Updates:
- Join the Forescout Community Discussion on controlling Cisco devices impacted by the CDPwn vulnerabilities.
- Learn why seeing all layer 2 CDP traffic is crucial (going beyond SPAN), and why instrumenting controls through switching infrastructure is the best way to fully identify devices impacted by CDPwn.
Another vendor protocol was laid bare today, with Cisco issuing multiple security advisories as Armis researchers disclosed CDPwn, demonstrating multiple ways to unravel Cisco Discovery Protocol (CDP), a fundamental vendor protocol baked into an array of Cisco-made products. It matters because the impacted Cisco devices are the de facto standard when it comes to VoIP and networking gear across enterprises.
To illustrate the ubiquity of Cisco in the enterprise supply chain and the variety of Cisco devices impacted, Forescout researchers turned to the more than 11 million devices in Forescout Device Cloud, one of the world’s largest crowdsourced device repositories. Most Cisco devices are affected by CDPwn issues, and the broad reach of Cisco inside the enterprise shows why this is so significant.
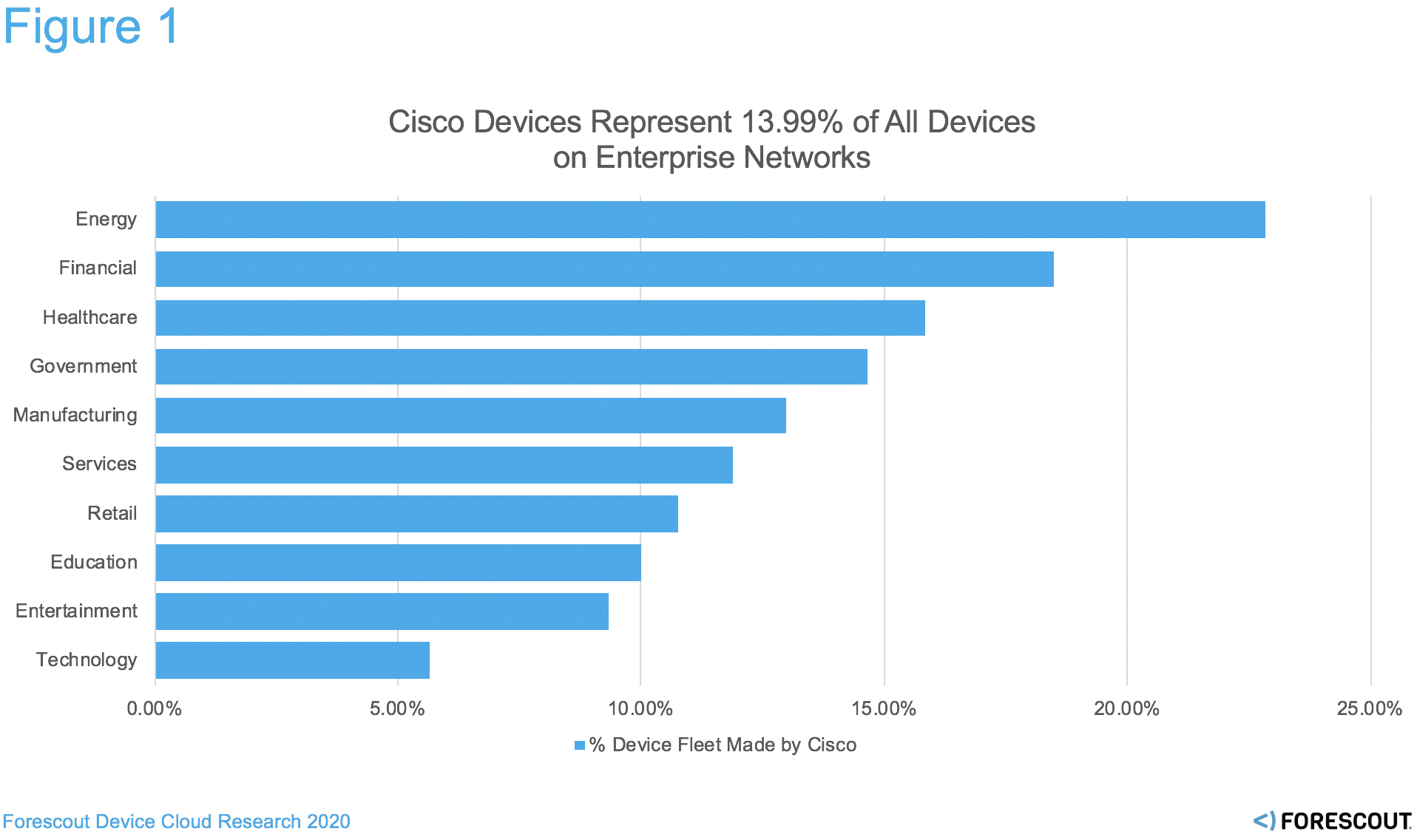
Figure 1. Cisco makes almost 1:7 devices on enterprise networks today
Even beyond networking devices, the Armis researchers suggest that depending on configuration, “tens of millions” of devices could be impacted. Cisco issued security advisories that potentially impacted devices include enterprise switches, routers, firewalls, collaboration systems, VoIP phones, IP cameras and more. As noted in Figure 2, VoIP devices are widely impacted, as they comprise 40% of Cisco devices present on enterprise networks today.
