CYBERSECURITY A-Z
In today’s hyperconnected landscape, protecting your internal network is no longer a defensive measure — it’s a business-critical imperative. Threat actors are growing more sophisticated and are finding more vulnerabilities to exploit than ever before. At the same time, cloud infrastructure is reshaping network boundaries, and digital transformation is expanding the cybersecurity attack surface. To keep up, security teams need more than reactive controls. They need a strong, well-architected network security design.
This guide explores what network security design is, why it matters, and how to implement it using proven best practices. It breaks down common security design components such as perimeter defense, access control, and cloud security with actionable tips and real-world examples. Whether you’re starting from scratch or optimizing an existing environment, this guide will help you build security that’s proactive, scalable, and resilient.
What Is Network Security Design?
It is the structured approach to building cybersecurity into an organization’s network infrastructure. It involves planning, configuring, and managing the architecture, technologies, and policies that protect the confidentiality of digital assets from unauthorized access, data breaches, vulnerabilities and cyberattacks.
At its core, network security design ensures that security controls are strategically embedded throughout the network’s lifecycle. This includes perimeter security like firewalls, segmentation, and microsegmentation, identity and access controls, intrusion prevention systems (IPS), encryption, and zero trust policies.
“Security, risk, and trust models play into how networks are designed and deployed. If these models are not considered during network design, band-aids and workarounds will be deployed to achieve the needed goals, potentially bypassing network controls,” Info-Tech Research Group underscores.[i]
Instead of treating security as an afterthought, design-led security integrates protection from the ground up. The goal is not only to detect and respond to threats, but to reduce the likelihood of successful attacks by limiting exposure, managing access, and ensuring visibility across an organization’s infrastructure.
Why Network Security Design Matters
A well-designed network security architecture minimizes risk while enabling agility. When security is baked into the network, teams can:
- Close visibility gaps across IT, OT, and IoT environments
- Prevent lateral movement through segmentation and access controls
- Respond faster to threats and vulnerabilities with unified monitoring and automated enforcement
- Scale securely with cloud, hybrid, and remote workforce models
- Demonstrate compliance with regulatory mandates such as NIST, PCI-DSS, and ISO 27001
Without a strong design, organizations often face inconsistent enforcement, overlapping tools, and blind spots that attackers can exploit. Cybercriminals thrive in complexity. Effective network security design simplifies and hardens the environment to make that complexity work for the organization, not against it.
Design Principle: Build Security by Design
Security by design means integrating protection into the network from the start. This requires collaboration across IT, security, networking, and compliance teams.
Key components of security by design include:
- Zero Trust Architecture (ZTA): Operate on the principle that no user or device is inherently trustworthy. Enforce strong authentication, granular authorization, and ongoing verification of identity and device health.
- Defense in Depth: Layer multiple, complementary security controls—so if one is compromised, others can still block, contain, or slow an attack.
- Least Privilege Access: Limit permissions so users and systems can access only what is strictly necessary to perform their roles.
- Visibility and Monitoring: Integrate continuous asset discovery, network traffic monitoring, and behavioral analytics to detect issues in real time.
- Secure-by-Default Configurations: Disable unused features, close unnecessary ports, and apply hardened baseline settings to minimize exploitable gaps.
- Network Segmentation: Isolate systems using both physical segmentation (dedicated hardware) and logical segmentation (VLANs, software-defined networking). Micro-segmentation can further confine traffic flows and restrict an attacker’s lateral movement.
- Automated Threat Detection and AI Analytics: Leverage machine learning and behavior-based detection to uncover threats that traditional signature-based tools might miss.
- Security Orchestration, Automation, and Response (SOAR): Use automated workflows to correlate logs, execute containment actions, and streamline security incident response, reducing manual workload and human error.
- Continuous Visibility and Monitoring: Employ SIEM platforms, endpoint telemetry, and network traffic analysis to maintain situational awareness and accelerate threat mitigation.
- Data Loss Prevention (DLP): Monitor data transfers and enforce rules to stop sensitive information from leaving the organization unintentionally or maliciously.
- Regular Updates and Patch Management: Proactively patch operating systems, applications, and firmware to close security holes before they can be exploited.
Adopting security by design helps reduce reliance on detection and response alone, allowing teams to get ahead of threats.
