IoT Security
The State of IoT Security
The Enterprise of Things Security Report reveals trends, risks and opportunities from Vedere Labs’ analysis of 8+ million devices deployed across the financial services, government, healthcare, manufacturing and retail sectors. This assessment of the state of enterprise IoT cybersecurity includes:
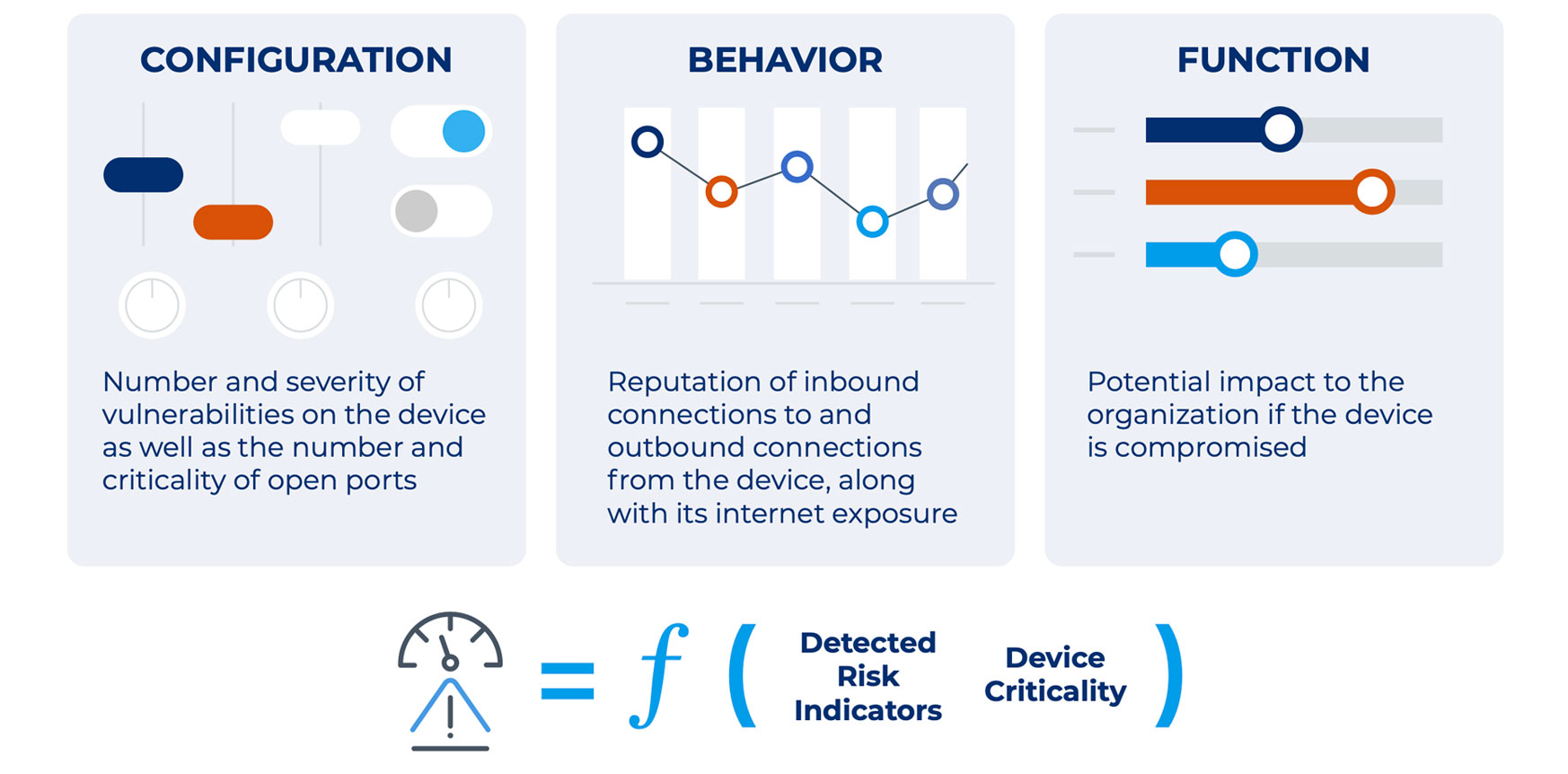
- A summary of the riskiest IoT device categories with vulnerabilities most often found in smart building systems, medical devices, networking equipment and VoIP phones
- The risks in desktop and laptop computers, with 30% to 35% of managed devices running unsupported Windows versions
- Other enterprise network security exposures, including services like Telnet, which were found extensively across the survey database.
Only Forescout can automate protection and mitigation of IoT device risk across your Enterprise of Things.

Gain complete device visibility
Real-time visibility and classification of every device enables Zero Trust control at enterprise scale.

Segment without disruption
Risky devices are contained in secure trust zones that enable critical operations to continue.