The art of risk assessment has long been a crucial element of military strategy and decision-making – and it remains critical to today’s best practices in cybersecurity defense.
Abraham Wald, a mathematical genius, played a pivotal role in revolutionizing the understanding of hidden risk and exposure with his innovative work on aircraft survivability. During World War II, the US air force wanted effective methods to protect aircraft against enemy fire. Wald’s innovative approach stood out.
Unlike conventional ways of reinforcing heavily damaged and bullet-struck areas (Fig. 1), Wald analyzed data on returning aircraft with bullet holes and proposed something unique. He shifted attention to the untouched regions of those planes to reveal critical insights into where reinforcement was most needed.
Wald’s logic was irrefutable: The absence of bullet holes in certain sections of aircraft wasn’t due to luck. It was because the planes hit in those areas simply never made it back.
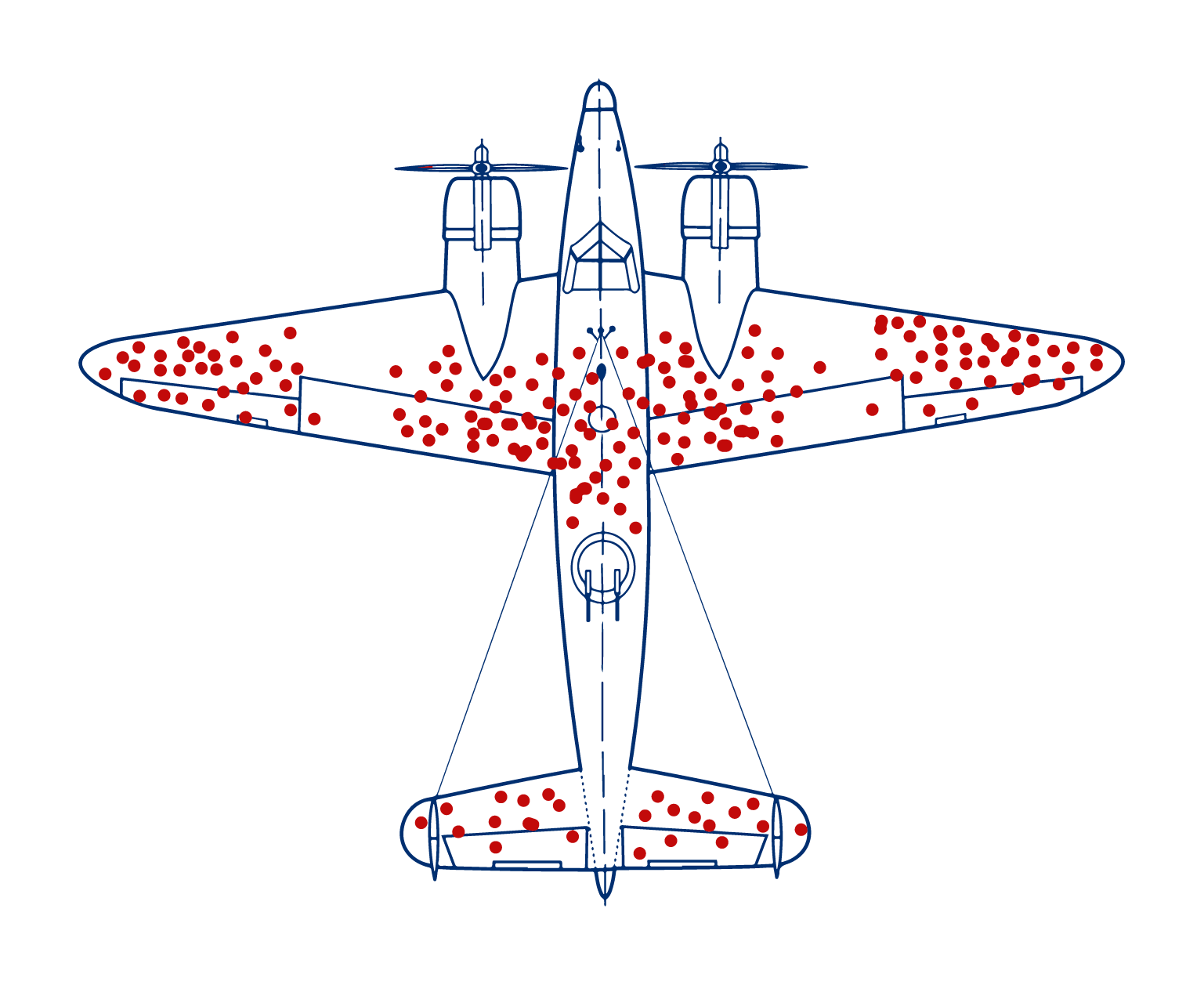
Wald’s ‘survivorship bias’ methodology offers a compelling analogy for today’s risk management. We need to think more strategically to gain a deeper understanding of risk – and not allow selective ‘success’ filters dissuade the mission. It’s time to accept there are hidden risks from limited visibility — and that hidden risks are a persistent threat to business and to human safety.
