Over the last decade, the automotive industry has undergone a massive technological transformation in connectivity and personal mobility. Modern cars are becoming more like computers than mechanical artifacts.
It is not unusual for a modern car to have remote connectivity and hi-tech features, such as a touch dashboard that can keep itself up-to-date with periodic software updates.
To get ahead of the competition, manufacturers need to innovate at a fast pace. However, with these innovations come concerns about automotive cyber security.
These connectivity innovations open up the car industry to the Information Technology (IT) world, where the cyber threat landscape is ever-growing and becoming more sophisticated. 1
Thus, providing adequate cyber security features is very important but usually overlooked.
The Origins of In-Vehicle Networks
The first analog electronic component introduced was the General Motors (GM) OnStar. 2
system in 1996. OnStar also represents the first in-vehicle network to connect different systems. Drivers could check fuel level or engine temperature by looking at the car”s dashboard.
Different network technologies have since been introduced to perform different functions, such as steering and transmission. This evolution finally resulted in the infotainment system, allowing in-vehicle entertainment as well as mobile phone integration (i.e. hands-free calls).
Despite the huge improvement in user experience, these technologies have increased the complexity of both in-vehicle networks and the software needed to manage them. It is estimated that software in modern cars exceeds 100 million lines of code. This is more than 15 times greater than the software needed in existing avionics systems. 3
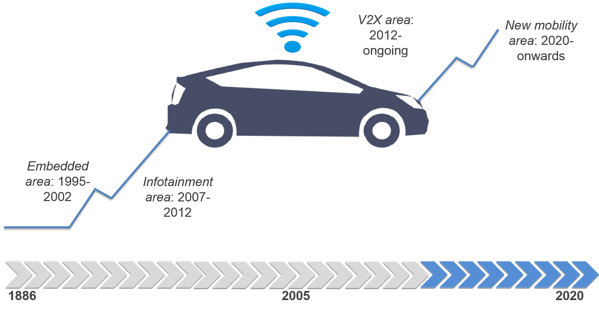
Fig. 1 Evolution Stages in the Automotive Industry
Connected Cars
New components and network technologies provide more interconnectivity capabilities both inside and outside the vehicle. Such capabilities often require substantial modifications to the in-vehicle architecture.
In-vehicle interconnectivity also leads to the development of new areas of communication. The so-called vehicle-to-everything (V2X) connections.
V2X enables the interaction of vehicles with other vehicles or the surrounding infrastructure, including traffic lights, highways or trains. This forms a larger mobility ecosystem currently known as Intelligent Transport System (ITS).
ITS is formed by conceptual elements of the Internet of Things (IoT), with the primary goal of improving citizens” safety by reducing road accidents and traffic jams. It also aids faster and simplified commuting to any destination.
Autonomous Driving
The transition to V2X allowed cars to become smarter. Certain manufacturers (e.g. Tesla) have gone one step further by working on autonomous or self-driving cars. 4
In the coming years, we expect autonomous cars to disrupt mobility as we know it. Driving will no longer need human intervention. More complex software will handle all in-vehicle functionality. Vehicles will be controlled solely by sensors.
Connected Cars: Security Challenges
Connected and autonomous cars will certainly become part of our future critical infrastructure. So, it is necessary to provide the automotive industry with adequate security solutions.
The need for automotive cyber security has been proven by:
To ensure interconnectivity, connected cars rely on wireless and cellular communication interfaces. This exposes them to underlying security risks. In the Nissan Leaf scenario, attackers gained direct remote access to the in-vehicle network of an entire vehicle fleet around the world.
These attacks revealed that neither the automotive industry nor the security community is ready for a large-scale targeted attack to the upcoming connected car ecosystem.
Until these attacks, the general perception was that an attacker required physical access to the vehicle. As such, car manufacturers focused on increasing physical security.
As in-vehicle wireless and Bluetooth connections become standardized, the threat increases. This is a call-to-action for security practitioners and car manufacturers to provide connected cars with security solutions that address the increasing threat landscape.
Providing adequate cyber security mechanisms is still challenging due to the in-vehicle network complexity. In-vehicle components and technologies were also built with no security in mind.
Adopting security mechanisms already used in other application domains (e.g. encryption) will introduce additional computational time and processing performance. This may lead to safety risks, as components linked to braking or steering could become unresponsive.
Solutions for the Automotive Cyber Security Threat
A systematic approach to ensure risk mitigation in automotive systems would require:
Increased Visibility
The interactions between the digital systems inside the vehicle, as well as with other entities in its environment, should be monitored to detect suspicious activities. This will help to identify faults or errors by enabling real-time analytics of the network connections inside the vehicle, as well as with its external environment.
Protection Schemes for the In-Vehicle Interfaces
The number of interfaces that allow data exchange between the in-vehicle subsystems and its external environment is growing. However, exploiting vulnerabilities on certain interfaces might still need physical vehicle access, while for others it can be done remotely 8. Therefore, different security measures are required for protecting each interface. These can be combined to achieve the highest threat protection level possible.
Develop an Incident Detection and Response Strategy
An automotive cyber-incident requires immediate remediation, to ensure passenger safety. To handle this situation, cross-industry stakeholders (e.g. security experts, system integrators, manufacturers or fleet managers) must join forces. All stakeholders should collaborate on a robust security program against the ever-increasing automotive threats, such as the Automotive Information Sharing and Analysis Center (Auto-ISAC) 9 initiative.
A security framework that properly addresses cyber risks for the future of the automotive industry will make it safer. It will also speed up the adoption of new technologies such as connected and autonomous cars.
1 2017 Threat Landscape, SANS Survey: https://www.sans.org/reading-room/whitepapers/threats/2017-threat-landscape-survey-users-front-line-37910
2 https://www.onstar.com/us/en/home/
3 https://spectrum.ieee.org/transportation/systems/this-car-runs-on-code
4 https://www.tesla.com/autopilot?redirect=no
5 https://www.wired.com/2016/08/hackers-fool-tesla-ss-autopilot-hide-spoof-obstacles/
6 http://www.bbc.com/news/technology-33650491
7 https://www.troyhunt.com/controlling-vehicle-features-of-nissan/
8 Automotive Security Best Practices, Intel Report: https://www.mcafee.com/enterprise/en-us/assets/white-papers/wp-automotive-security.pdf