CYBERSECURITY A-Z
What Is IoT Security?
IoT (Internet of Things) security is the process that makes IoT and all IP-connected devices visible and controllable. In today’s digitaxl terrain, where countless internet-enabled sensors and specialized devices connect and intersect, organizations need a cybersecurity solution that makes all devices visible and controllable. Otherwise, any device can be compromised and exploited for malicious purposes.
The number of IoT devices worldwide is forecast to almost double from 18 billion in 2024 to more than 32 billion in 2030. Major industries that have already deployed more than 100 million IoT devices include: Electricity, gas, government, retail and wholesale, steam and a/c, transportation and storage, and water supply and waste management.i
What Are the Security Risks of IoT Devices?
As highly valuable and often critical corporate assets in a digital ecosystem, these devices boost productivity, enhance product and service quality, and improve the bottom line. But they are also susceptible to cyberattacks and malware because they often exist invisibly on enterprise networks – and many were not designed to be secure.
Unlike with traditional systems, these devices can be more difficult to track, and they rarely support software agents. As a result, they expand an organization’s attack surface and greatly increase cyber risks with attackers often targeting them as entry points into vulnerable networks.
Even when IT is aware of these devices on the network, they often struggle to patch and manage each one — and can be compromised directly via authentication due to weak passwords, default settings, poor configurations, or unpatched firmware and specialized operating-system vulnerabilities.
The Cybersecurity & Infrastructure Security Agency (CISA) noted that the many cybersecurity and resilience risks involving IoT devices are not new. However, CISA states, “the scale of interconnectedness created by the IoT increases the consequences of known risks and creates new ones. Attackers take advantage of this scale to infect large segments of devices at a time, allowing them access to the data on those devices or to, as part of a botnet, attack other computers or devices for malicious intent.”ii
Which IoT Devices Pose the Greatest Risk?
In 2025, the riskiest devices include several persistent threats from previous years and one newer one within the attack surface, according to Forescout’s annual Riskiest Devices report.
Network Video Recorders, VoIP Systems, IP Cameras
These remain high-risk because they are often exposed to the internet, contain easily exploitable firmware vulnerabilities or their authentication process can be easily bypassed, so they have a long history of being targeted by criminal botnets and Advanced Persistent Threats (APTs).
NAS Systems
These network-attached storage systems share the same risks as other devices – internet exposure, firmware vulnerabilities, and frequent exploitation. However, they face an additional threat from ransomware actors. Since 2021, with the advent of QLocker, ransomware groups have increasingly targeted NAS systems. Today, multiple ransomware families are specifically designed to infect NAS devices with malware, exploiting the valuable data they store and their security weaknesses.
Point of Sale Devices
These process customer transactions, such as sales in retail stores. They may run traditional IT operating systems (e.g. Windows) or dedicated embedded OSes. These devices have long been prime targets for cybercriminals, who deploy keyloggers and infostealers to capture sensitive data. Additionally, RAM scrapers scan the system’s memory for credit card numbers and payment data before encryption. Certain PoS devices also contain specific vulnerabilities that attackers can exploit to gain deeper system access.
Riskiest Device Categories
| IT | IoT | OT | IoMT | |
|---|---|---|---|---|
| 1 | Application Delivery Controller (ADC) | Network Video Recorder (NVR) | Universal Gateway | Imaging Devices |
| 2 | Intelligent Platform Management Interface (IPMI) | Network Attached Storage (NAS) | Historian | Lab Equipment |
| 3 | Firewall | VoIP Systems | Building Management System (BMS) | Healthcare Workstations |
| 4 | Domain Controller | IP Camera | Physical Access Control Systems | Infusion Pump Controller |
| 5 | Router | Point of Sale (PoS) Systems | Uninterruptible Power Supply (UPS) | Picture Archiving and Communication System (PACS) |
Past Reports on Device Risk
IP cameras, VoIP and video conferencing systems often show due to internet exposure and have a long history of threat actors targeting them. For example:
- In 2019, compromised VoIP phones allowed attackers to gain initial access to multiple networks.
- In 2021 IP cameras allowed Conti malware to move within affected organizations.
- In 2022, both threat actors UNC3524 and TAG-38 targeted video conferencing and cameras for use as command and control infrastructure.
ATMs
ATMs have also appeared on our annual list because of their obvious business criticality in financial organizations and because many ATMs stand adjacent to, other devices, such as security cameras and physical security systems that are often exposed.