Targeting the Blind Spots in Cybersecurity
Today’s landscape is complex and constantly evolving, especially with the widespread use of Internet of Things (IoT) – and Operational Technology (OT). By 2028, connected IoT devices will expand to over 25 billion. They have significantly expanded the attack surface creating new challenges and vulnerabilities.
Uncovering blind spots is what Wald teaches us. By adopting his holistic approach to assess the entire situation rather than only visible damage, cybersecurity teams need comprehensive visibility. These blind spots may include unmanaged devices, including bring your own devices (BYOD) that connect and disconnect from the network — and third-party devices linked to the network.
With a clear view of all cyber assets, applications and networks, security professionals can identify potential vulnerabilities and exploitable weak points. Enhanced visibility promotes a more targeted and efficient cybersecurity strategy. With it, organizations can:
- Allocate resources more effectively
- Implement robust defenses more efficiently
- Proactively mitigate these blind spots before they become targets
Forescout’s Risk and Exposure Management (REM) solution can easily identify and classify all cyber assets and their exposure attributes giving real-time awareness of an entire organization’s attack surface (Fig. 2).
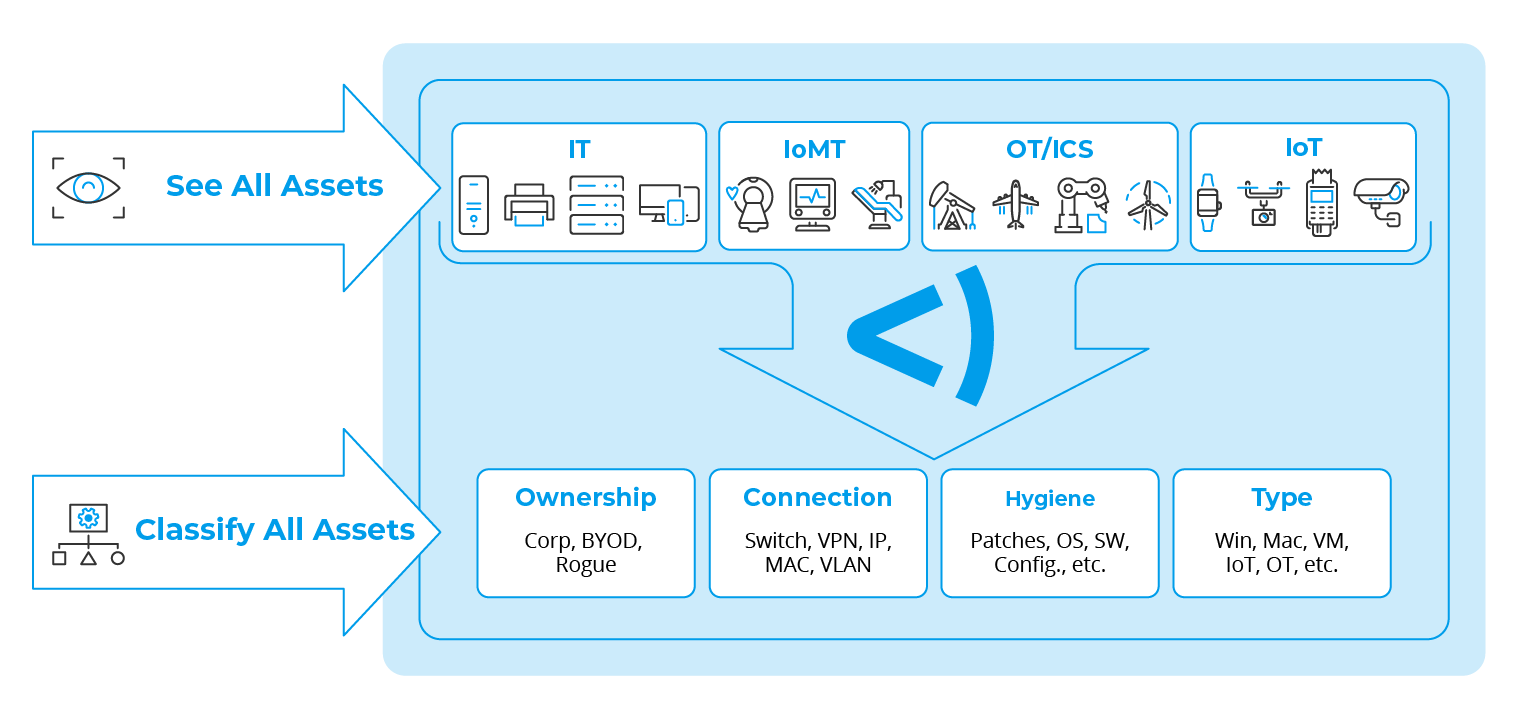
Our research shows there have been more than 420 million attacks per year at more than 13 attacks per second. Complete visibility is essential. Blindly strengthening cybersecurity defenses without full visibility is like reinforcing random sections of an aircraft without knowing where vulnerabilities lie —or where breaches are likely to occur.
Piercing the Risk Exposure Patterns
Traditional risk assessment methods struggle to capture dynamic risk and rely too heavily on historical data or visible incidents only. It may not fully represent emerging threats. By acknowledging where data gaps or biases exist, organizations can refine their assessment and mitigation strategies more effectively. Like Wald’s approach, security teams must move beyond surface-level assessments to quantify risk. It involves evaluating the likelihood of threats, leveraging threat intelligence feeds and implementing techniques using advanced analytics to uncover hidden patterns and anomalies.
Gartner predicts that organizations prioritizing their security investments based on ‘continuous threat exposure management’ will realize a two-thirds reduction in breaches by 2026. To achieve this level of risk reduction, it is incumbent on organizations to adopt proactive approaches, such as a risk scoring framework to assess all risk factors — including severity, likelihood of exploitation and potential impact on business operations.
