Forescout Vedere Labs has identified a total of 21 new vulnerabilities affecting Sierra Wireless AirLink cellular routers and some of its open source components such as TinyXML and OpenNDS, which are used in a variety of other products.
This new research confirms some trends that we have been tracking:
- Vulnerabilities on routers and network infrastructure are on the rise. Vulnerabilities on network infrastructure have consistently ranked among the most exploited since at least 2020; state-sponsored actors have been developing custom malware to use routers for persistence and espionage, while cybercriminals are leveraging them for residential proxies and to form botnets. Although most organizations are aware of the attack surface on their IT network infrastructure, many OT/IoT edge devices may not receive the same level of attention from security teams.
- Vulnerabilities in OT/IoT devices often arise from design flaws, such as the use of hardcoded credentials and certificates we saw in this research and previously in OT:ICEFALL, or issues when parsing malformed packets (see CVE-2023-41101 in this research and the many we saw previously in Project Memoria). These latter vulnerabilities are easier to exploit in OT/IoT devices because of the lack of effective exploit mitigations.
- Supply chain components, such as open-source software provided by third parties, can be very risky and increase the attack surface of critical devices, leading to vulnerabilities that may be hard for asset owners to track and mitigate.
Finding so many new vulnerabilities on software components of a well-studied device shows that device manufacturers, and in turn asset owners, must pay special attention to risks stemming from the software supply chain, both from open- and closed-source components. Asset owners are the ones who, at the end, may get breached due to insecure devices on their networks and, currently, they must either depend on device manufacturers to adequately address supply chain vulnerabilities or implement their own risk mitigation strategies that do not rely exclusively on patching. The former option is risky, since as we observed 2 years ago when concluding Project Memoria, legacy software components enable the connected world, vulnerability notification to a large number of parties is difficult and vendors/maintainers are often unresponsive, which means that organizations across several industries may remain vulnerable for a long time. The latter option – risk mitigation – is more broadly applicable and can lead to an overall better security posture against new and old vulnerabilities in critical devices.
Details of the vulnerabilities are available in the accompanying technical report. In this blog post, we summarize the research findings and discuss mitigation options for affected organizations.
The importance of OT/IoT routers
OT/IoT routers are used to connect critical local networks to the Internet via cellular connections such as 3G and 4G. The figures below show one of these routers connecting a remote surveillance camera for video streaming.
These devices are found in multiple critical infrastructure sectors, such as government and commercial facilities, emergency services, energy, transportation, water and wastewater systems, manufacturing and healthcare. Sierra Wireless is the most popular vendor of these types of devices.
Summary of findings
We found 21 new vulnerabilities affecting OT/IoT routers. One has critical severity (CVSS score 9.6) and nine have high severity. These vulnerabilities may allow attackers to steal credentials, take control of a router by injecting malicious code, persist on the device and use it as an initial access point into critical networks. The vulnerabilities are categorized as follows:
- Remote Code Execution (RCE) vulnerabilities allowing attackers to take full control of a device by injecting malicious code.
- Cross site scripting (XSS) vulnerabilities that may be used to inject malicious code on clients browsing the management application, thus potentially stealing credentials.
- Denial of service (DoS) vulnerabilities that may be used to crash the management for a variety of reasons, from simple vandalism to more sophisticated multi-staged attacks.
- Unauthorized access, via design flaws, such as hardcoded credentials and private keys and certificates, which can be used for performing man-in-the-middle attacks or to recover passwords by capable attackers.
- Authentication bypasses that allow attackers to skip the authentication service of the captive portal service and connect to the protected WiFi network directly.
Impact
We found more than 86,000 of these routers exposed online in organizations such as power distribution, a national health system, waste management, retail, and vehicle tracking. Less than 10% of the total exposed routers are confirmed to be patched against known previous vulnerabilities found since 2019. For devices exposing a specific management interface (AT commands over Telnet), we see that 90% are end of life, which means they cannot be patched anymore.
Numbers of exposed devices that run ACEmanager versus the security patch status of the underlying ALEOS versions
More than 22,000 exposed devices use a default SSL certificate (one of the vulnerabilities we identified – CVE-2023-40464), which allows for man-in-the-middle attacks to hijack or tamper with data in transit to and from the router.
On Forescout Device Cloud, we see Manufacturing and Healthcare as the most affected industries.
