Multifactor Risk Scoring
How Reducing Your Cyber Attack Surface Starts with Risk
Vulnerability Prioritization
Cuts Through the Noise
Most security teams, overloaded by alerts and incident backlogs, are inundated by the growing number and types of devices they must manage, so how do you reduce your cyberattack surface? What is the best way to prioritize your vulnerabilities and maximize effort? How do you ensure your control Forescout offers an asset-centric approach to the problem, helping you create a proactive strategy to deal with your network’s vulnerability effectively and efficiently at scale.
Multifactor Risk Scoring gives your security operations center (SOC) the advantage of working on the vulnerabilities and exposure in your current security framework that misalign it from your desired compliance state. We bring you cyber asset management by comprehensively assessing device risk. Instead of working feverishly on volume, you work on criticality to your network.
As part of the Forescout Platform, Multifactor Risk Scoring works to further your efforts in assessing and governing your cyber assets with comprehensive risk profiles. Forescout’s goal is to provide a single point of control that leverages automation to help you remediate or mitigate your organization’s highest risk.
Challenges Impacting Your
Cyber Risk Awareness

Gaps in Visibility Assessment
- Devices are missed due to scan scheduling as assets come and go offline.
- Unmanaged devices (IoT, OT, IoMT, mobile) joining your network, both authorized and unauthorized.
- Broken or misconfigured software agents that are assumed to be running correctly.
Risk Calculation Based Only on CVE
- Security tools offer only one dimension of risk: common vulnerabilities and exposures (CVE). They lack asset configuration, behavior and exploitability information.
- IoT and OT devices often do not have associated vulnerability data.

Fragmented Security Tools
- Most security tools fail to encompass all the unique asset types that make up the network (IT, IoT, IoMT, and OT).
- Multiple security tools can lead to a longer mean time to response (MTTR).
How Multifactor Risk Scoring Works
An asset’s risk is calculated based on its configuration, function and behavior. A risk score is an aggregate number that you can quickly act on – or have Forescout’s policy engine automate remediation and mitigation policy actions.
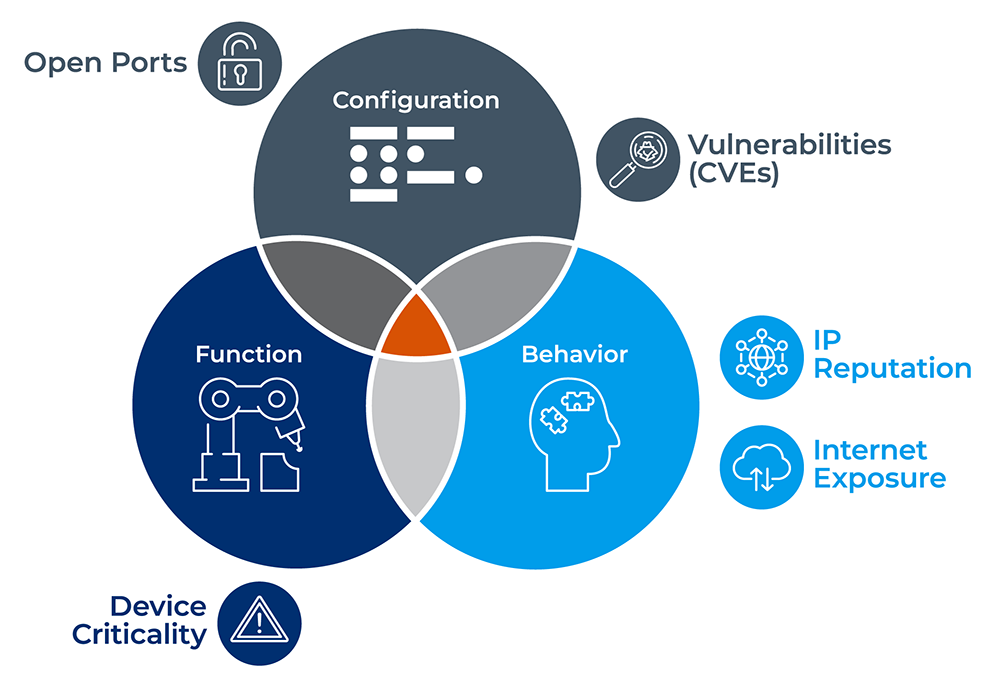
What Are the Indicators and Weighting Factors in Risk Scoring?
- Known vulnerabilities applicable to the device. This information comes from feeds, including integration with VA tools for managed device vulnerabilities.
- Exposed services and protocols for the devices.
- Inbound and outbound malicious traffic to devices (internet exposure).
- Device criticality: the potential impact to the organization if the device is compromised based on classification data.
Using Risk Scores to Achieve
Business Outcomes

Quickly Discover, Assess and Report Your Risk Posture
- Real-time inventory of all cyber assets, both managed and unmanaged
- High-fidelity asset classification with comprehensive risk profiling to show asset compliance

Prioritize Vulnerability Response
- Unique risk score drives the security governance of devices
- Initiate remediation and risk mitigation workflows in real time
- Understand the exploitability of your vulnerabilities

Automate Advanced Segmentation and Containment
- Craft policies that trigger an instant response to high-risk incidents saving precious time
- Contain threats to minimize blast radius and disruption to your network