How to Roll Out This Design: A Best Practice Implementation Process
A successful network security design rollout requires careful planning and phased execution. Below is a process modeled after proven best practices:
Baseline Assessment
Start by mapping the current state of your network. Identify assets, communication flows, vulnerabilities, and existing controls.
- Use network discovery tools to inventory connected devices, apps, and services.
- Conduct risk assessments for critical systems.
- Review firewall rules, access policies, and segmentation.
Define Security Requirements
Align stakeholders on business objectives and compliance mandates that will influence the design.
- Map regulations (e.g., NIST, HIPAA, PCI) to security capabilities.
- Identify areas requiring strict segmentation or data protection.
- Consider network types: enterprise IT, OT networks, cloud-native apps, remote endpoints.
Design the Security Architecture
Choose the right security model(s) for your environment:
- Zero Trust for user and device access
- Microsegmentation for east-west traffic control
- Perimeter defense for external threat prevention
- Cloud-native security for hybrid/multi-cloud environments
Build layered controls into each design zone: detection, authentication, access enforcement, encryption.
Implement Network Architecture Phase-by-Phase
Break the rollout into phases:
- Pilot in a non-critical segment or remote site
- Iterate based on feedback and telemetry
- Scale across data centers, cloud workloads, and remote offices
Use infrastructure-as-code (IaC) and policy-as-code where possible to reduce manual errors and increase consistency.
Monitor and Optimize
Establish ongoing monitoring and risk posture assessment:
- Deploy network detection and response (NDR), SIEM, and extended detection and response (XDR) tools for real-time insights
- Use threat intelligence and anomaly detection for adaptive defense
- Track KPIs such as policy violations, blocked connections, and attack surface reduction
Core Pillars of Security Design: Examples & Best Practices
Perimeter Defense
Perimeter security forms the outermost layer of defense, protecting the network from external threats. Common tools include firewalls, IPS, and web gateways.
Historically, organizations relied on perimeter firewalls to separate internal systems from the internet, blocking or allowing traffic based on IP, port, and static rules. Cloud migration, remote work, and SaaS apps have dissolved the old perimeter. NIST and others warn that trusting any device or user simply because it’s inside a corporate network is no longer viable.
Specifically, NIST says, “It is no longer feasible to simply enforce access controls at the perimeter of the enterprise environment and assume that all subjects (e.g., end users, applications, and other non-human entities that request information from resources) within it can be trusted.”[ii]
Best Practices:
- Use next-generation firewalls (NGFWs) that include deep packet inspection and application awareness.
- Deploy IDS/IPS tools with regularly updated threat signatures.
- Establish DMZ zones for public-facing applications to contain potential compromise.
- Inspect both inbound and outbound traffic to detect data exfiltration attempts.
- Conduct penetration testing to find out how effective your architecture works.
Access Control
Access control ensures that only authorized users and devices can connect to specific parts of the network.
Best Practices:
- Implement role-based access control (RBAC) and attribute-based access control (ABAC).
- Enforce multifactor authentication (MFA) across all endpoints and remote access.
- Use network access control (NAC) tools like the ones provided by Forescout to assess device posture before granting access.
- Continuously monitor for identity abuse or privilege escalation attempts.