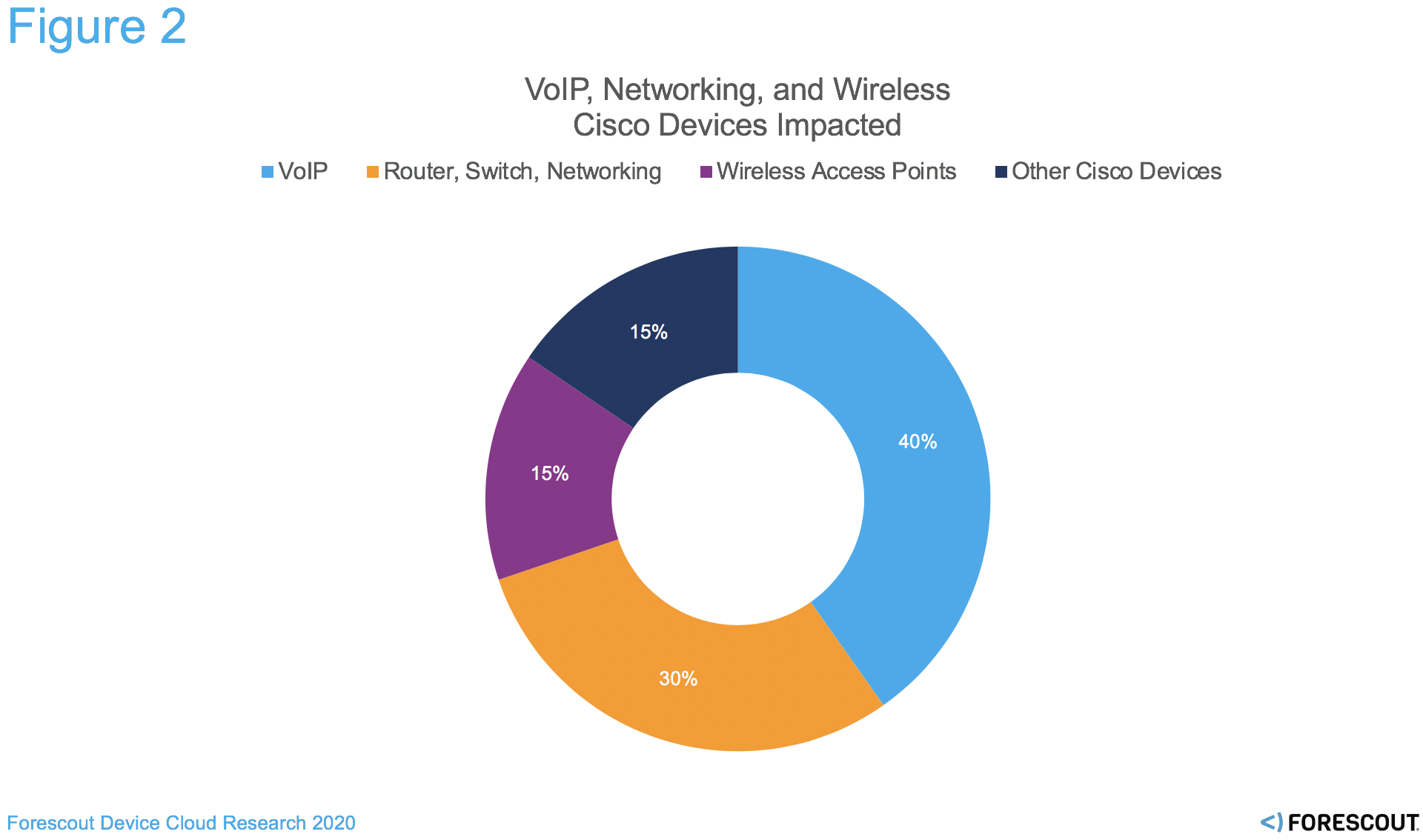
Figure 2. VoIP, Networking, and Wireless are the most common Cisco devices on the network
What do we expect?
The CDPwn vulnerabilities serve as a reminder how dependent networked technology is upon its underlying protocols—and when protocols fall, they fall hard, whether it’s SMB and RDP in Windows, or CDP in Cisco products.
While no exploits have been reported due to these issues, the fact that so many devices are impacted will make the vulnerabilities attractive targets for exploit kits in the future.
Recommendations
- The first response when protocols fall is to identify the impacted assets by vendor and product, and then take mitigation steps accordingly. That’s why the Center of Internet Security’s No. 1 critical control is Inventory and Control of Hardware Assets, which includes identifying devices by vendor, function, and operating system.
- It’s crucial to note that analysis of layer 2 traffic (where CDP is used) is key to managing this kind of protocol vulnerability.
- Use solutions like Forescout that go beyond SPAN traffic and can provide vendor device and model details in order to tune granular controls through security policies.
Join the Forescout Community Discussion on controlling Cisco devices impacted by the CDPwn vulnerabilities: