable device units is difficult because some devices, such as OT equipment, are known to be very popular but are rarely found online since they are not supposed to be internet-connected. Besides, embedded components are not always advertised in documentation or in network traffic, although it’s important to note that popular SoCs are shipped by manufacturers on the order of millions of units per quarter.
Recommended Mitigation
Due to the complexity of identifying and patching vulnerable devices, vulnerability management for TCP/IP stacks is becoming a challenge for the security community. We recommend adopting solutions that provide granular device visibility and allow for monitoring network communications and isolating vulnerable devices or network segments to manage the risk posed by these vulnerabilities.
More specifically, we recommend:
- Assess your risk: Organizations should perform a thorough risk assessment before deploying mitigations. This includes identifying potentially vulnerable devices, their business context and criticality, and their communication pathways and internet exposure. Based on this assessment, determine what level of mitigation is required.
- Patch when possible: The best mitigation is to identify and patch vulnerable devices. However, this is easier said than done because:
- Patches may not be available for an embedded component from the IoT or OT device vendor
- Patching an embedded component directly may void the device manufacturer’s warranty
- A device may be part of a mission-critical function or high-availability business operation and may not be patchable until a scheduled maintenance window at a future time.
- Segment to mitigate risk: For IoT and OT devices that cannot be patched, use segmentation to minimize their network exposure and likelihood of compromise, without impacting mission-critical functions or business operations. Segmentation and zoning also limit the blast radius and business impact if a vulnerable device becomes compromised.
- Disable or block IPv6 traffic: Since several vulnerabilities in AMNESIA:33 are related to IPv6 components, disable or block IPv6 traffic whenever it is not needed in the network.
- Rely on internal DNS servers: Configure devices to rely on internal DNS servers whenever possible and closely monitor external DNS traffic, as several vulnerabilities in AMNESIA:33 are related to DNS clients, which require a malicious DNS server to reply with malicious packets.
- Monitor for malformed packets: Monitor all network traffic for malformed packets (for instance, those having non-conforming field lengths or failing checksums) that try to exploit known vulnerabilities or possible zero days, since many vulnerabilities are related to IPv4 and other standard components of stacks. Anomalous and malformed IP traffic should be blocked or, at a minimum, network operators should be alerted to its presence.
Forescout can help in multiple ways to reduce the risk associated with AMNESIA:33 vulnerabilities. It is advisable to follow defense-in-depth principles and adhere to as many of these risk-mitigation best practices as possible.
- Know what is on your network: Accurate identification and inventory of all devices is foundational for risk assessment and mitigation. Use Forescout to get a three-dimensional view (Device Type, OS & Version, Vendor & Model) of all network connected devices, and identify all the unknown and unauthorized devices on the network. To exploit AMNESIA:33 vulnerabilities, an attacker needs a communication path to a vulnerable device or a routed path to an internal network. Unknown and unauthorized devices may try to compromise vulnerable devices. It is imperative to use a platform that can block all the unauthorized devices from accessing the corporate network, specifically the Forescout platform.
- Assess your risk: Once you have the foundational visibility, enterprise customers can use Forescout’s newly released Security Policy Template to detect potentially vulnerable devices by flagging the characteristic network signatures of devices using uIP, Nut/Net, FNET and picoTCP.
- Patch when possible: For devices that have available patches and that can be patched outside of maintenance windows, Forescout can help orchestrate remediation workflows with other IT and security tools.
- Segment to mitigate risk: Devices directly connected to the internet are at most risk from AMNESIA:33. Forescout provides network flow mapping of existing communications. This is not just a prerequisite for designing effective segmentation zones, it also provides a baseline understanding of external and internet-facing communication paths. This can help identify unintended/anomalous external communications so appropriate segmentation controls can be enforced for mitigating risk. Once the vulnerable devices have been identified, logically group those assets to form the basis for segmentation-based mitigation. It is important to take the business function of the asset into consideration while logically grouping devices, as the mitigation actions on a printer may be different than those for a business-critical IoT device. At that point, when logically grouping, you can detect and block anomalous IP traffic and apply segmentation controls to decrease the communications allowed to or from these potentially vulnerable devices, thereby limiting the likelihood of compromise and the blast radius if a compromise occurs.
- Enforce security compliance: Use Forescout to continuously monitor and enforce security compliance for all connected devices in your Enterprise of Things. Noncompliant devices (devices with weak/default credentials, unpatched, legacy OS, etc.) are often the primary targets for an attacker.
- Monitor network communications: In addition to immediately reducing risk by taking mitigation actions, customers should continuously monitor the traffic to and from high-risk devices. Forescout monitors the ongoing traffic and behavior of the device, so when anomalous traffic flows are detected, response actions or more stringent controls can be enforced. For OT networks, Forescout has released two Forescout eyeInspect scripts that detect active exploitation of AMNESIA:33 vulnerabilities, so critical alerts/mitigation steps can take place once an active attack is detected.
For more information about AMNESIA:33, read the technical report from Forescout Research Labs and visit our AMNESIA:33 resources page. You can also get up-to-date information about impacted vendors and devices from these agencies:
- ICS-CERT advisory (icsa-20-343-01)
- CERT Coordination Center advisory
- BSI (German Federal Office for Information Security) statement
- JPCERT advisory