OT Security
Reduce operational and security risk in OT/ICS and SCADA environments
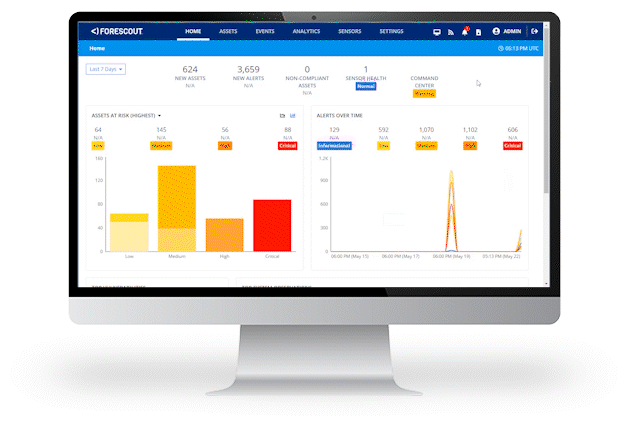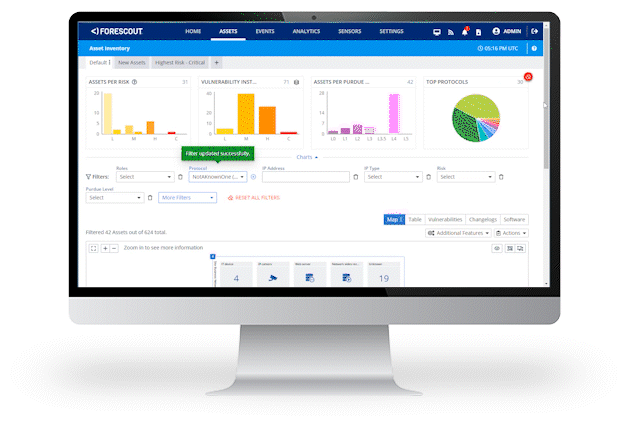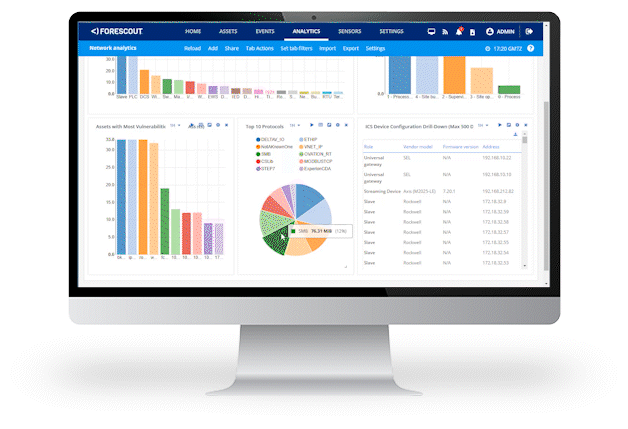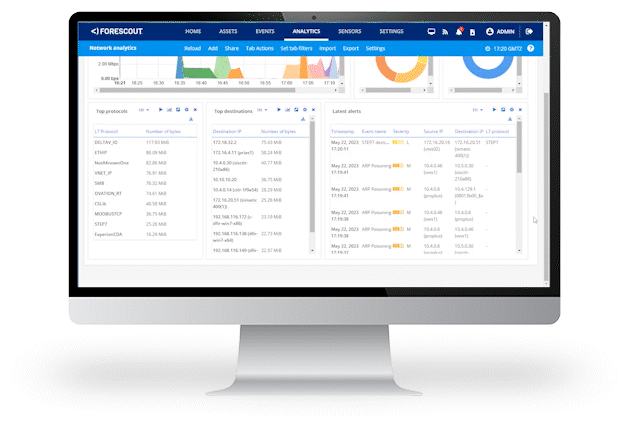
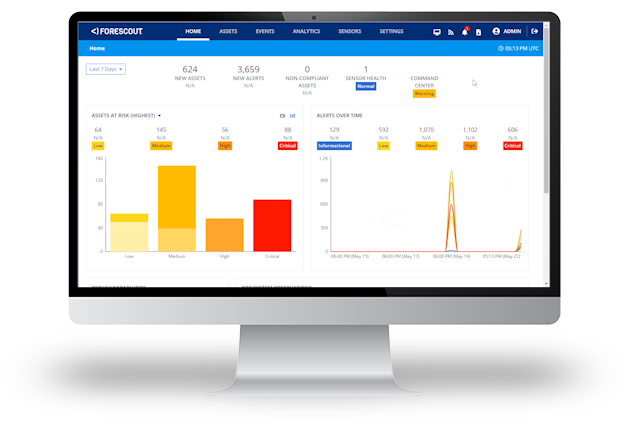
Industrial digitalization has accelerated the convergence of IT, IoT and OT assets and networks, increasing the complexity and vulnerability of previously isolated OT and ICS networks.
With industrial environments increasingly dependent on digital systems for production, you need continuous asset discovery, assessment and governance to help ensure regulatory compliance and avoid downtime – so you can detect and remediate cyber threats before they lead to operational or security incidents.