Printers
Printers present vulnerability risks, including multifunctional printing and copying devices used in the connected office, as well as specialized devices for printing receipts, labels, tickets, wristbands, and other items. Like IP cameras, printers have been exploited in intrusions by threat actors, such as APT28, and spammed by hacktivists on multiple occasions. They often connect to sensitive devices, such as point-of-sale (POS) systems (think receipt printers) and conventional workstations with privileged users, including office printers.
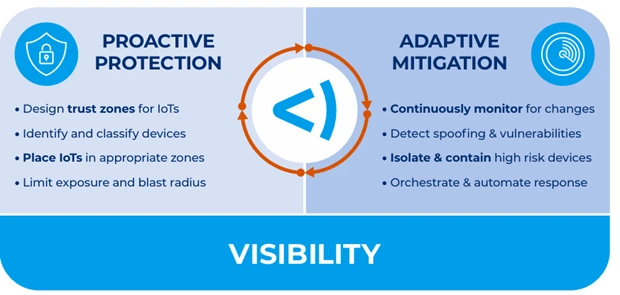
IoT Security Best Practices
These devices require the following essential practices to prevent potential threats including:
- Discover and classify 100% of IP-connected devices: It’s essential to obtain complete visibility and device context of all IoT endpoints across your network environment. To do this, use a cybersecurity platform that can discover all devices as soon as they enter your network. Since you must discover all devices, the technology you leverage should provide for devices that do not allow for agents. Agentless discovery will ensure that you capture everything.
- Implement dynamic network segmentation and controls: Proper IoT security requires network segmentation and orchestrated incident response across all domains. To do this, you must be able to:
- Correlate access with user identities (who is doing what, where, when and why)
- Provision devices to dynamic network segments based on policies and real-time context
- Map data flows to design segmentation policies and simulate them for non-disruptive deployment
- Automate segmentation to reduce security and operational risk
- Orchestrate security and enforce compliance: Rather than using traditional, expensive, single-purpose security solutions that cannot share knowledge or coordinate incident response, leverage a security solution that can share device context with other IT and security products. This will enable you to automate workflows and policy enforcement across disparate solutions. The benefits of taking this step include:
- Increase security and overall device compliance
- Reduce mean time to detect and respond
- Increase ROI from your existing tools
- Streamline updates to your configuration management database (CMDB)
How Forescout Helps
Forescout takes a Zero-Trust approach by combining complete device visibility, proactive network segmentation, and least-privilege access control of all digital assets – devices, users, apps, and workloads. The Forescout 4D Platform™ enables you to effectively manage cybersecurity, operational, and compliance risks across your environment by:
- Providing complete visibility into unmanaged IoT devices as well as all IP-connected systems
- Assessing and identifying IoT devices with factory-default or weak credentials and automating policy actions to enforce strong passwords
- Providing real-time insight into IoT devices’ communication and risky behavior across the extended environment
- Segmenting devices into trusted zones by enforcing least-privilege access by zero trust policy
- Automating unified zero trust policy orchestration across multivendor environments and multiple network domains
- Eliminating security management silos to accelerate response and maximize the value of your investments in other security solutions
- Helping your organization proactively detect and reduce vulnerabilities and granularly enforce segmentation and network access rules, and immediately contain IoT device threats while facilitating remediation
Expert in Assessing IoT Device Risk
As part of the Forescout 4D Platform™, Multifactor Risk Scoring works to further your efforts in assessing and governing your IoT devices with comprehensive risk profiles. Multifactor risk scoring gives your security operations center (SOC) the advantage of working on the vulnerabilities and exposure in your current security framework that misalign it from your desired compliance state. Instead of working feverishly on volume, you work on criticality to your network. Forescout device risk scores result from three main factors:
- CONFIGURATION: Number and severity of vulnerabilities on the device as well as the number and criticality of open ports
- BEHAVIOR: Reputation of inbound connections to – and outbound connections from – the device, along with its internet exposure
- FUNCTION: Potential impact to the organization if the device is compromised
Forescout offers an asset-centric approach to IoT. This helps you create a proactive strategy to deal with your network’s vulnerability effectively and efficiently at scale.
To learn more, visit www.forescout.com/solutions/iot-security/.
[i] Lionel Sujay Vailshery, Statista (2024). Number of Internet of Things (IoT) connections worldwide from 2022 to 2023, with forecasts from 2024 to 2033, September 11, 2024. Statista. Accessed March 19, 2025 from the following source: https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/
[ii] CISA (2021). Securing the Internet of Things (IoT), February 1, 2021. Accessed March 19, 2025 from the following source: https://www.cisa.gov/news-events/news/securing-internet-things-iot