In my recent blog, I recapped a conversation with Jack Jones, Chairman of the FAIR Institute and Gaurav Pal, CEO of stackArmor, where they debunked three myths about why risk quantification seems so difficult. The reality is that each year threat actors become more savvy and the attacks they use become more sophisticated while corporate resources continue to shrink or remain the same. The gargantuan task of quantifying risk across the extended enterprise seems impossible for some. How do CISOs and their teams scope and tackle this task so that they can prioritize and get the best bang for their security or risk mitigation buck? Here’s a three-step process our executive guests put together to simplify risk planning and mitigation:
Step 1: Use the NIST Cybersecurity Framework to scope what you need to measure
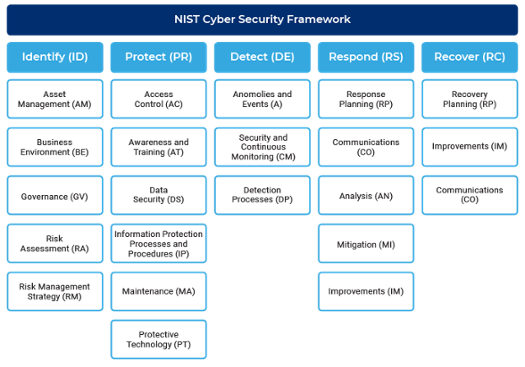
The simplest approach is to walk through each control family, one by one. For example, starting with the Identify Function, the first control within the Asset Management category is AM.1 Physical device inventory. Risk quantification does not have to be precise, but it should be accurate. An accurate assessment requires full device visibility across your extended enterprise of campus, cloud, OT, IoT and data center assets. To reduce downtime and operational overhead, use a tool that performs passive and active monitoring techniques to discover managed and unmanaged devices connecting to your heterogeneous network infrastructure.
Step 2: Use device visibility to provide inputs for your risk measurement process
Being able to see all devices exposes a whole world of potential vulnerabilities. Forescout’s report, Putting Healthcare Security Under the Microscope, used actual healthcare device data from the Forescout Device Cloud to determine that many healthcare organizations are running legacy operating systems—many of which will be unsupported over the next few months.
Knowing that the downtime associated with patching some critical care systems may be unacceptable, risk managers must now determine the level of risk they will accept, versus what they can and should mitigate. While being familiar with traditional managed devices is essential, unmanaged, and more importantly, unknown devices can become the doorway to introducing threat actors to the crown jewels on your network.
Step 3: Use the FAIR Methodology to provide a risk score
Now that you have a more detailed view of the devices on the network, you can classify those devices and use the FAIR methodology to examine the loss event frequency and loss magnitude of your most precious and critical assets. Analyze the probability of action and the financial and other impact that a breach via this device could have on your organization’s reputation. What are the legal and regulatory implications from having a rogue device on your network? We explored that question in a previous blog, Can a rogue device cost your company millions?
The FAIR methodology transcends technical boundaries and allows you to quantify risk even in the OT/ICS space. We also wrote about the 4 unique challenges that the IT-OT convergence is creating for critical infrastructure companies. Another area of concern is shadow IT apps that can become the Trojan horse that opens the way for attackers to get access to your company’s most valuable assets. We address cloud security risks head-on with a blog that describes the best practices that all CISO teams should know to reduce risk in the cloud.
For a deeper dive into the three steps above, watch this 6-minute video presented by our guest executives, Jack Jones and Gaurav Pal.