You may have noticed that Gartner analysts are actively promoting the research firm’s CARTA strategic approach for risk management and cybersecurity. As Gartner kicks off its series of Security and Risk Management Summits across Latin America, Europe, APAC and the Middle East in the coming weeks, Gartner analysts will most certainly amplify the need for CARTA, including why it’s fundamentally different than Zero Trust.
Both Gartner’s CARTA strategic approach and Forrester’s Zero Trust model offer new ways to think about reducing risk and improving cybersecurity, but they are remarkably similar in their outlooks. In fact, both frameworks require continuous device visibility and automated control, as well as orchestration capabilities to operationalize security and risk management across the growing vendor ecosystem. As I’ve written about Zero Trust in a previous blog, rather than detail the finer points that differentiate CARTA and Zero Trust (Forrester and Gartner are happy to do that), today we will define CARTA and introduce its fundamental concepts.
Why CARTA
Given the relentless pace of investment in security tools over the past decade, you may wonder why enterprises and government organizations haven’t solved all of their security problems and still need such an all-encompassing security framework. But let’s face it: Cybercriminals these days are wildly successful. The status quo simply isn’t working. Previously effective security and risk management approaches are unsuitable for rapid changes brought about by IP-connected data sharing and digital transformation. Some of these changes include:
- Hypergrowth of non-traditional devices and OSes—most of which are agentless
- Perimeter defenses no longer work—physical vendor access, phishing and insider credential abuse circumvent the perimeter every day
- Corporate device ownership has become irrelevant thanks to mobile computing, BYOD and IoT/OT devices showing up constantly on enterprise networks
- Point-in-time scans are old news—asset inventory and vulnerability assessment must occur continuously in real time
- Security silos add inefficiency and delays—too many tools to learn and use and too many manual processes to keep pace with growth and unyielding pressure from hackers
- One-time block/allow authentication methods miss the mark while impeding access to legitimate users
“One-time allow/deny gating for user authentication is as flawed as one-time allow/deny gating using signature-based antivirus protection.” 1
— Neil MacDonald, VP, Analyst, Gartner
CARTA defined
CARTA stands for Continuous Adaptive Risk and Trust Assessment. It builds upon Gartner’s Adaptive Security Architecture to shift security and risk management processes away from single allow/deny gating to more agile, context-aware and adaptive methods. The CARTA strategic approach:
- Requires continuous discovery, monitoring, assessment and risk prioritization
- Includes both adaptive attack and access protection
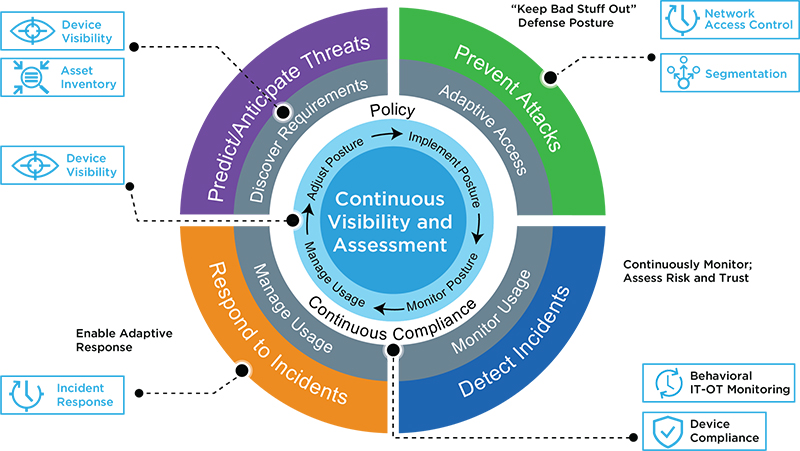
Caption: Continuous visibility and assessment are foundational capabilities of Gartner’s Adaptive Security Architecture and CARTA strategic approach.
Basic Precepts of Security at the Next Level
The CARTA strategic approach stipulates that effective risk and cybersecurity management require:
- 100% device visibility and automated control
- Continuous monitoring, assessment and remediation of cyber and operational risk
- Micro-segmentation to contain breaches and limit lateral movement/damage
- Technologies and products from multiple vendors
- New levels of multivendor orchestration and process/response automation
- Discovery, posture assessment and remediation/control of physical and virtual devices as well as cloud infrastructure and workloads
- Effective security management of agentless IoT devices and cyber-physical OT systems
What may not come as a surprise is the fact that these bullet points would fit nicely into a list of security must-haves based on Forrester’s Zero Trust Model. That’s how close Gartner and Forrester analysts are in their thinking.
Also not surprising: Forescout provides foundational capabilities to successfully implement Zero Trust security and the CARTA strategic approach.
To learn more, including how the Forescout platform adds value in each of CARTA’s seven strategic imperatives, read the Forescout White Paper: Continuous Visibility, Assessment and CARTA.
1 Neil MacDonald, Gartner Security and Risk Management Summit, June 2018