Key Findings
- The migration to post-quantum cryptography is underway but it is uneven, creating a future compliance and cybersecurity risk.
- Current Progress:
- About 6% of all 186 million SSH servers on the internet already use quantum-safe encryption.
- That percentage reaches over 20% if we consider only OpenSSH servers.
- Between October 2024 to March 2025, adoption grew :
- 554% for SSH key exchange with ML-KEM (a NIST standard)
- 21% for SSH key exchange with SNTRUP (an early PQC method)
- Why Growth Will Slow:
- As most early adopters migrate to quantum-safe technologies that rate of growth is expected to decrease.
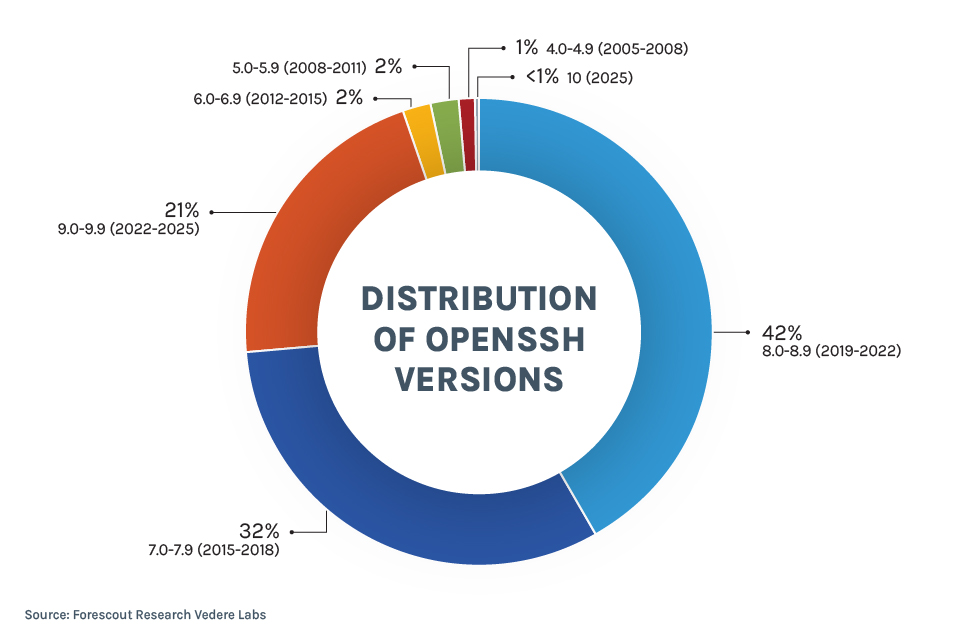
- Three quarters of OpenSSH versions on the internet still run versions released between 2015 and 2022 that do not support quantum-safe encryption.
- Less than 20% of TLS servers use TLSv1.3, which is the only version that supports PQC.
- What This Means for Business:
- If regulators mandate quantum-safe encryption in the near future, organizations will face serious gaps.
- Outdated infrastructure will become a compliance and security risk.
- Upgrading later may be slower, more expensive, and more disruptive than acting early.
Mitigation Recommendations
- Organizations need to start preparing for the migration as it will soon be mandated for critical assets.
- The first step of a migration roadmap is to inventory which assets support PQC and which don’t.
- The Forescout 4D Platform™ helps asset owners:
- Discover and map devices
- Prepare to gain control of the risk they could bring to the network
- Give planning support ahead of upgrades and mitigations
Identifying Network Assets with Quantum-Safe Cryptography
Quantum computing has been advancing rapidly. Governments and organizations are now concerned that a quantum computer could break traditional asymmetric encryption, such as RSA and ECC in the next few years — but it is more likely within the next decade.
Post-quantum cryptography (PQC), which is not susceptible to quantum threats, already exists but organizations need to migrate their assets to use this new technology. That includes IT, OT, IoT, medical devices, and other network-connected assets.