Distribution of Sierra Wireless routers by industry seen on Forescout Device Cloud
Attackers could leverage some of the new vulnerabilities to take full control of an OT/IoT router in critical infrastructure and achieve different goals such as network disruption, espionage, lateral movement and further malware deployment. For instance, attackers could take control of a router in a healthcare facility to attack devices of patients, guests or staff and distribute further malware. In a manufacturing scenario, attackers could take control of a router within a plant to attack industrial equipment.
Apart from human attackers, these vulnerabilities can also be used by botnets for automatic propagation, communication with command-and-control servers, and the launch of DoS attacks. In fact, previous botnets such as IoTroop/Reaper have targeted exposed Sierra Wireless routers via default credentials and 0-days.
Mitigation recommendations
Complete protection against the new vulnerabilities requires patching devices that run the affected software. The OpenNDS project has released OpenNDS 10.1.3, which contains fixes for all reported vulnerabilities. TinyXML is an abandoned open-source project, so the upstream vulnerabilities will not be fixed and must be addressed downstream by affected vendors.
Sierra Wireless has released the following ALEOS versions to address the new vulnerabilities:
- ALEOS 4.17.0 containing fixes for all relevant vulnerabilities.
- ALEOS 4.9.9 containing applicable fixes, except for OpeNDS issues since that version does not include OpenNDS.
In addition to patching, we recommend the following actions:
- Change the default SSL certificate for Sierra Wireless routers and any other device in your network that relies on default certificates.
- Disable captive portals and other services such as Telnet and SSH if they are not needed, or limit the access to those services if they are needed.
- Consider deploying a web application firewall in front of OT/IoT routers to prevent exploitation of web-based vulnerabilities, such as many of the XSS, command injections and DoS found in this research.
- Deploy an OT/IoT-aware intrusion detection system (IDS) to monitor both the connections between external networks and the routers as well as connections between the routers and devices behind them. This helps to detect signs of initial access leveraging the router as well as signs of attackers using the router to further exploit critical devices.
For previous vulnerabilities on Sierra Wireless products (1, 2, 3), the vendor and CISA have recommended the following, which should also apply for the new vulnerabilities:
- Always use strong, unique and random credentials for devices. If Telnet or SSH is enabled, ensure a strong password is set for the console accounts.
- Disable access to ACEManager on the wide area network (WAN) and use the Sierra Wireless Airlink Management System (ALMS) or an alternative device management platform for remote management of ALEOS devices.
- If the ACEManager must remain accessible via the WAN, restrict access using measures such as Private APN, VPN, or the ALEOS Trusted IP feature (restricts access to specific hosts).
- When connecting to ACEManager, use only HTTPS.
- Locate control system networks and remote devices behind the routers and isolate them from business networks.
How Forescout can help
Passive vulnerability matching, which allows for risk assessment and segmentation decisions, was added to the CVE database for Forescout eyeInspect and Forescout Risk and Exposure solutions.
Forescout eyeInspect customers can download the latest vulnerability bundle and install it locally to detect vulnerable devices on their networks. Forescout Risk and Exposure customers benefit from real-time deployment of content on the cloud, so they can detect vulnerable devices just by searching for specific CVEs on their dashboard.
The figures below show a Sierra Wireless router with the matched vulnerabilities and an associated security risk value on eyeInspect.