A data-driven methodology like Wald’s allows organizations to prioritize decision-making based on the actual level of risk using probability and potential impact (Fig. 3).
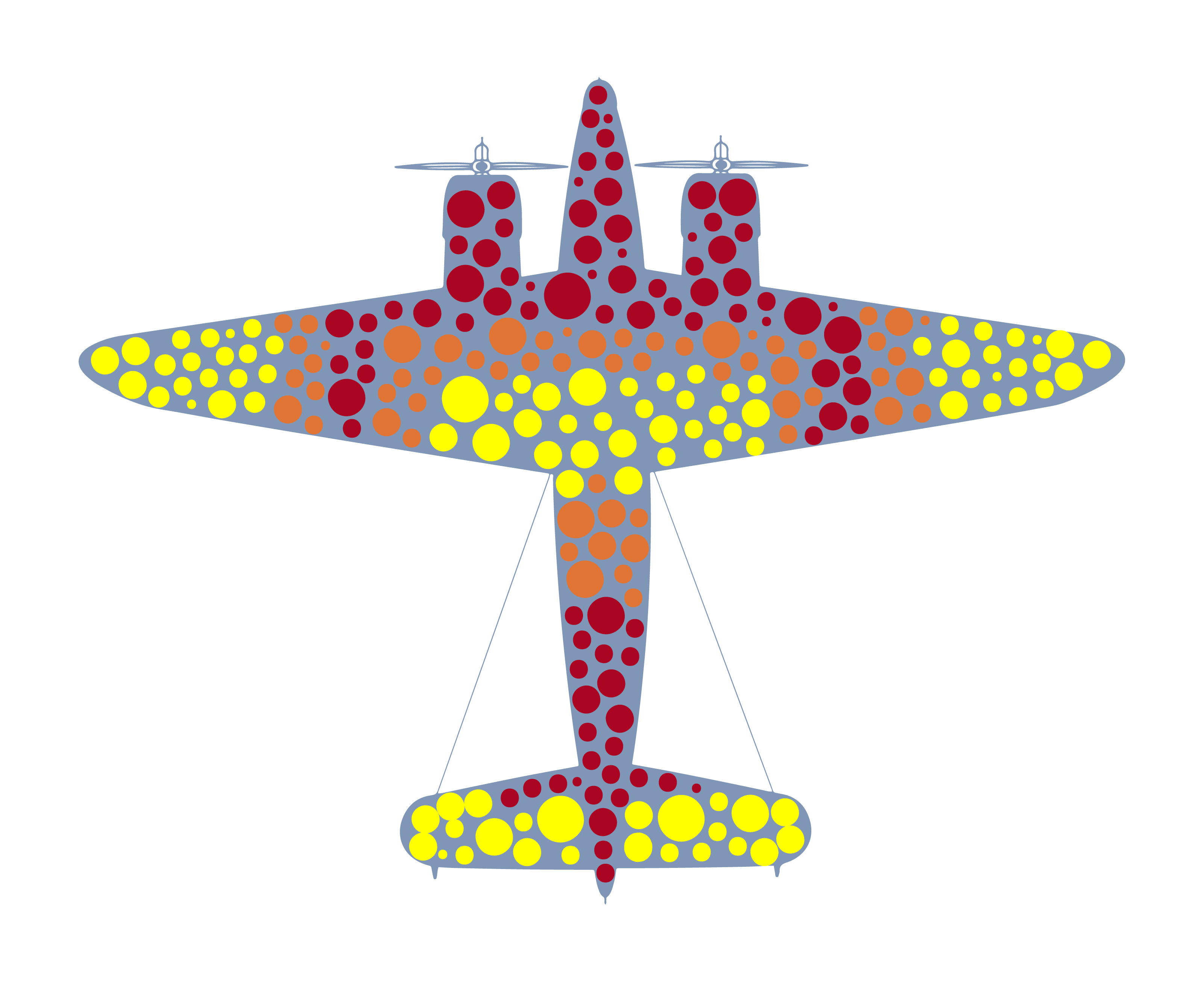
The Forescout REM solution correlates a wide range of asset exposure factors with asset criticality to facilitate prioritization based on a business risk score. It can identify all asset vulnerabilities and pinpoint which ones are actively exploited by attackers. Plus, it can assess the exposed services of each asset, identify configuration weaknesses, such as default credentials or insecure protocols — and detect compliance violations.
Bulletproof Risk Resilience Automatically
Organizations have realized how impractical it is to address every vulnerability and exposure within their environment. Wald’s advice on reinforcing vulnerable areas of aircraft to decrease damage risk mirrors the concept of actionable plans and workflows to reduce cybersecurity exposures.
An efficient risk mitigation strategy relies on a remediation approach that weighs the importance of assets or business functions against the likelihood or evidence of exploitation. This method not only helps in reducing vulnerabilities and averting potential threats but plays a crucial role in enhancing organizational resilience.
