As cyber threats continuously evolve, hackers are refining their attack tactics and the frequency of assaults. Over the past several years, 63% of Security Operations Center (SOC) analysts report the size of their attack surface has increased, according to Security Magazine. Similarly, our 2023 Threat Roundup research discovered the enterprise is experiencing 13 attacks every second.
Attackers are capitalizing on visibility gaps – the blind spots – between cybersecurity tools, technologies and security operation processes. While some organizations believe that hiring more personnel and buying more tools are answers, these approaches are insufficient. Devices and unmanaged devices are a big visibility gap. Tools often do not integrate or communicate well with each other, so data in one tool is not seen by another tool. It is the aggregation and correlation of data that creates the context organizations need to close the visibility gaps.
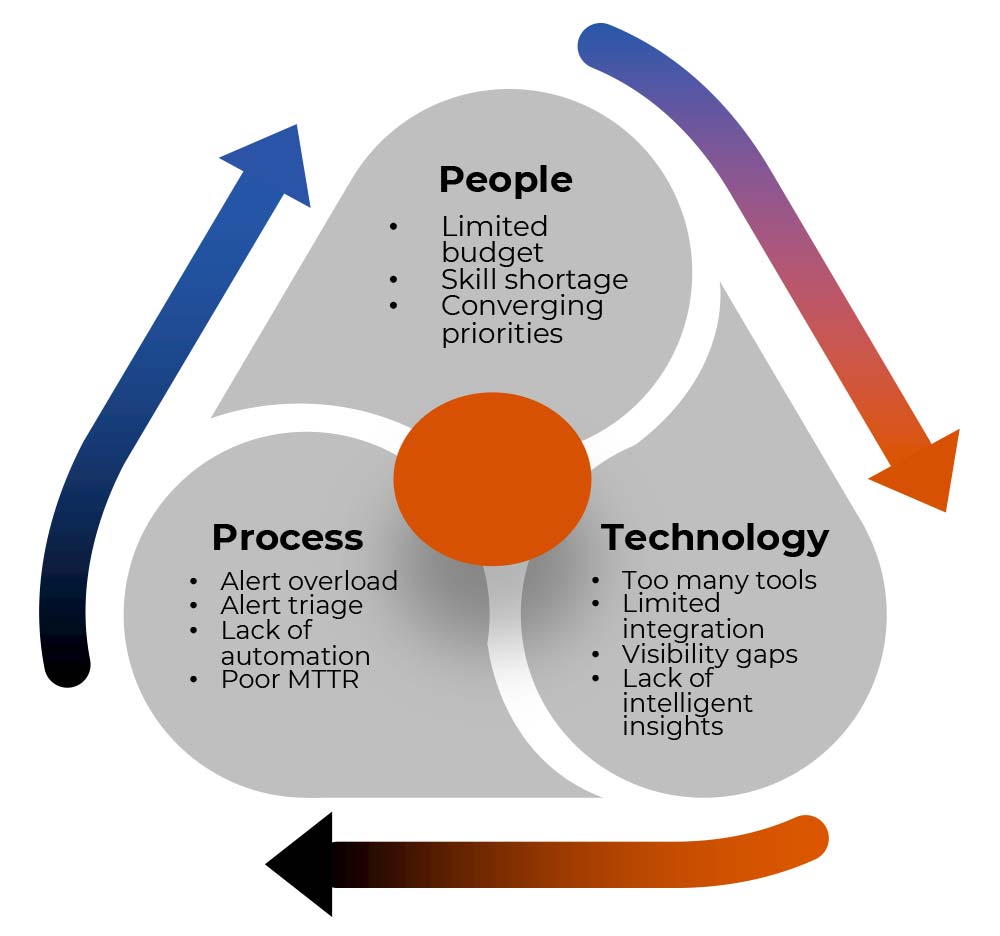
To manage threats, enterprises require an integrated approach that consolidates all pertinent data and provides deep visibility across the threat landscape. To defend against these evolving threats, organizations should establish a unified defense by integrating people, processes and technology within the SOC to improve their security posture.