Example Visual:
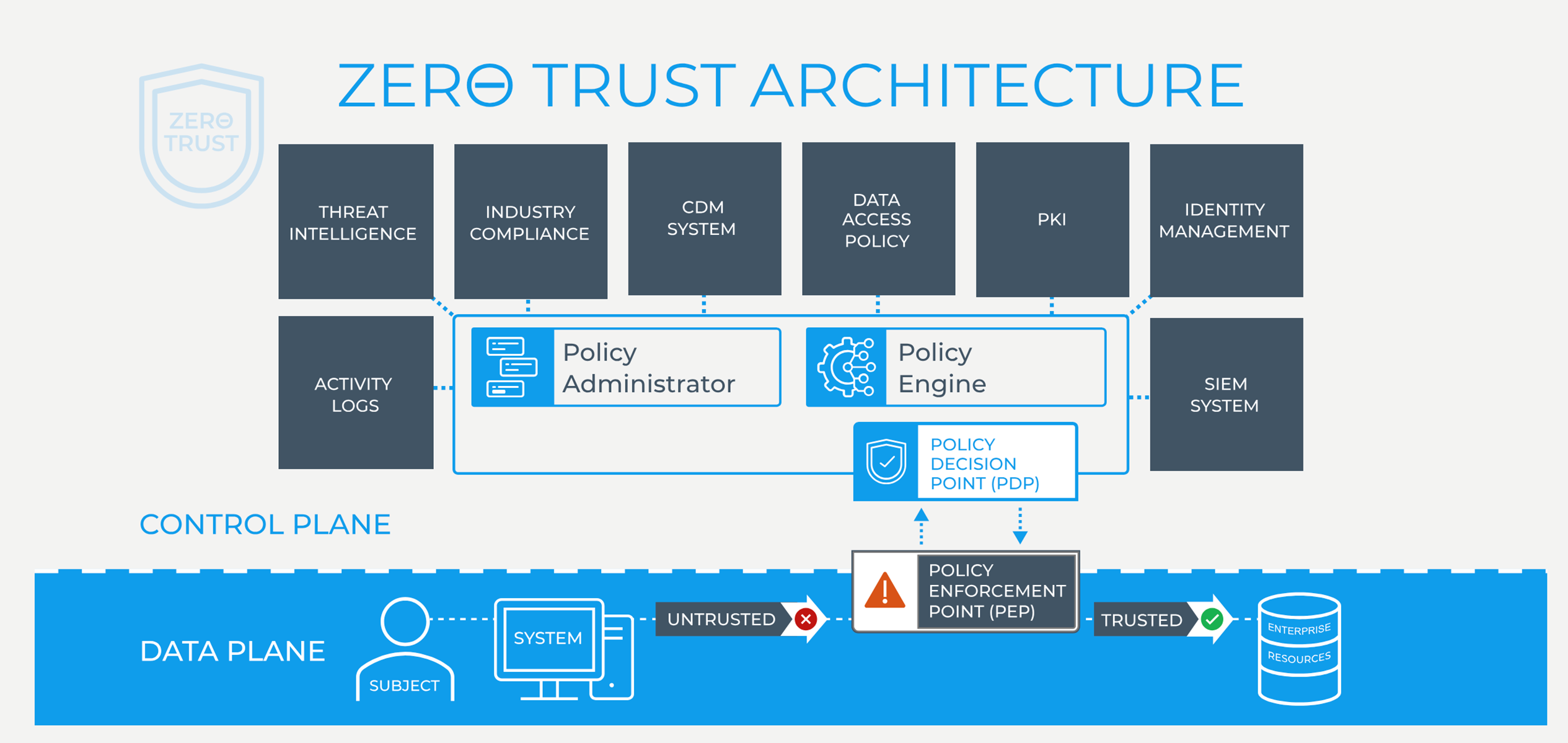
Cloud Security
Cloud environments introduce dynamic and ephemeral workloads that exist outside the traditional network perimeter, requiring cloud-native security controls.
Best Practices:
- Use cloud security posture management (CSPM) to detect misconfigurations.
- Enforce least privilege via IAM policies and service accounts.
- Encrypt data in transit and at rest.
- Use cloud workload protection platforms (CWPPs) to secure containers and VMs.
Example Visual:
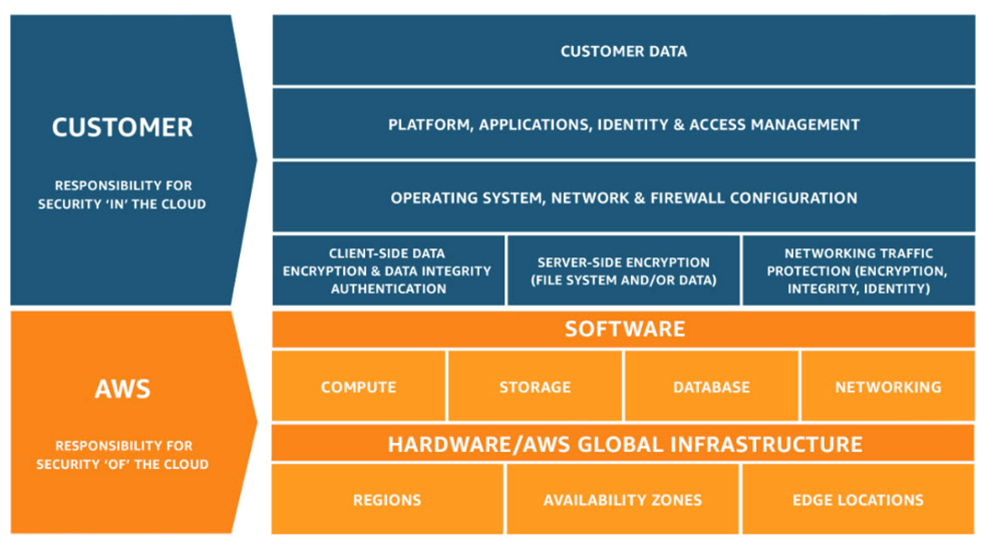
Addressing Common Network Security Design Challenges
Designing a secure network means tackling a range of evolving challenges head-on. Below are key issues that organizations often face, along with brief insights on how to address them:
| Challenge | Solution |
|---|---|
| Evolving Threat Landscape: Sophisticated threats like APTs, zero-day exploits, and ransomware constantly emerge, demanding timely detection and response. | Staying current—and proactively defending—is critical to prevent breaches and minimize business disruption. |
| Complex Networks & Device Sprawl: Modern environments span on-premises, cloud, IoT/OT, and legacy systems, creating a complex attack surface. | Ensuring visibility and security across all these domains is vital. Without simplification, gaps multiply. |
| Network Segmentation Difficulty: Dividing networks into secure zones is hard to plan, test, and enforce, especially without disrupting workflow. | Proper segmentation limits lateral movement and exposure, but must be carefully implemented to avoid outages. |
| Zero Trust Adoption Gaps: Lots of networks still trust devices/segments implicitly, even though modern threats can come from inside. | Zero Trust avoids that assumption by verifying every request and limiting access, enforcing least privilege. |
| Tool Overload & Visibility Gaps: Organizations juggle dozens of disparate tools, leading to blind spots, slow response, and misconfigurations. | Simplifying tool stacks and improving integration is essential to improve visibility and eliminate friction. |
| Talent & Budget Constraints: Skilled cybersecurity professionals are in short supply, and securing a wide-ranging network is expensive. | Limited talent and funds mean every control must be efficient, scalable, and easy to manage. |
Forescout’s Specific Capabilities
