CYBERSECURITY A-Z
What is XDR?
Extended detection and response (XDR) is a relatively new solution category for security operations centers (SOCs) that breaks down traditional security tool silos to deliver holistic, automated detection and response across multiple domains. It consolidates essential SOC technologies and functions – a data lake; security analytics; user and entity behavior analytics (UEBA); security orchestration, automation and response (SOAR); and threat intelligence – into a unified platform with a single console, enabling security teams to efficiently investigate, hunt for and respond to true threats across the extended enterprise.
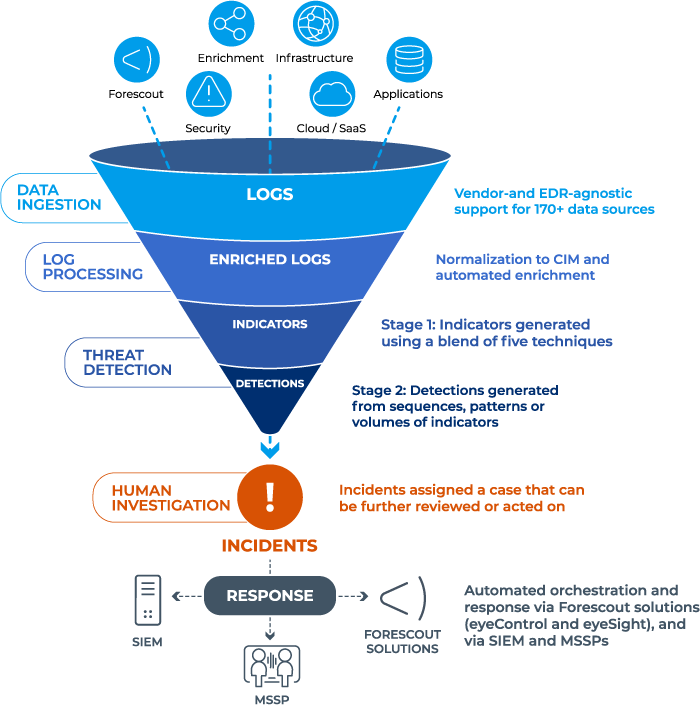
On the front end, an XDR collects telemetry and logs from data sources including email, endpoints (e.g., extended detection and response, or EDR), cloud workloads, network traffic, virtual containers and servers. The back end includes a data lake for log and telemetry storage and security analytics (or threat detection engine) that correlates the data and converts it into high-fidelity threats. Integrated case management functions accelerate investigation by providing a complete picture of the incident and timeline including victim(s), attack vector, tactics, techniques and procedures (TTPs) used, propagation and impact. An XDR can also orchestrate and automate incident response, either natively or via API integration with multiple security tools.
XDR emerged from the need for improved threat detection and response capabilities, higher productivity for SOC teams and security product consolidation. Today it is a crowded, rapidly expanding market, with vendors coming at it based on their existing security offerings or market position – endpoint, network/firewall, security information and event management (SIEM), vulnerability assessment, and managed detection and response. Regardless of the starting point, XDR is an evolution in threat detection and response beyond the complex and costly point-solution, single-vector approach.
SOC challenges and the rise of XDR
SOC teams face a daily barrage of incomplete and inaccurate alerts that lack vital contextual information needed to prioritize them. As a result, analysts miss critical threats and take longer to investigate and respond to them, increasing the risk of a breach. The typical SOC receives an estimated 11,000 alerts per day (“The State of Security Operations,” Forrester, 2020), or 450 alerts per hour – most of them low- fidelity, low-confidence alerts or false positives. SIEMs in particular generate a massive volume of alerts that lack the context necessary to understand threat severity.
In addition to alert fatigue, SOC teams face these challenges:
- Detection gaps. Sophisticated, stealthy threats can dwell and propagate between security tool silos that gather specific data for a specific function but don’t exchange information. For example, SIEMs can only detect threats based on the data they have access to. If there are blind spots in the network or data sources that aren’t integrated into the SIEM, it can’t detect those threats. By centrally collecting this data, XDR can analyze and correlate what looks like a series of low-confidence events into a higher-confidence incident that requires human investigation.
