Customer Success with Zero Trust

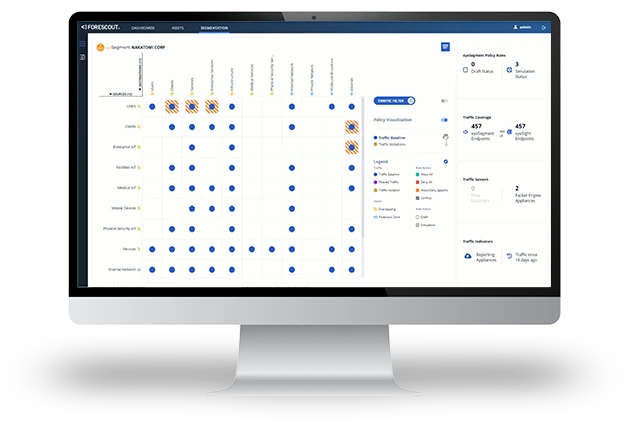
Learn More“To gain the functionality that Forescout provides – from seeing and managing assets to triggering control actions and accelerating zero trust segmentation – we would have needed multiple tools. Going with Forescout was far more cost-effective.”
— Jeff Haidet, Director of Application Development and Architecture, South Central Power Co.

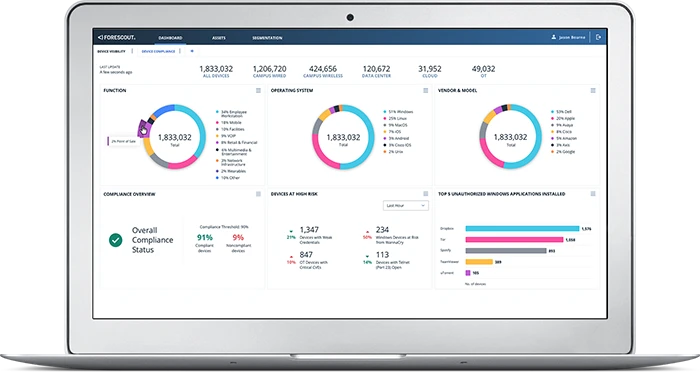
Learn More“When there is trust, there is speed. The Forescout Platform is invaluable because it provides the level of visibility that gives us that trust – trust that we know exactly what devices are on our network, along with the situational awareness both to be proactive and to address issues as they arise.”
— Chief Technology Officer, U.S. State Government Agency

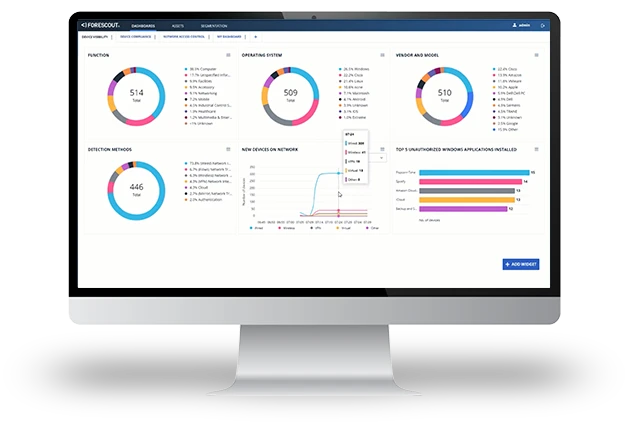
Read More“The real-time accuracy and completeness of the visibility that Forescout provides is what really impresses us.”
— Director of Security Operations, IT and Control Systems, American Energy Company