Forescout provides organizations with the tools to build and maintain robust network security across IT, OT, IoT, IoMT, and cloud environments. Forescout enables enterprises to operationalize security by design at scale, helping eliminate blind spots, reduce complexity, and meet regulatory compliance. Whether modernizing your network or migrating to the cloud, Forescout equips you with the visibility and control needed to reduce cyber risk across every domain.
Key capabilities include:
Continuous Asset Discovery & Classification
Forescout offers real-time, agentless discovery and classification of devices across IT, IoT, OT, IoMT, and cloud environments, providing full visibility, even for unmanaged or rogue systems. With over 12 million device fingerprints in the Forescout Device Cloud, it builds high–fidelity inventory and detailed contextual profiles (device function, OS, vendor, model, etc.) to eliminate blind spots and power accurate policy enforcement.
Segmentation & Policy Enforcement
Forescout enhances network segmentation by visualizing traffic flows, simulating policy changes, and continuously monitoring compliance. This intelligence supports zero trust design, restricting communication only between assets that need to talk while limiting threat blast radii as networks grow more complex.
Access Control & NAC
As a next-gen NAC solution, Forescout adopts an agentless, flexible approach that enforces policies across devices—including BYOD, IoT, and OT—without requiring software installation. It dynamically assigns devices to appropriate VLANs or applies ACLs based on posture and compliance, supporting least-privileged access while integrating with existing firewalls, switches, and SIEM tools.
Threat Detection & Response
Forescout correlates asset context across endpoints, network layers, and cloud environments to detect lateral movement and advanced threats. Its real-time inventory, combined with integrations into SIEM, EDR, and other tools, enables faster and more coordinated incident responses—adding an automated layer of defense rooted in visibility.
Automated Policy Enforcement
Forescout automates security policy enforcement via seamless integrations including firewalls, SIEMs, EDR, and cloud platforms, and adapts in real time to device posture or behavioral changes. When a device falls out of compliance, the platform can isolate or quarantine it automatically, helping enforce governance while minimizing human intervention.
Explore how Forescout can enhance your network security design.
[i] Info-Tech Research Group. Enterprise Network Design Considerations. Accessed August 11, 2025 from the following resource: https://www.infotech.com/research/ss/enterprise-network-design-considerations
[ii] NIST. NIST SPECIAL PUBLICATION: 1800-35B Implementing a Zero Trust Architecture, December 2022.