On August 15, the Clop ransomware group announced on their leak website the breach of South Staffordshire Water, a privately owned UK water supply company.
This attack is yet another example of ransomware gangs targeting critical infrastructure expecting to receive a big payout, which is reminiscent of hundreds of previous incidents, including the well-known Colonial Pipeline and JBS attacks.
However, in this instance the attackers did not encrypt systems to prevent access to data or business continuity. They chose to use extortion techniques that are gaining popularity with cybercriminals: leak some of the exfiltrated data, publicly shame the victim and threaten further consequences if the ransom is not paid.
In brief, Clop posted on its website leaked documents and two screenshots of the SCADA system used to monitor and control South Straffordshire Water’s operations, which seems to corroborate the group’s claims that they could manipulate the level of chemicals in the water. However, the company may have compensating controls that would prevent the tampered values from being accepted by the system, and the pumps themselves may not be physically capable of accommodating the instructions. Moreover, now that the breach has been disclosed and incident response is underway, it is unlikely that Clop still has access to the systems.
In this blog post, we give a brief overview of Clop’s history, analyze what is known so far about the South Staffordshire Water incident and provide mitigation recommendations for other organizations.
Overview of the Clop ransomware group
Clop, also known as Cl0p, has been active since 2019, but their infrastructure was temporarily shut down in June 2021 following INTERPOL’s Operation Cyclone, which also arrested people involved in laundering money for the group in Ukraine. They remained inactive between the end of 2021 and beginning of 2022, but in April the group returned with 21 new victims announced on their leak site. Clop has been involved in several other attacks since then including global technology company Applexus on July 26, Middle Eastern supermarket chain Spinneys on July 20, Canadian technology company Pricedex on May 28 and American distributor of physical security systems ENS Security on May 27.
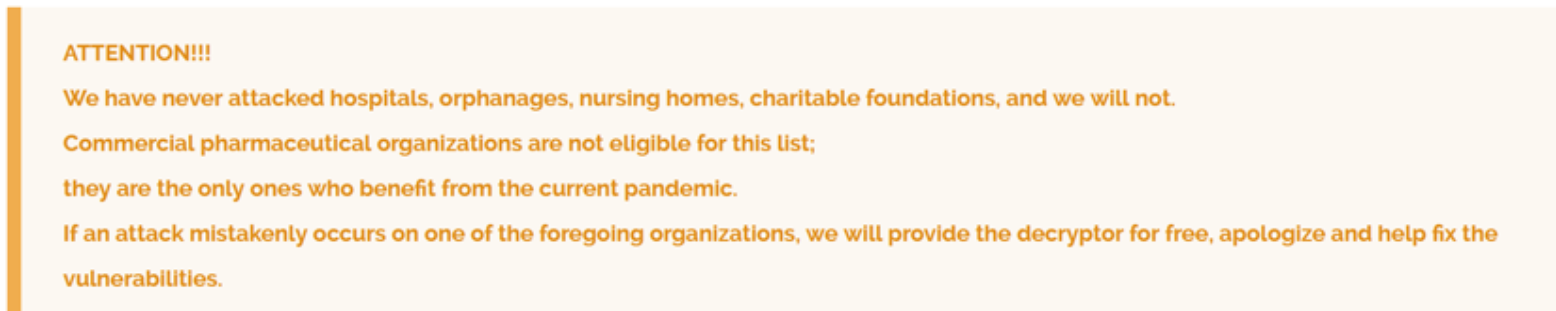
As shown in the figure below, taken from their leak site, the group claims to not target several types of organizations, including healthcare and charitable foundations.
The South Staffordshire Water cyber attack
It is not currently known how the attackers obtained access to the compromised systems and exactly what was the limit of their access. So far, they posted on their website a short description of the incident, several copies of stolen personal documents (such as passports and driver licenses possibly belonging to employees), and some screenshots containing system credentials as well as a view of the SCADA system used to monitor and control water treatment. Below, we analyze these leaked documents.
The files were originally published on the Clop website under the name “thameswater.co.uk.” It is not clear if Thames Water – which is a separate water utility in the UK – is another victim whose files have not yet been published, but the attackers later fixed their mistake and renamed the leak “south-staffs-water.co.uk.” Nevertheless, South Staffordshire Water has confirmed the incident via a public statement, while Thames Water has publicly denied being targeted by a cyber attack.
Clop claims to have spent months on the target’s systems, but they also claim to not attack critical infrastructure and therefore decided not to encrypt data. Instead, the leaked files are supposed to be proof of their access to more than 5TB of sensitive data and control systems.

The attackers said they proposed to disclose details of the breach and possible fixes to the company in exchange for a payment. They were then supposedly contacted by a company negotiator who offered an amount considered too low by Clop, which prompted the group to publicly announce the breach.
Besides personal information, the leaked files contain credentials to systems such as virtual machine servers, HR, payroll, ERP and other internal systems. All the systems mentioned were internal-facing and most of the passwords seem unique and randomly generated, which is indicative of good security practices – despite the attacker’s claims of bad security.
