In a new threat briefing report, Vedere Labs analyzes the behavior of the Night Sky malware on two samples, presents a list of IoCs extracted from the analysis and discusses mitigation.
The Night Sky ransomware was first reported on January 1, 2022. Victims were asked to contact the attackers to pay for the ransom. If the victims refused to pay, attackers threatened to expose their data on a leak site. This is known as double extortion ransomware, which was first used by Maze and is now used by several ransomware groups.
Previous reports suggest that Night Sky has been distributed by exploiting the Log4Shell vulnerability and is connected to a threat actor based in China, which is tracked by Microsoft as DEV-0401. The Night Sky campaign was short and compromised two victims in Bangladesh and Japan. Currently, the Night Sky infrastructure is offline, which suggests the threat actor may have rebranded.
Night Sky provides an interesting view into the relationships among several ransomware families. Night Sky was discovered to be a fork of a ransomware family called Rook, which was itself derived from the leaked source code of Babuk and deployed by the same threat actor that used LockFile and AtomSilo, which are so close they share the same decryption tool. Shortly after the Night Sky and Rook leak sites went offline in January 2022, a new gang named Pandora appeared online, claiming one of the victims of Rook as its own – the Japanese automotive parts manufacturer Denso – and using malware samples that are still detected as Rook. The Pandora leak site is still active as of this writing. Currently, they claim a total of seven victims.
These relationships are depicted in the figure below.
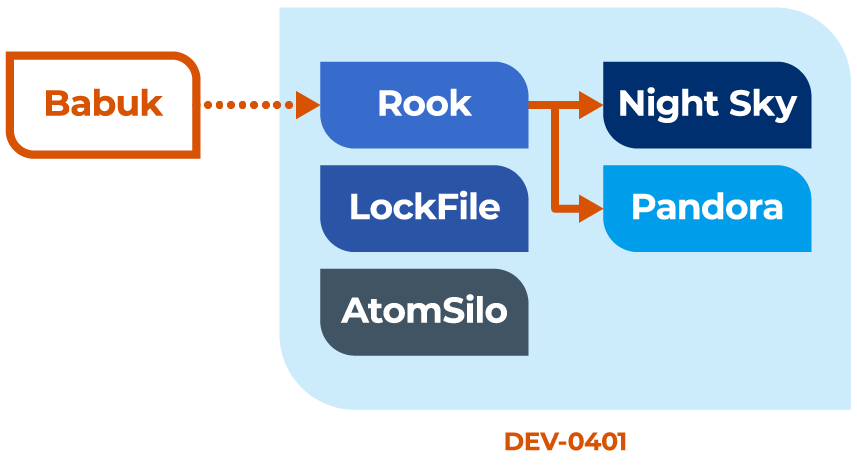
Understanding the current trend of rebranding ransomware gangs helps network defenders better use threat intelligence by focusing on strategic defense against threat actors rather than tactical defense against individual threats.