Updated to discuss the regulatory deadline on January 17, 2025.
Tick, tock. A new regulation is officially enacted this week.
The Digital Operational Resilience Act (DORA) is a robust cybersecurity regulation in the European Union (EU) takes effect on January 17. It is designed to help protect against evolving digital threats to financial systems.
Like GDPR, the scope of DORA isn’t only limited to financial services companies and banks. Service providers in Information, Communications and Technology (ICT) and third-party vendors are also on the hook. If you haven’t been preparing, the time to be is now. Given the global impact of technology within financials, it is in the best interest of CISOs, compliance officers and risk management teams outside of the EU to better understand DORA.
“Good governance and risk management require access to the right tools and technologies,” writes Corporate Compliance Insights in “Beyond Box-Checking: How EU’s NIS2 and DORA Elevate Security Standards.”
“These might include integrated risk management (IRM) platforms, incident detection and response systems, third-party risk management (TPRM) solutions, data encryption and network discovery tools,” reflects CCI.
Regulators are serious about several key areas in this beginning phase, according to legal watchers. Top priority? Registers of Information – however, the final implementing regulation was only published in December. That said, this register and focusing on its accuracy is very much the guidance.
Regulators have “reiterated that DORA has a strict 17 January 2025 deadline, and that the ESAs expect comprehensive compliance by that date,” finds law firm Skadden.
Remember, there are potential costs from fines for being in non-compliance.
Why DORA Is Necessary
Digital threats run deep today – and attackers do not care about borders. Ransomware alone grew by 73% in 2023. Criminals can easily buy and deploy automated attack kits with already-discovered entry points in hardware and software.
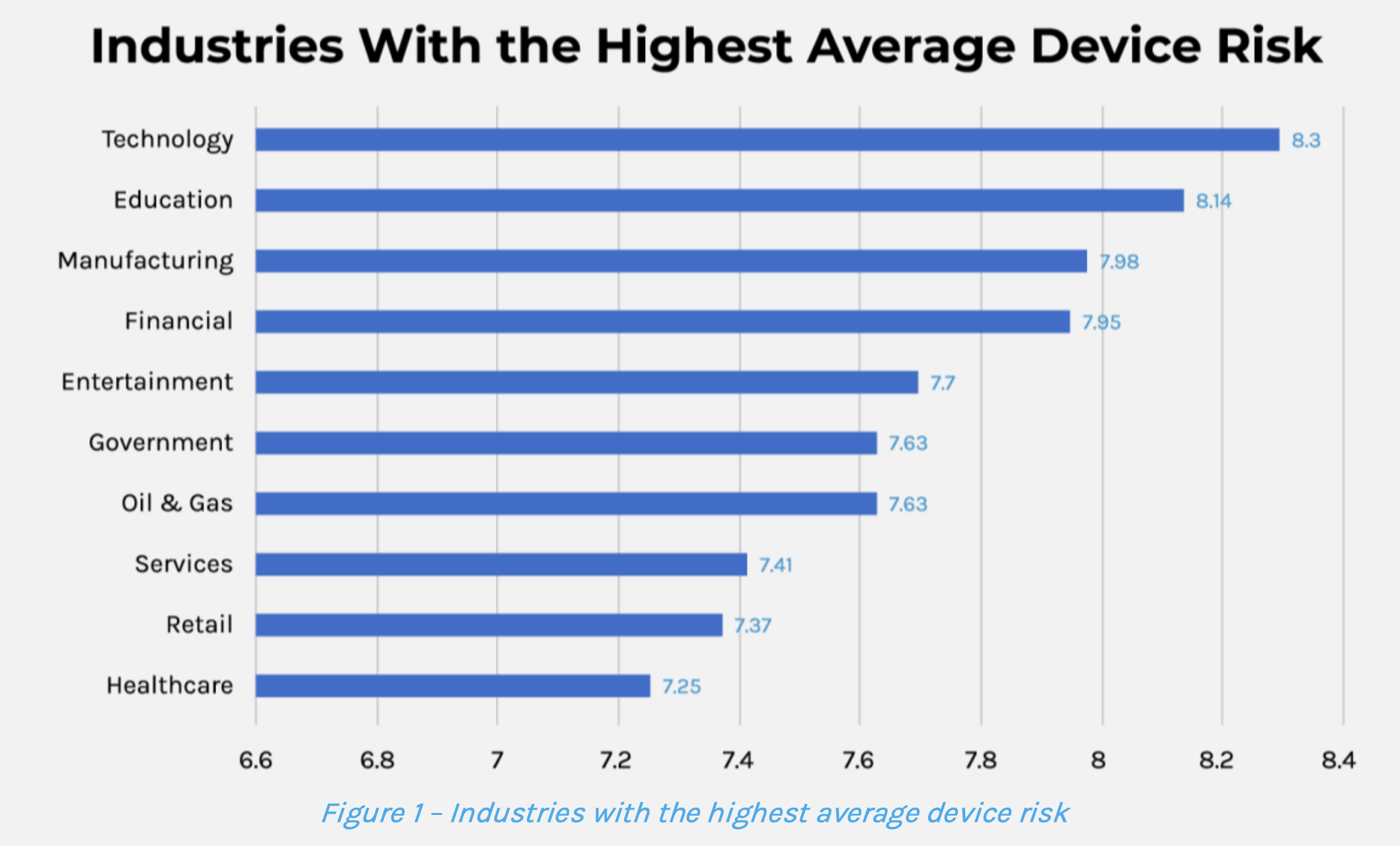
In our 2024 research on the riskiest devices, financial services ranks fourth for most risky devices across 10 major industries behind manufacturing, education and technology. Since 2023, there has been a 136% increase in IoT vulnerabilities.