SOC analysts need:
- Full network visibility – including all connected devices
- Rapid and accurate cybersecurity threat and network context with the right data
- Situational awareness to identify and isolate true threats from the noisy ones
Why SOC Integration Matters
SOC integration connects security tools, technologies and processes together to create a unified defense posture. A holistic view empowers SOC analysts to detect patterns, trends and anomalies that signal security risk. The goal? Early detection for proactive, rapid prevention measures. But without an integrated approach, this can be tough to manage the attack volume and to separate the attack noise from actual threats.
SOC integration drives easier collaboration via automation with refined workflows resulting in faster time to detection and response. By integrating security tools and data sources, such as endpoint detection and response (EDR) solutions, network intrusion detection systems (NIDS) and log management platforms, the SOC can consolidate security data for analysis.
Beyond visibility, SOC integration can automate and orchestrate security processes reducing alert fatigue and repetitive, often manual case management tasks. The SOC can respond to security incidents faster and more effectively by using playbooks and workflows to automate incident triage, enrichment and response processes. Automation also reduces the potential for human error freeing up analysts to focus on more strategic tasks, such as threat hunting and risk assessments.
The key components of a security operations center (SOC) are the people, the processes and the technology. These three things together driver greater efficiencies, reduce risk and improve security effectiveness.
The Lack of SOC Integration Results in an Ineffective Defense Posture
A fragmented, hodgepodge of standalone security tools often leads to a fragmented response to cyberattacks. While these individual tools may provide some level of protection, the lack of integration between them creates silos of information. It hampers the ability to detect, respond and mitigate security incidents effectively.
A lack of integration extends beyond technology. People (teams) and processes also suffer. Without cohesive collaboration and alignment in teams and processes, the organization can struggle to maintain a unified defense posture. This disjointed approach often results in stressed SOC analysts too.
SOC analysts are too often left grappling with incomplete data, manual processes and delayed response times. This leads to burnout in the ranks – which leads to turnover and skills shortages. A 2022 study of SOC performance found 71% of respondents rate the pain of SOC staffers at 6 through 9 out of 10, according to the SANS Institute.
“This confirms that most SOC managers and company leaders need to make significant adjustments in how they operate and manage their people to make SOC work less painful,” writes the SANS Institute.
An integrated SOC approach will lighten the load on analysts because it will automatically help identify and separate true threats from those designed to distract and overwhelm SOC teams.
The True Benefits of SOC Integration
The benefits of SOC integration extend beyond operational efficiency and effectiveness. By integrating security tools, data sources and processes within the SOC, organizations can achieve holistic, proactive cybersecurity risk management.
Optimized resource utilization. Better collaboration across security, risk and compliance teams. Streamlined workflows for faster response and reduced noise. A unified and complete view of the organization’s security posture empowers SOC analysts to make informed decisions. SOC integration enhances the overall resilience and agility in the face of evolving security challenges.
SOC teams gain:
- A stronger security posture – Provides a more proactive approach to threat detection and incident response.
- Efficient threat detection and response – Minimizes the dwell time and helps reduce the impact of security incidents.
- Better collaboration and communication – Resulting in faster decision-making and more effective incident response.
- Optimized resources – Enables organizations to allocate resources based on severity and priority of security incidents.
“By aligning the SOC within business processes and managing cyber risk proactively, organizations can reduce operational costs while fortifying against threats,” writes Jason Hart, CTO of Rapid7, in Forbes. “This shift demands commitment, investment and cultural change, but the benefits can be substantial.”
SOC Integration Is a Strategic Imperative
SOC integration goes beyond operational efficiency and effectiveness. It is a strategic necessity for organizations defending against the ever-evolving threat landscape. By connecting people, processes and technology, organizations can establish a unified and cohesive defense posture.
This approach, coupled with the comprehensive visibility and seamless integration offered by Forescout Threat Detection and Response (TDR), enables effective detection, response and mitigation of cyber threats. As cyber threats grow in complexity, SOC integration becomes increasingly vital for organizations aiming to stay proactive and safeguard their sensitive data, assets and reputation from cyber threats.