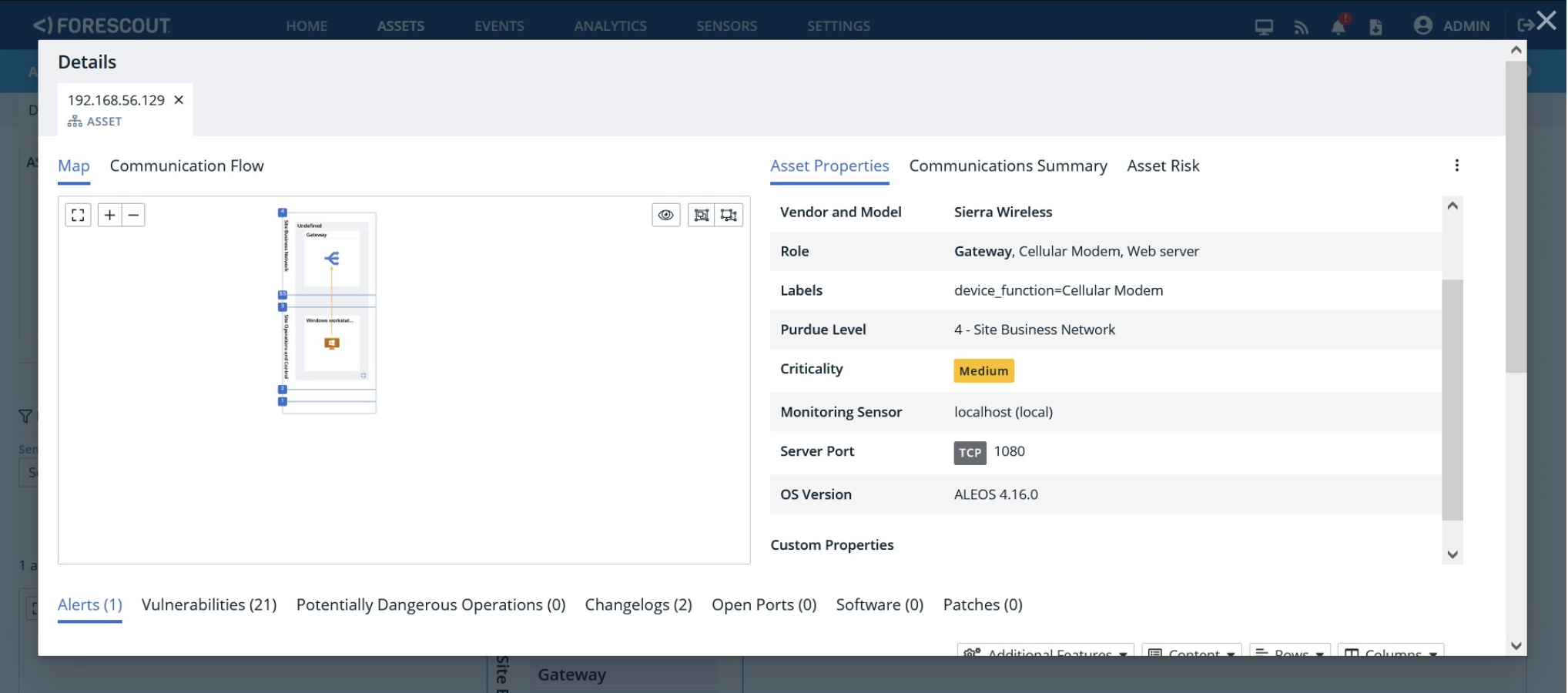
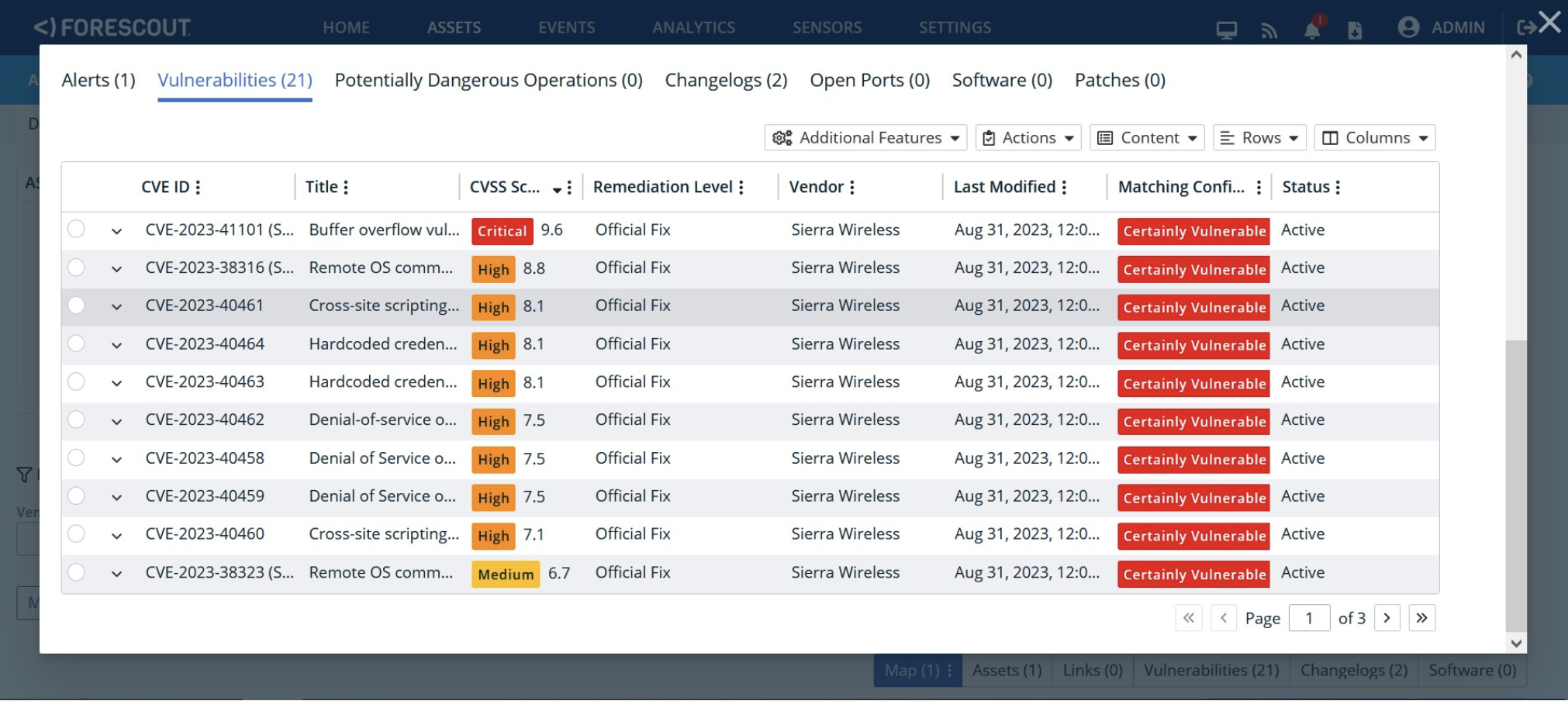
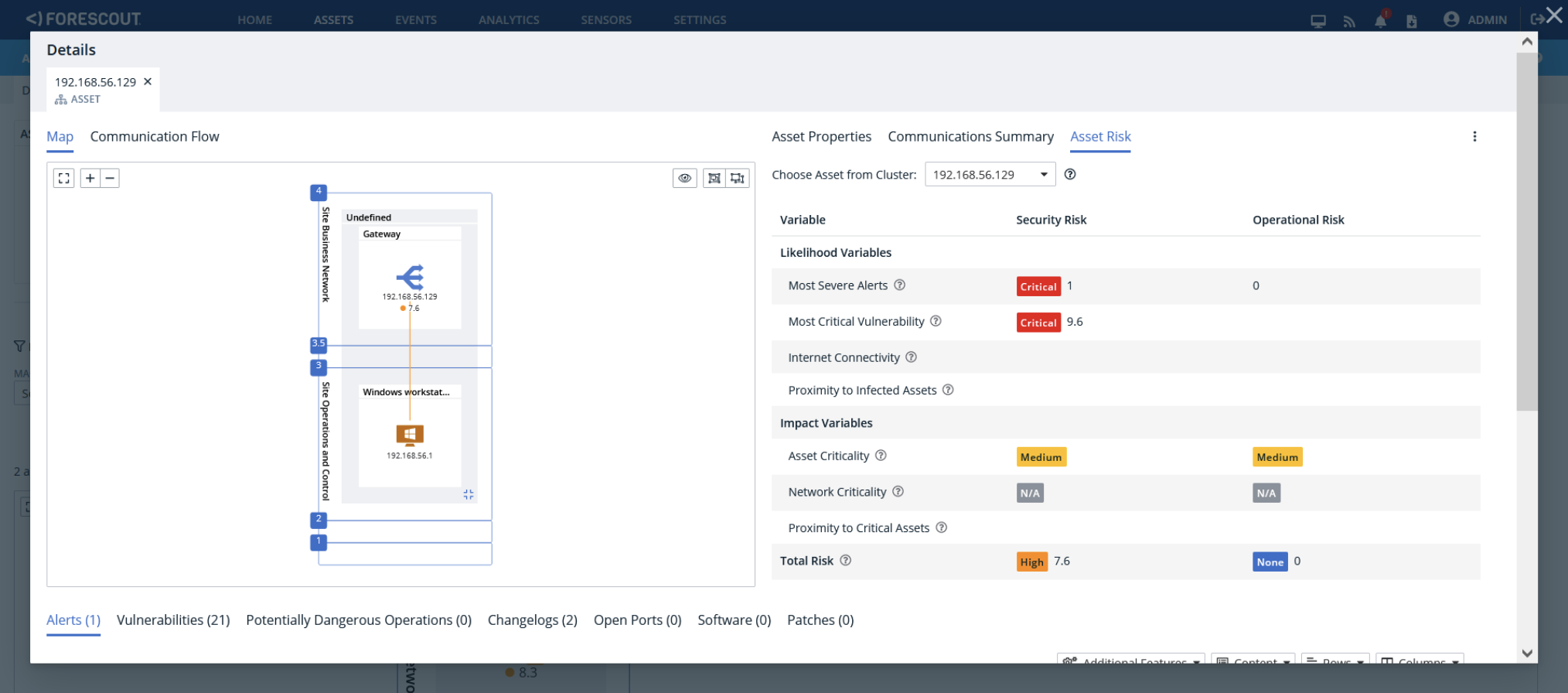
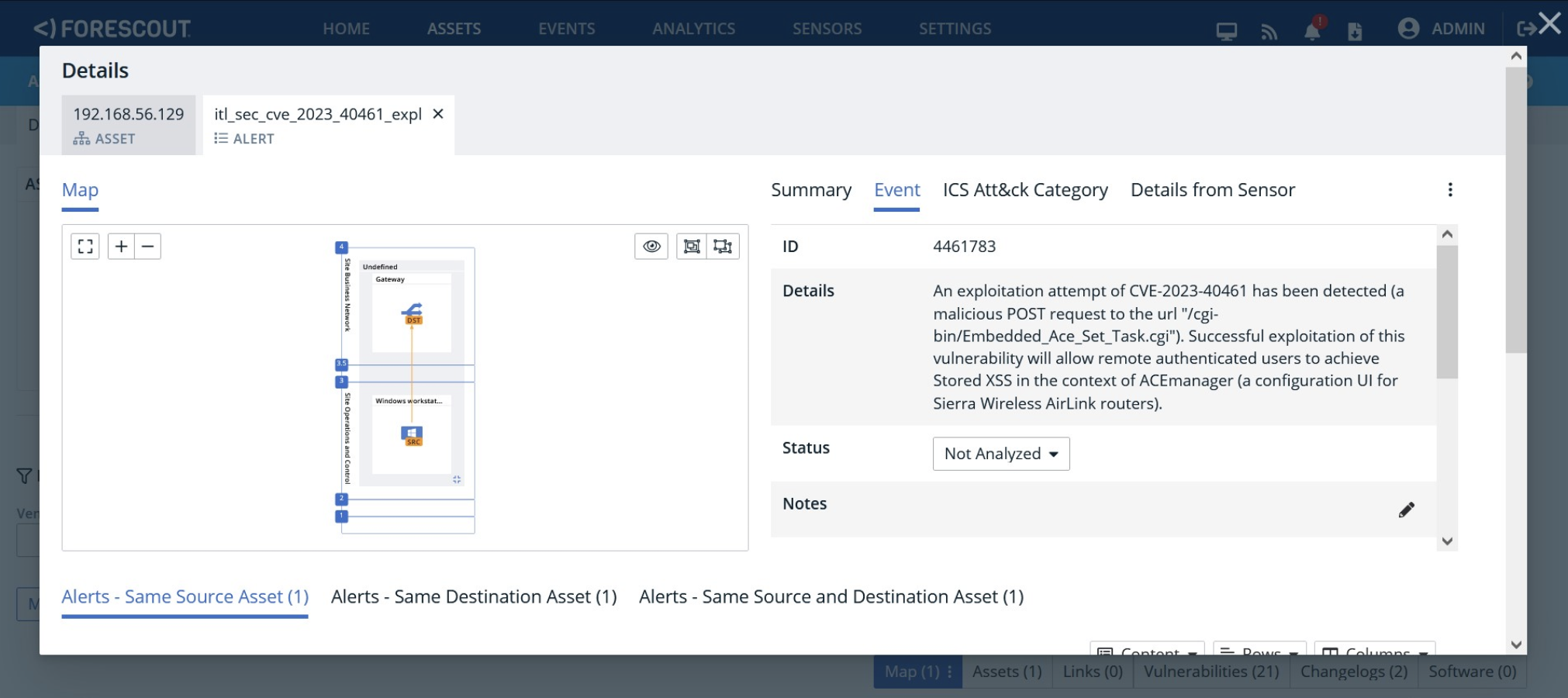
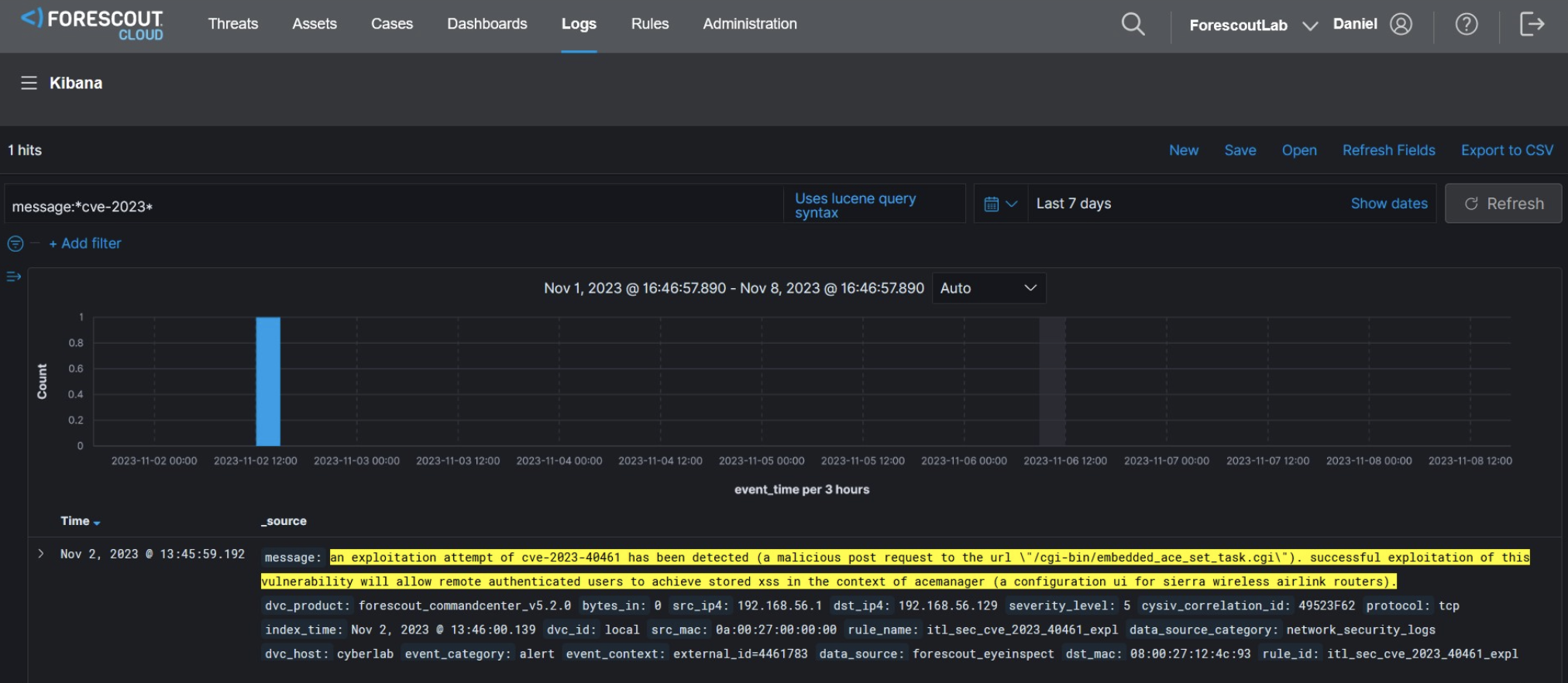
Forescout eyeInspect can also detect exploitation attempts against Sierra Wireless devices using the new ACEmanager Monitor script, which must be downloaded and locally installed. The figure below shows an alert raised by eyeInspect when it detects an a^empt to exploit CVE-2023-40461 against a Sierra Wireless router.
eyeInspect detections can be forwarded to Forescout Threat Detection & Response, where they can be automatically correlated with telemetry and logs from a wide range of sources such as security tools, applications, infrastructure, cloud and other enrichment sources, to generate high-fidelity threats for analyst investigation. The figure below shows the eyeInspect alert as seen on the Forescout Threat Detection & Response interface.
Finally, Threat Detection & Response detections can be sent to Forescout eyeControl via the “Cloud Data Exchange” plugin so that eyeControl can take automated remediate or restrict ac5ons based on user-defined policies.
