Update as of August 1, 2024
A year and a half after our original research, ransomware groups have continued to increase attacks targeting ESXi virtualization environments. Here are two of the main developments:
New groups are developing ESXi encryptors
The trend that started after Babuk’s source code leak in 2021 and led to the events reported below in 2023 continued into 2024 with more top groups such as Akira and Cactus targeting ESXi. Not just top groups but smaller players like Eldorado and SEXi also specialized in virtualized environments.
New ESXi 0-days
Two significant 0-day vulnerabilities were disclosed in this period: CVE-2023-20867 and CVE-2024-37085. While the former was known to be used for espionage, the latter was used by cybercriminals to deliver ransomware, such as Akira and BlackBasta.
The good news is that the number of ESXi directly exposed online has decreased significantly in the last year. While in February 2023 there were 85,000 servers online, there are now around 8,900 — a decrease of 90%.
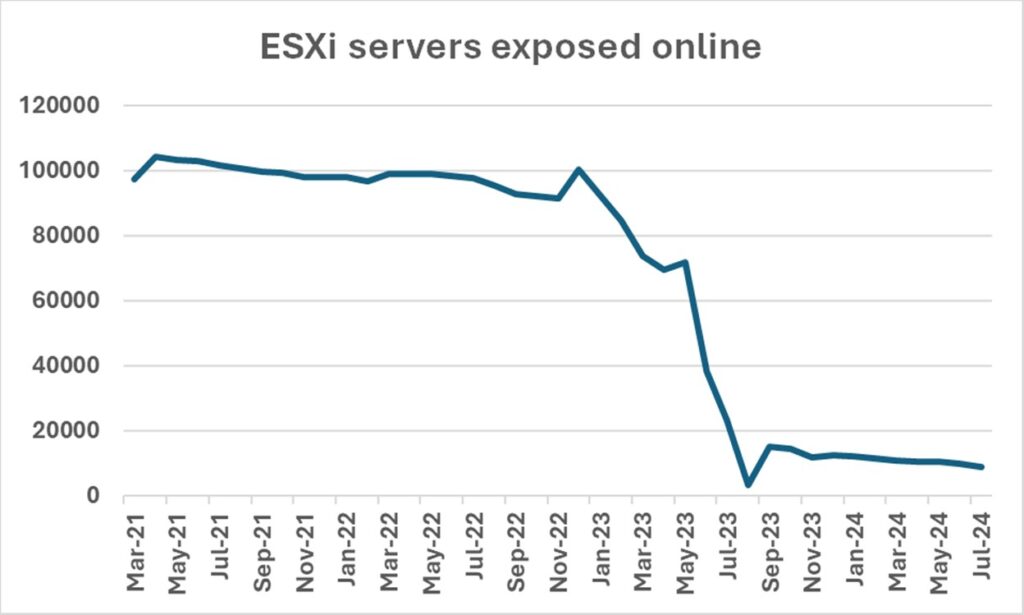
As observed in the attacks targeting exposed OT, it appears the sharp decrease in exposure is correlated with the attack campaign reported in March 2023.
Original post from March 9, 2023
In our new threat briefing report, Forescout’s Vedere Labs provides details on the recent ransomware campaign targeting VMware ESXi virtualization servers, or hypervisors, and analyzes two payloads used in these attacks: variants of the Royal and Clop ransomware. We also present the tactics, techniques and procedures (TTPs) used by attackers in this campaign, discuss mitigation recommendations and list indicators of compromise (IOCs) that can be used for detection or threat hunting.
Popularity of ESXi servers
As of February 24, 2023 there are close to 85,000 ESXi servers exposed on the internet, according to the Shodan search engine. Those servers are located mostly in France (11.4%), the U.S. (9.6%) and Brazil (9.4).
These devices run a wide range of ESXi versions, from 3.5.0 (first released in 2008 and last patched in 2013) to 8.0, the most recent version. The three most popular versions (6.5, 6.7 and 7.0) are the ones being exploited in the recent campaign (more details about the vulnerability in the next section).
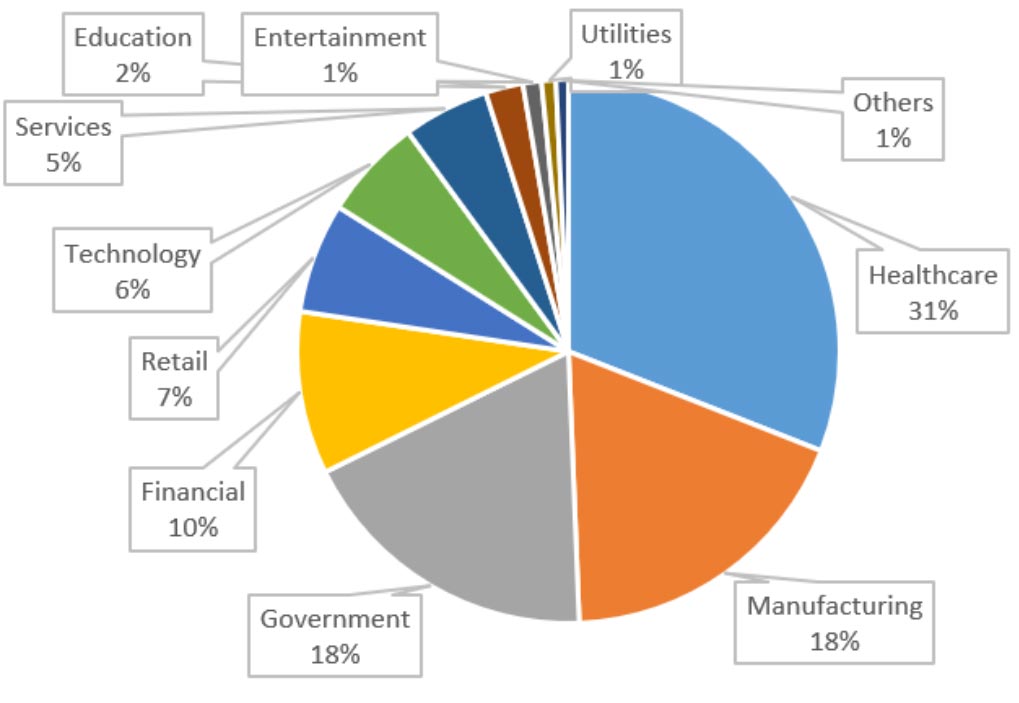
Forescout’s Device Cloud allows us to have deeper insight into organizations deploying ESXi. There are more than 17,000 ESXi servers tracked on the Device Cloud and the figure below shows their distribution by industry.
The ongoing ransomware campaign on ESXi
On February 3, CERT-FR issued a warning about an attack campaign targeting VMware ESXi hypervisors vulnerable to CVE-2021-21974 with the goal of deploying ransomware. According to Censys, the first infections of this campaign occurred on October 12, 2022. The company is still keeping track of the campaign and the number of infected servers has gone down from a peak of 3,500 at the beginning of February to around 1,000 on February 22. Most of those infected servers are in Europe (with France being the top affected country), followed by the U. S. and South Korea.
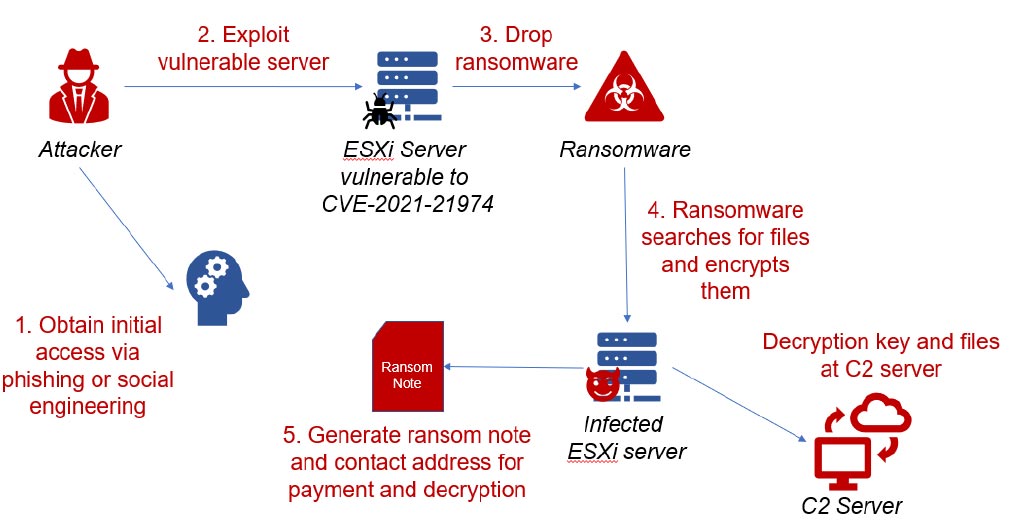
The attackers in the ongoing campaign take advantage of a remote code execution (RCE) vulnerability (reported in February 2021 as CVE-2021-21974 with a CVSS score of 8.8) that allows unauthenticated attackers to exploit a heap overflow in the OpenSLP service of ESXi. Phishing or social engineering can be used by the attacker to gain initial access into the networks containing vulnerable ESXi servers, which can then be exploited.
The ransomware families used in the ongoing attacks, including ESXiArgs, Royal and Cl0p, seem to be distinct from one another. The figure below shows the attack chain commonly used in this campaign.
ESXi: an attractive target for ransomware
VMware ESXi is an enterprise-class hypervisor developed by VMware to deploy and serve virtual computers. It allows the same hardware to be used for multiple virtual machines (VMs), which helps organizations save on hardware and easily scale infrastructure.
Since 2022, ESXi virtualization servers have been one of the main targets of ransomware groups, with the number of attacks targeting these servers tripling between 2021 and 2022. The increasing focus on new types of targets, such as ESXi, may be seen as a response to a decline in successful ransomware attacks or total ransom payouts in 2022. Ransomware groups are ever-changing and willing to adapt to maintain or increase profitability.
A past (and ongoing) trend has been the move from data encryption to data exfiltration, thus rendering backups ineffective. There may be many reasons for the current decline not strictly related to improving cybersecurity, such as:
- An uncertain economy making companies willing to pay less
- The Russian invasion of Ukraine leading to internal conflicts in groups such as Conti
- Cybercriminals changing their goals to target Ukrainian organizations
- Victims unwilling to pay because of sanctions
Nonetheless, improved cybersecurity certainly plays a role in the decline. The increased ability of potential victims to detect and respond to attacks through improved application of technology on managed devices has not gone unnoticed by ransomware threat actors. This makes these actors rethink their targets and adapt to remain profitable.
Unmanaged devices such as ESXi servers are a great target for ransomware threat actors. That’s because of the valuable data on these servers, a growing number of exploited vulnerabilities affecting them, their frequent internet exposure and the difficulty of implementing security measures, such as endpoint detection and response (EDR), on these devices. ESXi is a high-yielding target for attackers since it hosts several VMs, allowing attackers to deploy malware once and encrypt numerous servers with a single command.
Many of the past ransomware attacks targeting ESXi servers have been similar, with attackers either buying valid credentials from initial access brokers (IABs) or discovering vulnerable hosts via search engines such as Shodan or Censys, then exploiting known vulnerabilities and deploying a ransomware payload. In March 2022, Vedere Labs reported the trend of ransomware infecting ESXi servers. In April, we published an analysis of an incident using the ESXi version of ALPHV and in September, we reported how the trend had exploded with many other families targeting these servers such as Lockbit, Cheerscrypt, RansomEXX, Hive, Luna, BlackBasta and RedAlert/N13V. Ransomware is now commonly either created specifically for these environments or adapted for them, with many ransomware families written in Go or Rust for better cross-compilation. This allows those families to target Windows, Linux (which runs on many servers and several IoT devices) and ESXi with the same software.
Even as attackers target these environments, organizations will probably continue to increase their reliance on virtualization, given its undeniable advantages. However, these same organizations must realize that both the servers hosting VMs and the VMs themselves are part of an extended attack surface that is often not covered by EDR and other traditional security solutions. That makes them a blind spot on the network.
Ransomware is just a part of the threat landscape for virtualized infrastructure. Beyond what we discuss in this report, there are known attacks leveraging a custom Python backdoor on ESXi servers, APTs targeting Log4shell vulnerabilities on VMware Horizon, attack tools developed specifically for ESXi and even vulnerabilities allowing attackers to break out of virtual machines and execute code on the host operating system.
Mitigation recommendations for ESXi attacks
VMware provides a comprehensive guide on securing ESXi hypervisors. Here are specific mitigation recommendations based on their guide and other sources:
- Update your ESXi software: It is strongly recommended that administrators update servers to the latest version of VMware ESXi software to prevent several initial access or lateral movement vectors relying on vulnerabilities, including CVE-2021-21974. If patching is not possible or if the Service Location Protocol (SLP) is not needed (even on a patched server), harden ESXi hypervisors by disabling the SLP service. This is also valid for other services running on ESXi that may not be needed, such as SSH and Shell access.
- Harden passwords: Initial access and lateral movement vectors that rely on valid accounts can be mitigated by implementing strong password policies, enabling multifactor authentication, and monitoring account changes and authentication attempts. For organizations that have the means to do so, it is recommended to monitor discussions about leaked credentials on underground markets.
- Restrict access: To mitigate against most initial access vectors, ensure the ESXi hypervisor is not exposed to the public internet. To prevent the spread of an attack starting from ESXi, limit the communication between the servers and the rest of the network either by restricting allowed addresses and ports via native settings (“Allowed IP Addresses” on ESXi), firewall access control lists or both.
- Monitor network traffic: To detect an ongoing attack, monitor abnormal activities on network traffic and on ESXi servers. Network intrusion detection systems can detect network scanning and exploitation attempts, including for known vulnerabilities and anomalous or malformed packets. Network traffic from or to unknown IP addresses can also indicate exploitation. On ESXi servers, detection is more difficult because attackers rely on native commands that are hard to differentiate from usual system administrator actions. The Recorded Future report presents several ideas for monitoring anomalies. They include monitoring log files for authentication attempts, operations on VM snapshots and potentially malicious commands, such as esxcli.
- Create recovery backups: Ensure there are backups of the VMs residing outside the ESXi environment to enable recovery in the case of an attack. To recover from an attack, recommendations vary depending on the payload used. CISA published an extensive guide on recovering from ESXiArgs, while the Clop ELF variant had a flaw allowing for decryption for some time. The ID Ransomware project helps identify the malware used in an attack, while the No More Ransom project links to dozens of publicly available decryptors. VMware Security has a dedicated blog post with resources related to the ESXiArgs ransomware as well as a Ransomware Resource Center with more helpful information.
How Forescout can help
The Forescout Platform provides visibility, compliance, segmentation and threat detection against ransomware on ESXi servers:
- Visibility and compliance. The eyeSight VMware vSphere plugin brings visibility into ESXi hosts and associated guest VMs, with granular detail into various ESXi and guest operating system properties. It also allows for control policies over VM state and network access similar to those applied to campus endpoints. For instance, it can automatically assess software versions and services running (such as SSH), then take action against non-standard configurations.
- eyeSegment enables segmentation across the entire enterprise, including ESXi servers.
- Threat detection. Forescout Threat Detection & Response ingests logs from multiple sources across the enterprise and detects true threats while weeding out low-fidelity, low-confidence alerts and false positives among those. It includes is a specific rule implemented for ESXi ransomware attacks – Rule CY-IR-0568 Linux Logs: VMware ESXi ransomware Detected.
For a deeper dive into ransomware targeting ESXi servers and TTPs used in these attacks, read the full threat briefing.