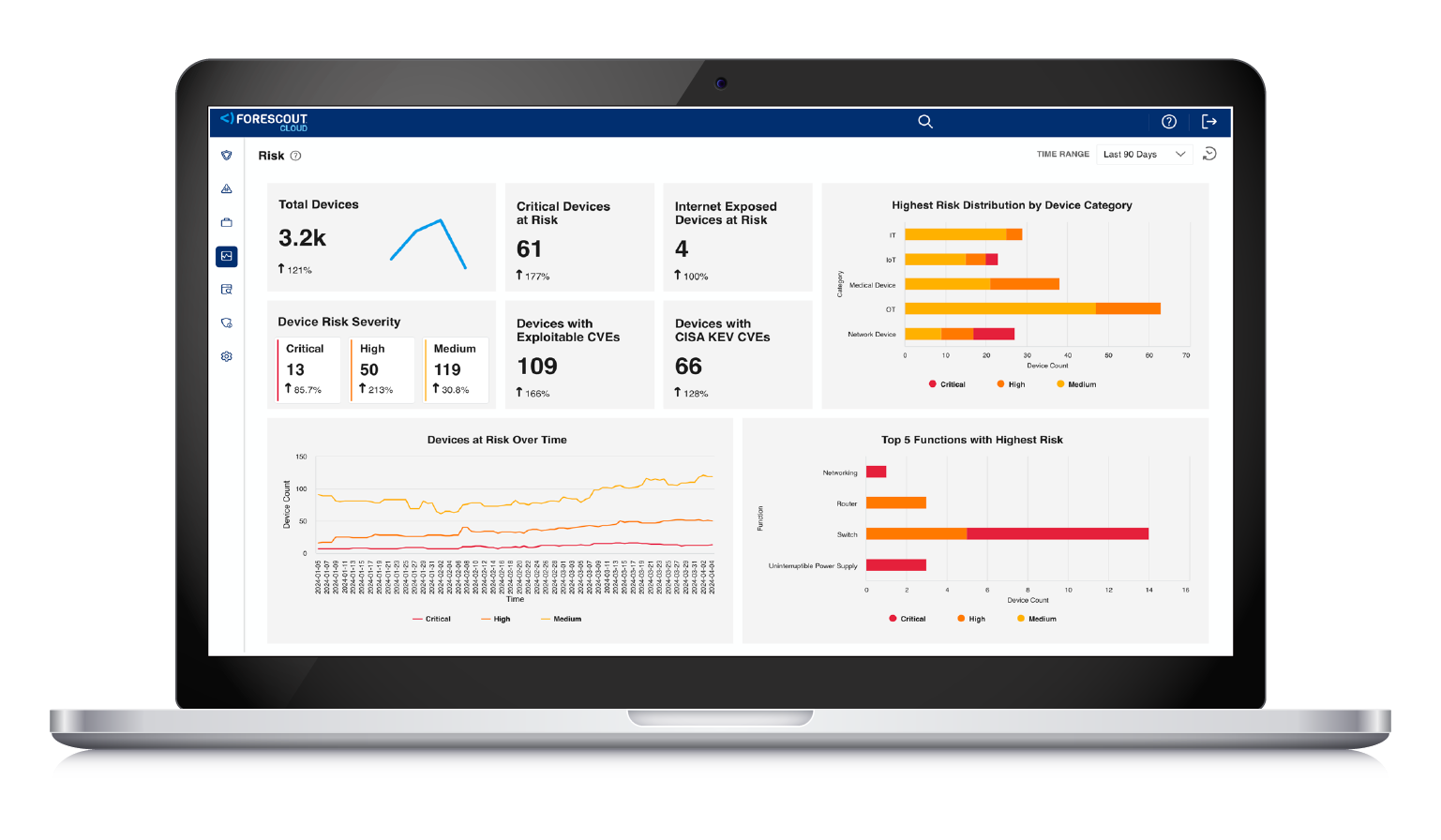
The Forescout REM solution helps users prioritize mitigation and remediation actions to offer the most significant return on investment by reducing risk. Through REM, organizations can assess and prioritize risks holistically and granularly — at the device level and across the entire organization (Fig. 4). Utilizing the Forescout platform capabilities, REM solution enables automated response actions based on the asset’s risk level allowing security teams to reduce risk and exposure efficiently.
Close Your Security Blind Spots with Forescout REM
In the complex dance of cybersecurity, the continuous cycle of identifying, prioritizing and minimizing exposures acts as the backbone of a resilient defense strategy. This dynamic process serves as a conduit for fortifying a resilient cybersecurity posture. Move beyond vulnerability management. Not only can you detect and mitigate current vulnerabilities, but you will adapt quickly to emerging cyber threats.
The Forescout REM solution is powerful and provides unparalleled visibility into the full spectrum of your connected network assets – managed or unmanaged. Identify all connected assets, including your most critical ones, using active or passive methods, from initial discovery to detailed classification. Eliminate the security guesswork with actionable recommendations to confidently close your exposure and compliance gaps with proactive controls.
Go deeper: Learn how to decode cyber risk and take action, today. Join Reza Koohrangpour on May 30 for “Closing the Gap: A Proactive Approach to Mitigating Risk”