The most interesting leak is two screenshots of the SCADA system used to monitor and control water treatment. They show the “Advanced Graphic Workstation” developed by OPUS Software monitoring the Seedy Mill water works. The timestamp on the screenshots is 20 July 2022, which supports the group’s claims of having had access to the victim for months.
The leaked material shows that the attackers had access to both the IT and parts of the OT network of South Staffordshire Water, which indicates the company may have had weak segmentation policies between the two. This is typical in ransomware incidents targeting critical infrastructure.
Possession of the screenshots also seems to corroborate Clop’s claims that they could manipulate the levels of chemicals in the water, although this fine-grained control was not directly shown on the published screenshots, and South Staffordshire Water could have compensating controls that would prevent the tampered values from being accepted by the system.
SCADA system access and potential impacts
From the screenshots, it appears that the attackers had comprehensive access to the SCADA master station responsible for multiple sites including water distribution and treatment processes (UV, membrane filtration, etc.). Many of the screenshots shared depict mostly monitoring, but there also some clear controls, such as for manual override, alarm handling and initiating specific actions like requesting a wash. It is hard to tell whether some of the little labels are configurable setpoints rather than merely monitoring representations and whether a manual override will make them editable or not, though there are also some explicitly configurable setpoints such as for rinse pumps and DAF (dissolved air flotation) turbidity.
Water treatment processes are complex and have multiple steps, so tampering with one part, such as flocculation and coagulation, will likely not result in immediate issues and only lead to unwanted buildup in basins over a prolonged period or extra stress on subsequent filtration steps, which will strain various washing sequences but is not very likely to result in quick damage or affect water quality, though this depends on the specific process of course.
In addition, many setpoints for adding chemicals, even if not limited by the SCADA software or controller logic, are still limited by instrument constraints. Attackers can instruct a pump to put thousands of liters of lye or chlorine or other chemicals in some tank, but that doesn’t mean that the pump is physically capable of that much throughput. Typically, these pumps are not very high capacity, so attackers would likely have to wait a long time before buildup results in something with a noticeable effect, and they would have to spoof downstream sensors too.
More troubling is the ultrafiltration membrane process. These are very expensive filters, which are highly sensitive to overpressure and are often bottlenecks in the water treatment process. If these break, the process is disrupted and replacing them costs significant time and money. Whether these can be damaged depends on the pressure ratings of the filters and pump and backwash capabilities, but this could be a focal point if the attackers were to do serious damage.
Although the attackers may have had a chance to interact with the water treatment control systems in the past, now that the breach has been disclosed and the company is working on their incident response, it is unlikely they still have any significant access to the systems that would allow them to do so.
Mitigating cyber attacks targeting the water sector
The South Staffordshire Water attack is part of a series of incidents targeting the water sector in the past couple of years, which have increased the cost of cyber insurance for water utilities. In 2020, Israeli water utilities were targeted, possibly by hacktivists, for undisclosed reasons that prompted the government to issue an alert recommending the changing of passwords to operational technology (OT). In February 2021, an attacker obtained remote access to the system controlling the levels of sodium hydroxide used at a water treatment plant in Oldsmar, FL, and managed to change the settings to a deadly level, which was promptly detected and reverted by an alert employee. In March, July and August 2021, three U.S. water utilities were targeted by different ransomware groups. Now cybercriminals have obtained access to a UK water treatment control system with the intent of extorting the victim.
Although the incidents had different types of perpetrators and goals, similar mitigation efforts could help reduce the likelihood and the impact of potential cyberattacks targeting the water sector:
- Identify all devices connected to the network: IT, OT and IoT will all be targeted by attackers either for initial access, lateral movement in the network or to impact the business. Not having a complete and accurate inventory of devices creates security blind spots in the network.
- Enforce security compliance: Continuously monitor and enforce security compliance for all connected devices in your network. Noncompliant devices (devices with weak/default credentials, unpatched, legacy OS, etc.) are often the primary targets for attackers.
- Segment to mitigate risk: Devices directly connected to the internet are at most risk for initial access ,while those bridging IT and OT systems can be used to cross the perimeter. Network flow mapping of existing communications provides a baseline understanding of external and internet-facing communication paths. This can help identify unintended/anomalous external communications so appropriate segmentation controls can be enforced for mitigating risk.
- Monitor network communications: In addition to immediately reducing risk by taking mitigation actions, water utilities should continuously monitor the traffic to and from high-risk devices, so when anomalous traffic flows are detected, response actions or more stringent controls can be enforced.
Critical infrastructure is critical for a reason. Attacks on water treatment and control systems are not only cause for public alarm but a wakeup call for operators to up their cyber hygiene by following these basics.
Read how this major water and wastewater treatment company tackled compliance by improving asset management, network monitoring and segmentation, threat assessment and report capabilities across a complex IT-OT environment.