Most often discussed quantum threats relate to “harvest now, decrypt later” for confidential information. Decryption of confidential information is also relevant for network assets, such as IoT and OT equipment, as attackers could gain access to credentials or intellectual property, for instance. However, there are other relevant security risks for these assets, such as:
- Unauthorized remote access by exploiting functionality that relies on public keys for authentication and authorization.
- Tampering with device-to-device communication by decrypting traffic.
- Persistent and stealthy malware that exploits signatures used for secure boot and firmware integrity checks.
Current quantum migration roadmaps throughout the world mandate transitioning to PQC between 2030 and 2035, especially for critical assets. These PQC migration roadmaps are long, but according to CISA, “conducting an inventory of vulnerable critical infrastructure systems […] is the first step of this preparation […].”
Here, we review the status of PQC migration on the internet and discuss how Forescout helps organizations understand their risks and prepare for this transition.
Background: Who Has Adopted Post-Quantum Cryptography?
Network assets use cryptographic algorithms for different types of services. The most popular protocols include Secure Shell (SSH), used for remote access, and Transport Layer Security (TLS), which forms the basis of services, such as HTTPS.
These protocols rely on algorithms that are often developed by academics, standardized by NIST, then later integrated into existing internet services by the IETF and IANA.
In 2022, NIST selected Kyber for Key Encapsulation Mechanism (KEM), as well as Dilithium, SPHINCS+, and Falcon for digital signatures as the first PQC algorithms to be standardized. The first three final standards were published in August 2024 as:
Other PQC algorithms exist, although they have not been standardized by NIST. Most notably, the German BSI additionally recommends the use of FrodoKEM and Classic McEliece for KEM, as well as LMS/HSS and XMSS/XMSS^MT for digital signatures. Similarly, Streamlined NTRU Prime (SNTRUP) has been used by SSH applications since 2022.
After NIST finalized the standards, IANA added the standardized parameters for ML-KEM and hybrid schemes using ML-KEM in TLSv1.3, as well as ML-KEM and SNTRUP in SSH. The last step to enable end users to start the migration was including these new standardized algorithms in applications, which is already happening:
- OpenSSH 8.9, released in February 2022, added support for SNTRUP, which became the default key exchange method in the 9.0 release (April 2022). ML-KEM support was added on OpenSSH 9.9 (September 2024) and made the default KEM in the 10.0 release (April 2025).
- Chrome 115, released in July 2023, added experimental support for hybrid Kyber as a TLSv1.3 client. This was deprecated in Chrome 131 (September 2024) in favor of the standardized ML-KEM.
- Microsoft SymCrypt, the crypto library used in Windows and other Microsoft products, started adding support for PQC in September 2024.
- OpenSSL 3.5, released in April 2025, added full support for the three NIST standards ML-KEM, ML-DSA and SLH-DSA.
Beyond libraries and applications, consumer products, such as PCs and printers, have started adding support for quantum-safe algorithms in the last year, especially in secure boot capabilities.
Status: What Is the Prevalence of PQC on the Internet?
Since quantum migration has already started, we wanted to understand how it is progressing. To understand the current use of PQC, we used two internet scanning tools, Censys and Shodan, to examine two relevant protocols: SSH and TLS.
SSH
Using a Censys query to list the most used SSH key exchange algorithms results in over 186 million hosts on the Internet. These hosts use OpenSSH and other servers, such as Dropbear, which is very common in embedded devices — and also added support for PQC in its latest version 2025.87.
The most popular algorithms currently are curve25519-sha256, diffie-hellman-group-exchange-sha256, and ecdh-sha2-*. These are all quantum-unsafe and run on around 30 million hosts each (16% of the total).