- Inefficiency. With too many siloed point products and too little automation across the full-spectrum threat detection, investigation and response process, L1 analysts spend too much time sifting through noise to identify true threats for investigation. When they do, senior analysts must still perform too many steps manually, jumping from screen to screen trying to establish a timeline and attack path and determine the right response.
- Cost. The current approach to SOC operations is too expensive, especially given the shortage of skilled analysts. Minimally, this includes the cost of licensing disparate security tools, log storage and onboarding new data sources to enrich threat detection capabilities. Add to that the cost of hiring and training analysts due to staff turnover, the resource-intensive approach to manual threat investigation and the never-ending task of creating and tuning threat detection rules.
The upshot of these common SOC challenges is that threats go undetected for too long, increasing mean time to detect (MTTD), mean time to investigate (MTTI) and mean time to respond (MTTR) – all of which raise the risk and consequences of an attack.
How XDR works
Generically, XDR solutions collect data from siloed security products across multiple domains into a data lake, then use powerful analytics combined with automation to correlate incidents and surface true threats. They then facilitate investigation and orchestrate incident response.
Specifically, Forescout XDR automates the detection, investigation, hunt for and response to advanced threats across all managed and unmanaged connected assets – IT, OT/ICS, IoT and IoMT – from campus to cloud to data center to edge. It continuously converts telemetry and logs into high-fidelity, probable threats, combining essential SOC technologies and functions into a unified platform, viewable and actionable from a single console.
What to look for in an XDR vendor
XDRs are far from being a commodity. When evaluating vendors, be sure to take into account your extended enterprise and existing cybersecurity tech stack. Here are some critical considerations:
- The extent of “extended” detection and response. Not all XDRs detect and respond to threats that impact all connected assets, including OT, IoT, IoMT and other unmanaged (or unagentable) devices. Integration with other Forescout solutions reduces your attack surface – and enables you to automate responses across the extended enterprise. True extensibility protects all connected devices across the entire enterprise, including cloud, campus, remote and data center environments.
- Open vs. closed XDR. Closed (or native) XDR solutions may require that vendor’s tech stack (including endpoint detection and response, network and cloud), whereas open systems can leverage telemetry across the entire attack surface, picked up from multi-vendor security tools. Forescout XDR is an open XDR that works with the security solutions you’ve already invested in, including 12 EDRs, so you derive more value from them and don’t have to rip and replace anything. That includes making better use of asset data and threat intel sources via automation across case management and incident response systems, sensors (network, endpoint, cloud) and enforcement points. Forescout XDR natively supports data from other Forescout solutions as well as more than 180 vendor- and EDR-agnostic sources including security, infrastructure, enrichment, applications and cloud/SaaS.
- Detection rule breadth and depth. How many rules does the vendor provide out-of-the-box, have they been fully tested/validated to work and how easy is it to create new rules in response to emerging threats? Forescout XDR includes more than 1,500 verified detection rules and models for those sources. They are regularly updated, and you can also easily create custom rules based on your environment.
- Security analytics. Robust analytics is the “secret sauce” that defines superior threat detection and enables accelerated response. Forescout XDR features a two-stage threat detection engine that applies a blend of five detection techniques to ensure effectiveness across different use cases to reduce false positives and improve the fidelity of threats detected:
- Cyber intel: More than 70 sources that look for backdoors, command-and-control traffic or phishing
- Signatures: Match object attributes to a known bad object to identify threats inside raw telemetry, uncleanable malware, ransomware, etc.