From ransomware as a service to digital fraud to AI-based scams, faceless digital crime runs rampant. No industry knows this more than banks, credit card companies, insurers, et al. Between cyberinsurance premiums growing and spending increases in cybersecurity budgets, financial services organizations are deeply invested in IT security.
“The financial sector is increasingly dependent on technology and on tech companies to deliver financial services,” writes the EU parliament in its official explanation on why DORA is needed. “This makes financial entities vulnerable to cyber-attacks or incidents.”
Investment services and banks rely on digital technology. Many manage their own data centers and trading operations on-premises – but are also using cloud-based fintech for analytics, artificial intelligence (AI) and other applications. Many are adopting cloud models to stay competitive and keep up with customer needs.
Not all applications or server infrastructure is done in-house anymore, so the attack surface is widening. Banks moved 15% of their workload into the cloud in 2022 which was double from 2021, according to Accenture research. Plus, the financial industry has many third-party partners and vendors to manage – often with digital connections on the back end. Third party risk management (TPRM) is crucial.
DORA Compliance Explained
The process for DORA becoming a regulation has been ongoing since 2020. It was ratified in 2022.
The DORA regulation broadens the definition of operational resilience in the financial system beyond an economic focus on capital risk. Digital threats are as concerning to the 27 member-states of the EU as the financial health of the industry. In fact, codifying DORA is viewed as essential to securing financial health.
DORA builds on an already established regulatory foundation of managing the risk within ICT. DORA covers these six areas:
- ICT Risk Management
- ICT Third-Party Risk Management
- Digital Operational Resilience Testing
- ICT-related Incidents
- Information Sharing
- Oversight of Critical Third-Party Providers
“When not managed properly, ICT risks can lead to disruptions of financial services offered across borders,” reflects the EU. “This in turn, can have an impact on other companies, sectors and even on the rest of the economy, which underlines the importance of the digital operational resilience of the financial sector.”
Dive deeper with our guide:
“The Forescout Platform for DORA”.