The table below presents the most popular PQC methods currently in use.
| PQC KEM | #Hosts | %Hosts |
|---|---|---|
| [email protected] | 9,815,725 | 5.27% |
| sntrup761x25519-sha512 | 1,460,306 | 0.78% |
| mlkem768x25519-sha256 | 188,157 | 0.10% |
| [email protected] | 27,070 | 0.01% |
| [email protected] | 19,497 | 0.01% |
| [email protected] | 19,497 | 0.01% |
| [email protected] | 19,497 | 0.01% |
| [email protected] | 18,463 | 0.01% |
| mlkem1024nistp384-sha384 | 244 | <0.01% |
| mlkem768nistp256-sha256 | 243 | <0.01% |
| [email protected] | 13 | <0.01% |
| [email protected] | 13 | <0.01% |
The first, second, and fourth entries are the same algorithm (hybrid SNTRUP+x25519). The first and fourth use vendor extension names “@openssh.com” and “@tinyssh.org” that pre-date IANA’s assignment. The second uses the IANA-assigned parameter. Entries with “@openquantumsafe.org” are experimental implementations from the OQS project.
The table shows that more than 11 million hosts – around 6% of the total SSH servers – currently support PQC.
That number is growing fast despite it not being a large percentage. The figures below track the evolution of hosts supporting the two most popular PQC algorithms:
- sntrup761x25519-sha512 grew by 30% in the six months between April and October 2024 — and by a further 21% in the six months between October 2024 and March 2025.
- mlkem768x25519-sha256 grew by 554% in the six months between October 2024 and March 2025. It is expected to continue growing, but at a lower pace.
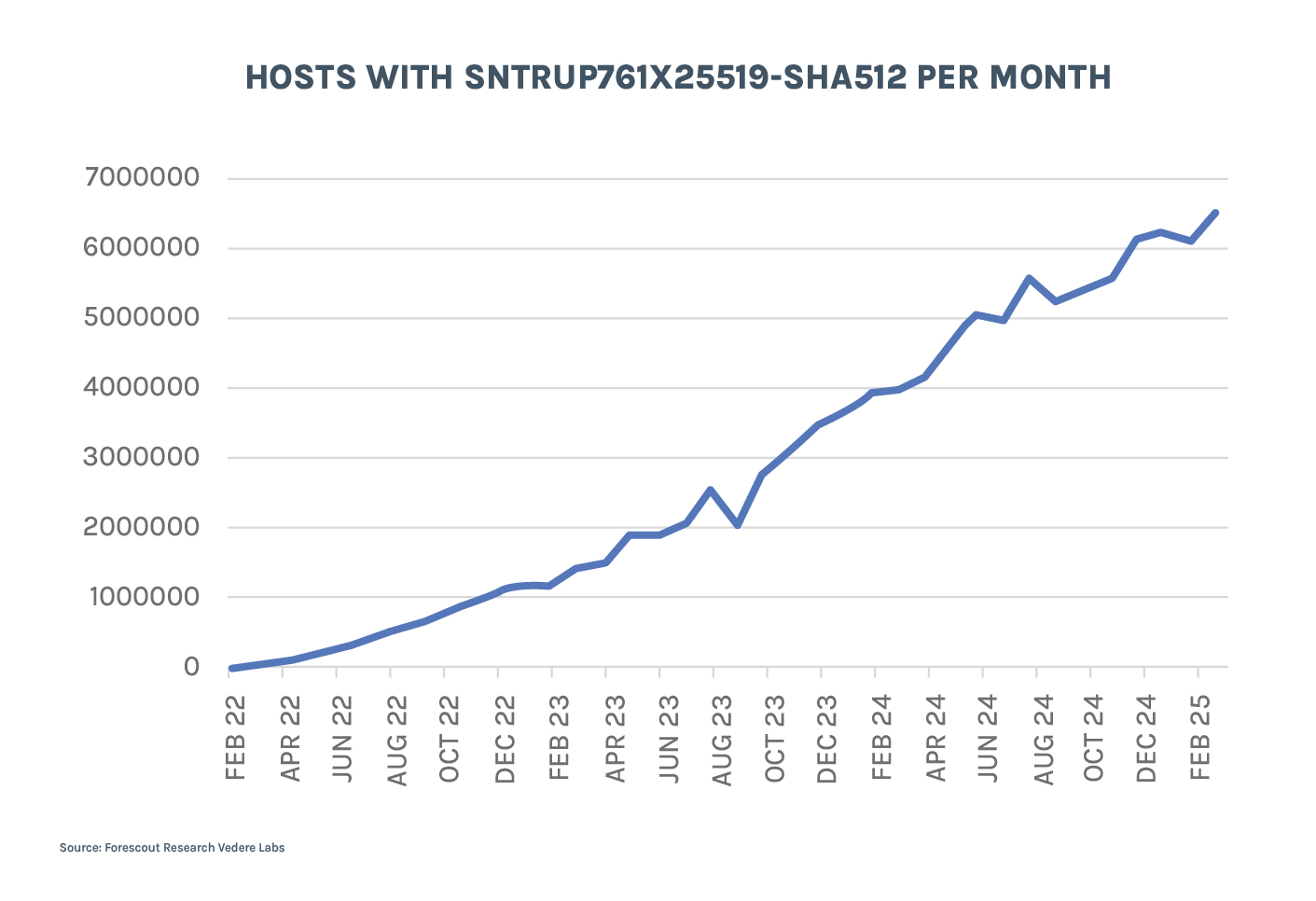
