CYBERSECURITY A-Z
What is MITRE ATT&CK?
MITRE ATT&CK is a free, globally accessible knowledge base of tactics, techniques and procedures (TTPs) used by adversaries across the attack lifecycle, based on real-world observations. Also referred to as the MITRE ATT&CK framework, it is used by industry, governments and academia as a common reference for categorizing and classifying adversarial tactics and techniques, and for developing distinct threat models and methodologies.
The name MITRE ATT&CK combines MITRE, the widely trusted non-profit organization that maintains the framework, with an acronym for what it includes: Adversarial Tactics, Techniques & Common Knowledge.
The MITRE ATT&CK knowledge base comprises open-sourced information as well as publicly disclosed incident response reports and threat intelligence contributed by cybersecurity analysts and threat hunters. There is no login, and anyone is invited to use it. Before the framework was released in 2015, this breadth and depth of knowledge was available only to large enterprises with dedicated analysts and researchers. Today, MITRE ATT&CK serves as a “lingua franca” of security operations, used by 89% of organizations.
Unlike other widely adopted cybersecurity resources, MITRE ATT&CK focuses on the adversary’s perspective and observed behavior, including motivation and end goals. It’s a unique resource for organizations of all sizes who want to better understand their adversaries, the behaviors they display and how to detect and remediate the threats they pose.
What is the MITRE ATT&CK matrix?
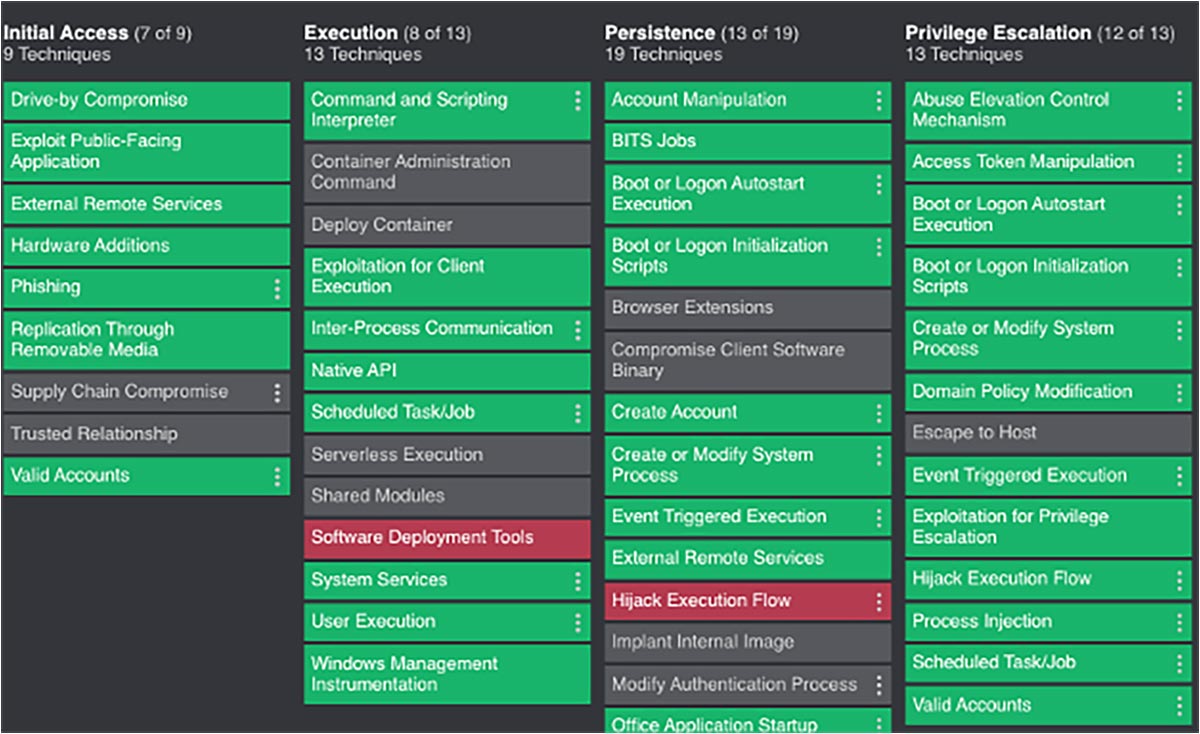
There are three MITRE ATT&CK matrices, each focused on a specific environment. They provide easy-to-use lookups of the common TTPs adversaries use to attack each environment.
- ATT&CK for Enterprise has 14 tactics, 196 techniques and 411 sub-techniques. It focuses on identifying and imitating adversarial behavior in Windows, Mac, Linux and cloud environments.
- ATT&CK for Mobile has 14 tactics, 66 techniques and 41 sub-techniques. It focuses on identifying and imitating adversarial behavior in iOS and Android operating systems
- ATT&CK for ICS has 12 tactics, 81 techniques and zero sub-techniques. It focuses on describing the actions adversaries might take when attacking OT/ICS environments.
Each matrix is organized into columns, with the tactics used in the attack lifecycle running sequentially at the top of each column and the related techniques listed below. Many tactics appear in multiple matrices and four – the initial access, execution, lateral movement, and impact – are common across all three. Depending on the matrix, techniques drill down to a varying number of sub-techniques or procedures. All discrete information can be filtered outside of the matrices to view by tactic, data source, mitigations, etc.
MITRE ATT&CK also tracks threat groups, maps them based on publicly reported technique use and correlates them to campaigns. Specific adversaries tend to repeatedly use specific techniques that work for them. However, they may also choose one sub-technique over another based on their skill sets, tools and the target’s exploitable vulnerabilities.
How is MITRE ATT&CK used?
First and foremost, MITRE ATT&CK provides a standard, concise language to name, describe and categorize adversary behaviors. This facilities intelligence sharing and threat hunting across all stakeholders. For example, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) uses MITRE ATT&CK to identify the TTPs used by threat actors in its cybersecurity advisories.
Here are some key stakeholders and use cases:
- Threat researchers, including Forescout Research – Vedere Labs, use the framework to research threats, categorize observed TTPs when analyzing an attack and share their findings with the cybersecurity community – including MITRE ATT&CK.
- Security operations teams use the framework to assess the maturity of their security program (including the effectiveness of specific measures to detect TTPs), identify gaps in coverage and evolve their strategies to keep pace with emerging threats. They can zero in on a specific tactic being used to target their industry and drill into its details, including ways to detect and mitigate the TTPs based on successful actions companies have taken.
- Cybersecurity solution vendors embed the matrices in their products and look at updates to guide development of new detection and mitigation capabilities. Forescout Threat Detection & Response integrates the MITRE ATT&CK framework so you can instantly see how ingesting different data sources impacts TTP detection coverage. This makes it easy to identify potential blind spots and opportunities to improve threat detection by addition specific data sources. The Forescout Platform also leverages indicators aligned with the MITRE ATT&CK for ICS to detect threats from misconfigurations and operational errors to advanced cyberattacks.