New research shows that more than 70% of devices on healthcare networks are running Windows 7—the OS fast approaching end of support.
Sales of PCs with Windows 7 Professional preinstalled ended on October 31, 2016. At that time, few gave much thought to the inevitable sunset of the Operating System (OS), but more recently, Microsoft has announced that it will start warning users about the Windows 7 end-of-support deadline. Support for Windows 7 devices is scheduled to end on or before January 14, 2020; while Microsoft offers an Extended Security Update (ESU) program, technical support and security updates will come at a cost. For many, it can be tempting for the functionality of such an OS to overshadow what the end of support really means— “if it’s not broken, don’t fix it.” The reality is, however, that end of life doesn’t just mean it’s time for an upgrade to a new PC with a new OS, more applications, a faster processor, and more storage; it means that if you don’t abandon Windows 7, you may be much more susceptible to compromise—data theft, ransomware attacks, zero-day vulnerabilities—and, you might wish you’d taken advantage of Microsoft’s free upgrade to Windows 10 back in 2015. And for the healthcare industry, failure to upgrade to a new OS or mitigate the risks associated with Windows 7 means potentially jeopardizing patient safety.
To put the looming Win7 sunset into perspective, let’s consider the end of life for Windows XP, a predecessor of Win7. After 12 years, support for Windows XP ended on April 8, 2014, and with it so did security updates and technical support for the OS. Just five months later, Home Depot confirmed a massive data breach that was ultimately tied back to legacy Windows XP vulnerabilities. Two-and-a-half years later, Home Depot reached a $27.25 million dollar settlement with affected financial institutions. In the healthcare industry, the largest hospital group in the UK was victim of a cyberattack in 2017. Investigations ultimately revealed that attackers gained access to the network via legacy Windows XP vulnerabilities.
While an OS may remain functional after sunset, that doesn’t mean it is secure. Vendors such as Microsoft release security updates and patches that, when added to the machine, can make it harder for adversaries to gain access to the device and consequently the enterprise network. Routine patching is a basic, fundamental defense against cyber criminals, yet it’s often not part of routine practice in many organizations. Within the healthcare industry specifically, default passwords and failure to patch are often cited as primary reasons hackers are able to gain unauthorized access to hospital networks and data.
In our report, Putting Healthcare Security Under the Microscope, we analyzed device data from 75 healthcare deployments to provide healthcare organization security and risk management leaders with insight into the types of devices connecting to networks and their associated risks. One of the specific areas of research centered on the potential impact of legacy Windows operating systems on the security posture of healthcare organizations. Here’s a look at what we found when our researchers queried the number of devices currently supported for more than a year, already unsupported, or soon to be unsupported come January 14, 2020.
Windows Operating Systems – The Good, the Bad and the Ugly
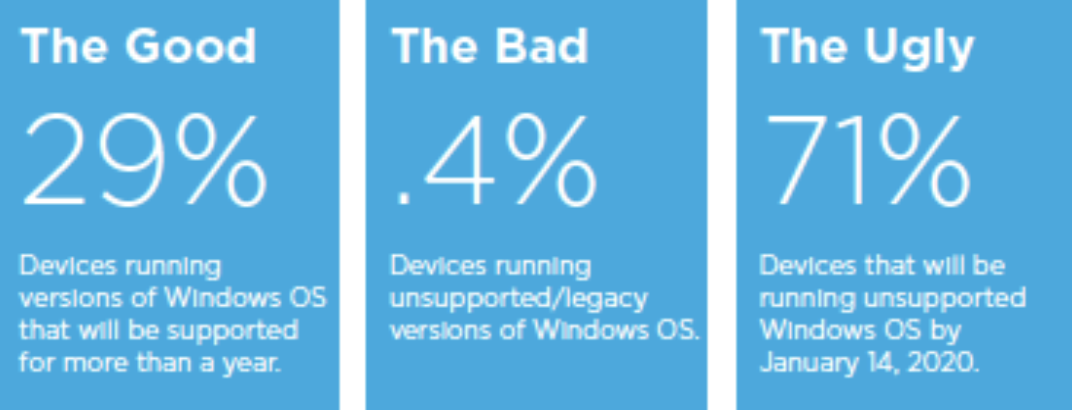
After querying a sample of more than 430,000 devices, we found that 29 percent of devices were running versions of the Windows OS that will be supported for more than a year, 0.4 percent of devices were running unsupported legacy versions of the Windows OS, and 71 percent of devices will be running an unsupported Windows OS by the scheduled end of support date, January 14, 2020.
Roughly 29 percent of the ‘good’ healthcare devices in our sample were running an OS with expected support beyond one year—they’re being patched and should continue to be patched for the foreseeable future. ‘Bad’ devices, on the other hand, are running a version of Windows with multiple exploits readily available off the shelf and are basically sitting duck targets if discovered by an attacker with a toehold on the local network. These are devices running XP or older versions of Windows that should have been abandoned long ago.
Patches and critical updates are still being pushed at this time for ‘ugly’ devices, but that support will soon end. Enterprise OS migration times vary based on size and complexity, but large healthcare organizations can take months to fully upgrade. To paint that picture plainly, that means that there are a host of devices on healthcare networks that are months away from zero-day exploits and other vulnerabilities if hospitals and healthcare providers do not upgrade to a newer version of Windows or take other action to manage the risks.
Recommendations
Hospitals, healthcare providers and other HDOs are faced with a massive cybersecurity challenge. While upgrading to a newer version of Windows is the optimal solution, there are also other best practices and interim solutions that may shield healthcare organizations from potential threats of the looming OS expiration. Our findings support adoption of tools and tactics for proactive cybersecurity risk management in connected medical environments. Healthcare IT leaders should leverage asset inventory, network segmentation, network access control, device hardening, compliance automation, technical policy orchestration, and risk management solutions to gain visibility into their network so they can make informed, strategic cyber decisions and investments, and regain control over their networks.
For more information on the cybersecurity risks facing healthcare organizations today, check out the report: Putting Healthcare Security Under the Microscope