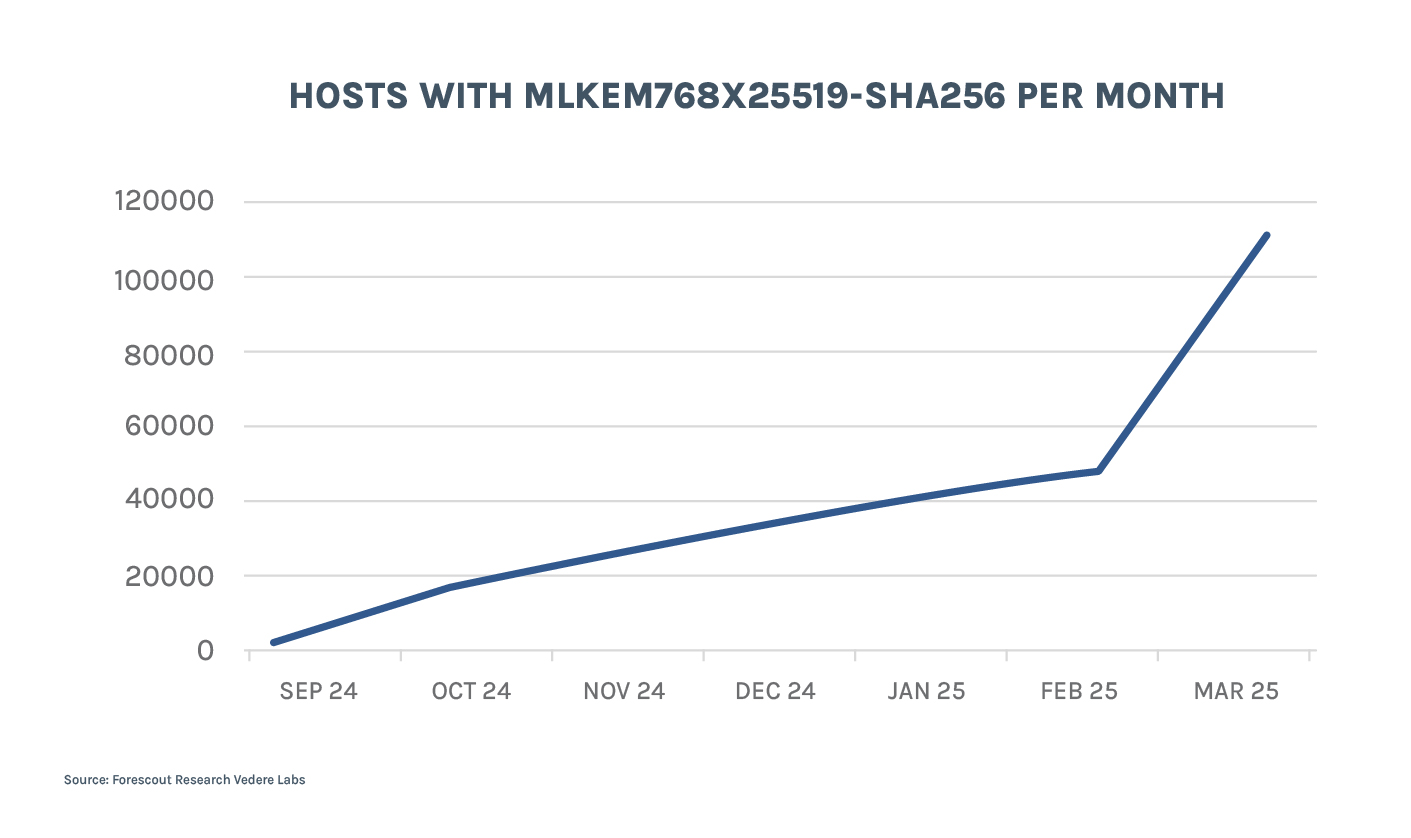
Note that the figures start at different points in time because that is when each algorithm was added to OpenSSH. They also end with different numbers than what was shown in the table above because this data comes from Shodan, while that came from Censys.
The decreasing rate of growth as time passes by is normal, since the “early adopters” will update as soon as possible and then the number of people who can easily update servers/devices decreases. It’s the usual problem of legacy devices we so often face in both IT and OT security.
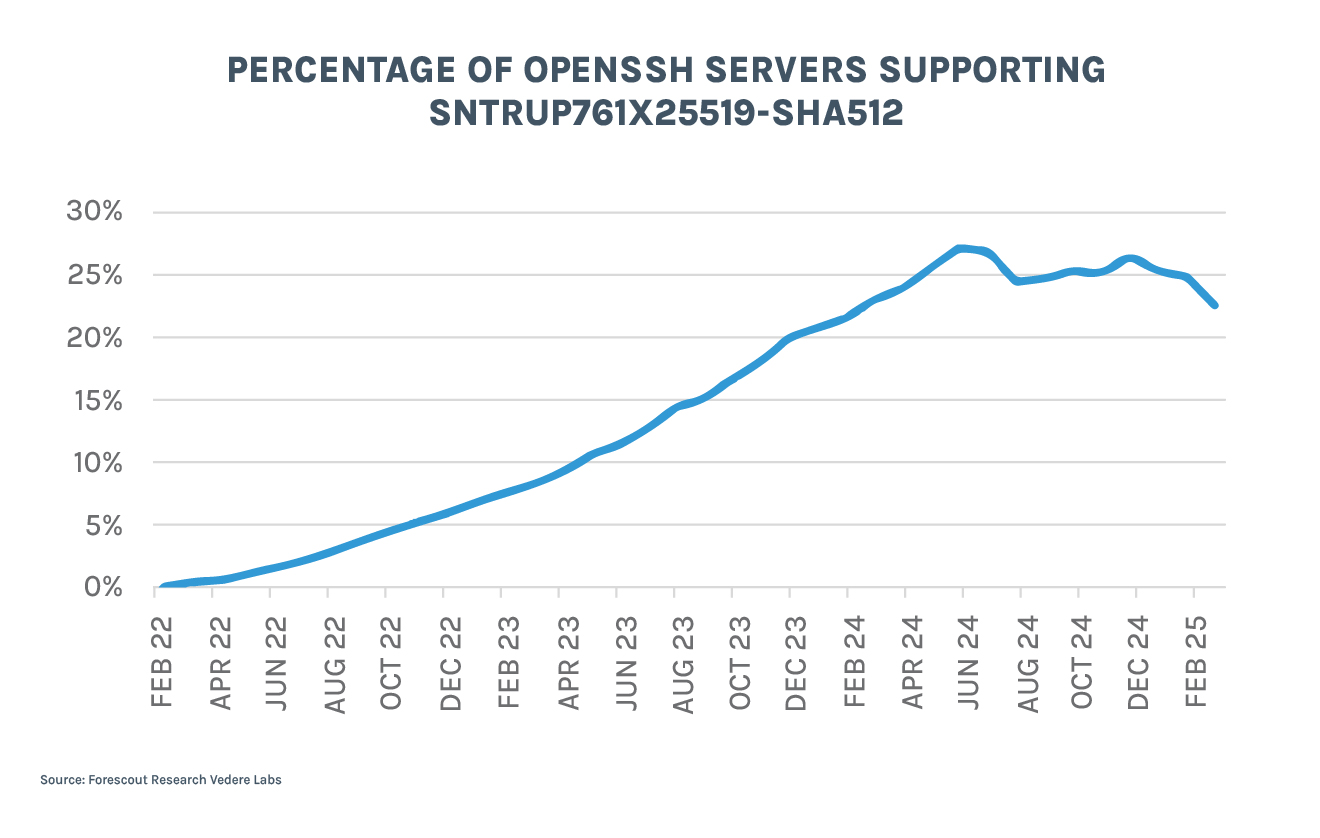
This is evidenced in the chart below – again using Censys data. Almost three quarters of OpenSSH servers on the Internet nowadays run versions between 7.0 and 8.9, which were released