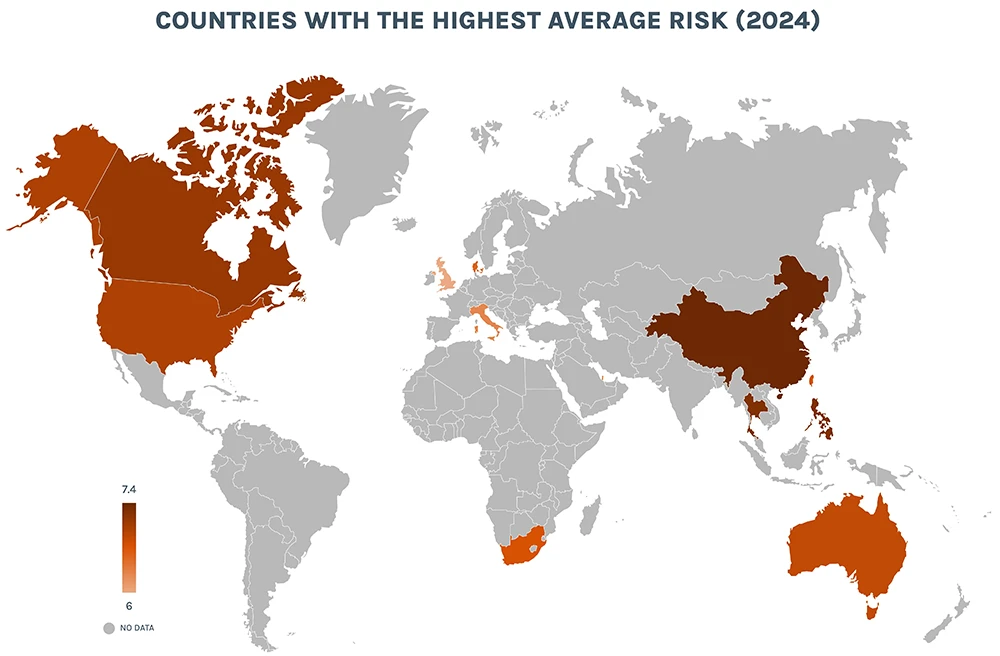
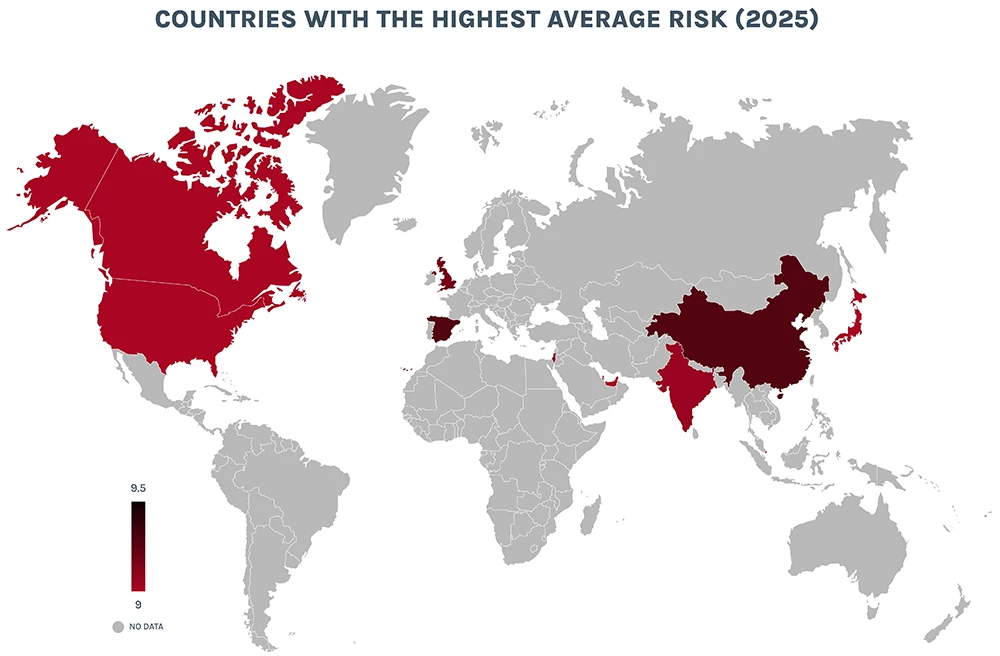
The Riskiest Devices of 2025
This year, a dozen brand-new asset types have made the list. It is the single largest year-over-year change observed in the report’s history. We analyzed industry, country, and device data taken directly from Forescout’s Device Cloud — one of the largest global repositories of IT, OT, IoT, and IoMT data in existence.