- UEBA: Looks for abnormal behaviors that match a digital pattern, footprint, human activity or network behavior with known bad behavior
- Statistics and outliers: Use clustering, grouping, stack counting, baseline and variation, outlier detection, logistic regression and other methods to detect anomalous activity
- Algorithms: Use context-aware AI and ML techniques such as supervised/unsupervised learning or deep learning to detect malicious or anomalous activity and predict attacks
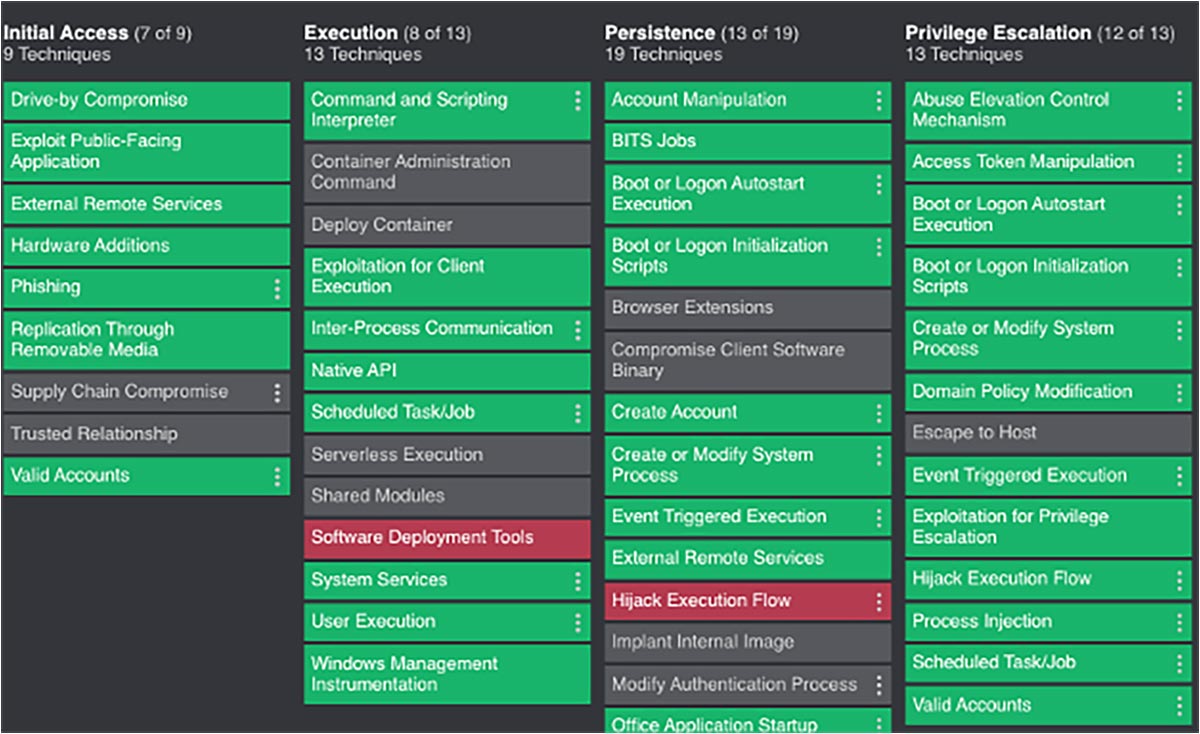
- MITRE ATT&CK integration. – MITRE ATT&CK coverage is the gold standard for XDRs, but how is it visualized? Forescout XDR allows you to instantly see how different data sources map to the TTPs of the MITRE ATT&CK framework. This makes it easy to prioritize the initial data sources that should be ingested for broad or specific TTP coverage, identify potential blind spots that adversaries can exploit and model which additional data sources would further elevate your coverage before implementing them.
- Upfront risk reduction. XDRs are not designed to reduce the risk of an attack in the first place. By implementing an XDR alongside Forescout solutions that continuously monitor all connected assets and enforce dynamic access policies, you reduce the risk of a compromised or non-compliant device connecting to your network at all – and reduce the demands on the SOC team.
- Predictable pricing. While XDR is designed to increase SOC efficiency and consolidate the functions of siloed security products, cost reduction isn’t a given because better detection can depend on log storage volume. Forescout XDR uses a license fee based on the total number of endpoints in your organization. We don’t penalize you for sending more logs to the cloud for better detection. Pricing includes 30-day log storage, and longer-term storage options are available.