between 2015 and 2022, just before OpenSSH added support for PQC by default. Even older versions are still common. Versions 9.0 until 10, which have SNTRUP and then ML-KEM as default key exchange mechanisms are around 21% of OpenSSH servers.
That same 21% is seen in the next chart, which now uses Shodan data. The percentage of OpenSSH servers supporting sntrup761x25519-sha512 grew quickly until it reached the 20-25% range last year. Now it has been oscillating in that range since most servers that could be easily updated – or that had a strong reason to be update quickly – already did.
TLS
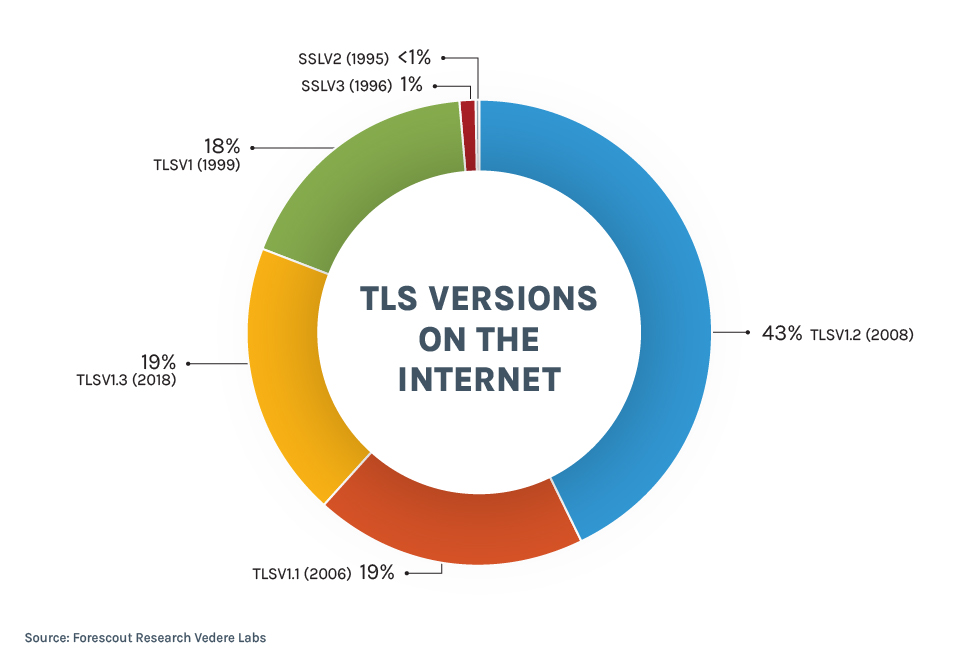
For TLS, we could not directly measure the new algorithms being supported by servers and clients, but we used TLS version as a proxy for that information.