DORA applies to more than 22,000 financial entities and ICT service providers operating within the EU, plus the ICT infrastructure supporting them from outside the EU, according to PWC. Companies impacted by DORA include:
- Credit institutions
- Central securities depositories
- Data reporting service providers
- Crowdfunding service providers
- Payment institutions
- Central counterparties
- Insurance and reinsurance undertakings
- Securitization repositories
- Account information service providers
- Trading venues
- Insurance intermediaries
- Other financial entity
- Electric money institutions
- Trade repositories
- Institutions for occupational retirement provision
- Non-financial entity: ICT service provider*
- Investment firms
- Managers of alternative investment funds
- Credit rating agencies
- Crypto-asset service providers
- Management companies
- Administrators of critical benchmarks
*This could be an internet service provider, a cloud service provider, telecommunications companies, an outsourced technology provider and more.
“If a firm is not already compliant with essential operational resilience regulatory guidance in the U.S., it may already be behind,” explains Mark Young, Senior Director, MorganFranklin. “For instance, if the organization still needs to select, define and map its critical business services, it may not be able to include end-to-end testing of those services in its 2024 testing calendar, which is required to show DORA compliance.”
Essential Steps to Prepare for DORA
- Identify and map critical services
- Establish impact tolerances
- Test tolerances (eg. penetration testing) and run exercises with lessons learned
Essential Steps to Comply with DORA
- Assess policies, procedures and controls against DORA regulations
- Assess third-party contracts for alignment with risk and impact on operational resilience
Understanding the Layers of ICT Incidents
There are three layers defining a major ICT incident:
- Layer 1: Determine if the incident affects critical services
- Layer 2: Determine if the incident is a result of a malicious intrusion
- Layer 3: Determine whether the incident impacts at least two of the following six criteria:
- Number of clients affected
- Amount of data loss affected
- Reputational impact
- Duration and service downtime
- Geographic spread
- Economic impact
Differences Between the EU, UK and US on Operational Resilience
Since the 2008 financial collapse in the US, operational resilience has become a crucial area of compliance – and important strategic value for companies. Cybersecurity risk has also been expanding – as has oversight – for all companies.
In 2023, the Securities and Exchange Commission (SEC) in the US changed notification requirements. Public companies are required to make a disclosure within 4-business days once a cybersecurity incident is deemed by the company, to be material to a reasonable investor, but many companies have struggled to meet the 4-day window in 2024, according to Forbes.
In banking and financial services, US regulators have formulated guidance dubbed Sound Practices to Strengthen Operational Resilience (Sound Practices) for cybersecurity. They direct organizations to follow:
- The FFIEC Cybersecurity Assessment tool
- The National Institute of Standards and Technology Cybersecurity Framework (NIST)
- The Center for Internet Security Critical Security Controls
- The Financial Services Sector Coordinating Council Cybersecurity Profile
“Moreover, the three US federal banking regulators recently adopted a new Computer-Security Incident Notification Rule that requires banks and their key service providers to ensure that their incident response plans include a mechanism to identify and provide immediate notice to regulators of ‘material’ cybersecurity incidents, including a ransomware, malware, denial of service (DoS) attack, or other hacking or similar incident,” explains global law firm White & Case.
The Potential Financial Impact of the EU DORA Regulation
A timeline for reporting incidents and fines are key parts of DORA compliance:
- Serious incidents must be reported within four hours and no later than 24 hours after they are detected
- A major ICT related incident also needs an intermediate report within a week of first notification and a final report with root-cause analysis no later than one month
- You can be subject to GDPR-class sanctions with fines that can amount to:
- 2% of an organization’s total annual worldwide turnover
- Or 3x the profit a financial entity has made because of the rule violation
The EU’s operational resilience governance framework is based on the UK’s Prudential Regulatory Authority framework for Operational Resilience. More details on DORA implementation are expected from the European Supervisory Authorities in July 2024. Overall, each country and region share a common goal to ensure greater resiliency, accountability and transparency to the public and to investors.