The IETF is only adding PQC support for TLSv1.3. However, the figure below – using data from Shodan – shows how TLSv1.3 (released in 2018) is still only the third most popular version of the protocol supported by servers nowadays.
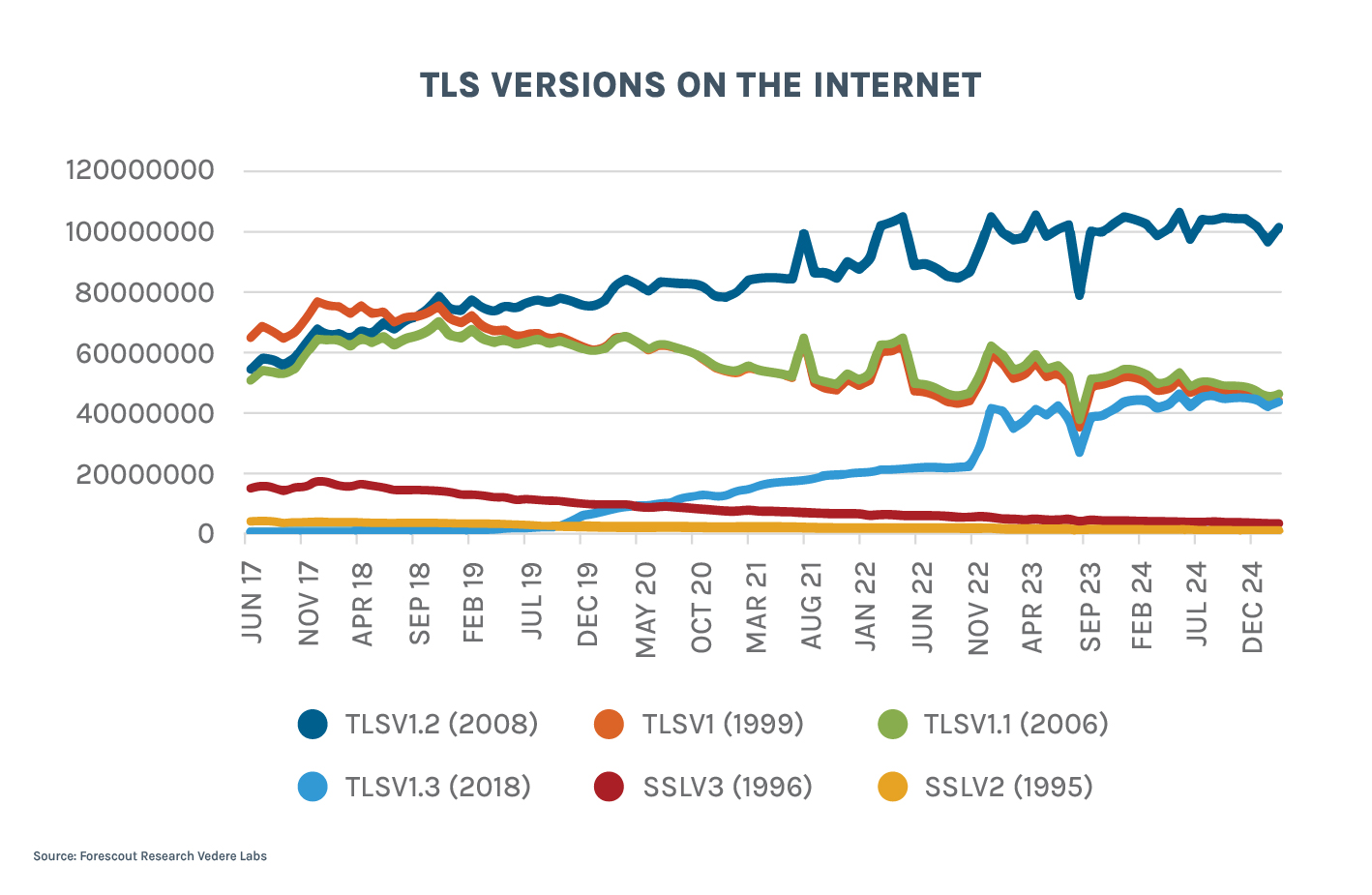
The figure below shows a phenomenon similar to what we saw for OpenSSH deployments: adoption of TLSv1.3 was very fast until early 2023, but growth has slowed considerably since then.
Looking Ahead: How Forescout Can Help
The data above shows two things:
- The PQC migration has already started since all the basic pieces are in place for organizations to adopt quantum-safe technologies.
- Those who can easily upgrade servers and devices will likely do so fast, but we will see decreasing rates of growth of these technologies as the easy deployments are done first.
The main difference of the PQC migration – compared to TLSv1.3 and other previously slow adoption of encryption technology – is that this migration will soon be mandated for critical assets and organizations.
Therefore, organizations will need to understand what assets already support PQC, what needs to be migrated or replaced, and what risk those devices bring to the network.
Enter the Forescout 4D Platform™.
The Forescout 4D Platform™ continuously identifies, protects and ensures the compliance of all managed and unmanaged cyber assets – IT, IoT, IoMT and OT – without business disruption. It delivers comprehensive capabilities for network security, risk and exposure management, and extended detection and response.
Forescout has already delivered extensive coverage for insecure cryptography and broader security posture issues, enabling organizations to monitor and manage a wide range of encryption-related risks across their environments.
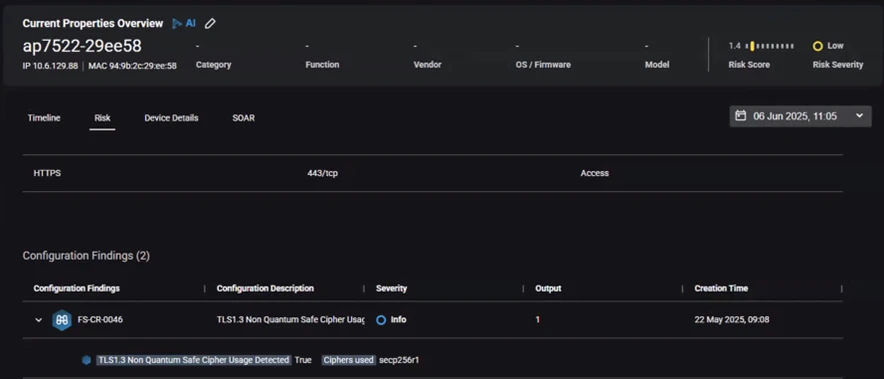
After a period of testing and patent acceptance in 2024, can detect TLS 1.3 connections that use quantum-safe, PQC, algorithms standardized by NIST and IANA/IETF.
This information is sent to Forescout eyeFocus, the risk exposure management component of the platform, for matching and tracking.
While Forescout rules enable asset filtering and executive reporting to monitor PQC adoption, they do not yet impact individual asset risk scores.
Since quantum-safe profiles are still rare, we will progressively adjust the risk scoring over time as regulatory frameworks and technology adoption evolve, ensuring alignment with emerging requirements.