As Field CTO at Forescout, I spend much of my time working with customers across critical infrastructure, manufacturing, and energy sectors who face an increasingly complex challenge: securing operational technology environments.
And calling it a challenge is an understatement. Between 2022 and 2024, there was a 668% increase in attacks on critical infrastructure, according to data from Forescout’s research team, Vedere Labs. This isn’t hyperbole. These are the facts from the 19 billion+ devices in our customer data lake.
OT systems power our water treatment plants, energy grids, transportation networks, and so much more. When these systems go down or get compromised, it’s more than an inconvenience. It’s a national emergency.
Recently, CISA and its international partners released the guidance “Foundations for OT Cybersecurity: Asset Inventory Guidance for Owners and Operators.” This document reinforces what I see every day in the field: you can’t protect what you don’t know you have in your environment.
A reliable asset inventory is not just a checkbox exercise. It’s the foundation of an effective operational technology (OT) security strategy. The CISA guidance works across industries but also had input from “working sessions with organizations in the Energy Sector and Water and Wastewater Sector.”
We’ve designed the Forescout 4D Platform™ to give organizations continuous visibility and control across their OT, IT, and IoT environments. Our products, including eyeInspect, directly address many of the challenges highlighted in CISA’s recommendations. Below are five key recommendations that show how the platform helps organizations achieve them.
The Big Why: Visibility Doesn’t Equal Security, But You Can’t Have Security Without Visibility
Here’s the cold hard truth: you can’t defend what you can’t see. That’s why this guidance is so critical. It’s not just about ticking a box, it’s about building a foundation for modern, defensible architecture that keeps OT safe in an evolving threat landscape.
Step-by-Step: How to Build Your OT Asset Inventory (And Why Each Step Matters)
CISA’s guidance lays out a clear five-step roadmap. Here’s what you need to know:
1. Define Scope & Objectives
The first step in building an asset inventory is defining scope and governance. Organizations need to agree on which environments, facilities, and systems are in play, and assign clear roles for ownership. Without this structure, inventories quickly become outdated or incomplete. With Forescout, discovery is automated and continuous, ensuring that defined scope is consistently monitored.
Governance is supported through out of the box integrations with Service Management tools and CMDBs, such as ServiceNow, providing a clear system of record. Solutions like Forescout’s eyeInspect create a continuous blanket of visibility, which enables asset owners to identify the specific assets that need to be incorporated in the scope.
2. Identify Assets & Collect Attributes
Visibility gaps are one of the biggest risks in OT. Hidden assets – legacy controllers, unpatched devices, or shadow systems – can become backdoors for attackers. CISA recommends documenting every asset with attributes such as vendor, firmware, communications, and location.
Forescout eyeInspect excels here by continuously identifying assets across OT environments without disrupting operations. It captures rich context about each device and communicates that data into the broader 4D Platform for enterprise-wide visibility.
3. Create a Taxonomy
Structure matters. Group assets by criticality, function, zones, conduits, etc.-think ISA/IEC 62443 standards. Visualize, validate, review. The Forescout 4D Platform™ provides a robust policy-based classification engine, allowing customers to organize assets into groups based on role, process, or operational function. This taxonomy is the backbone of effective segmentation and policy enforcement and is shared throughout the platform.
Here’s an example taxonomy:
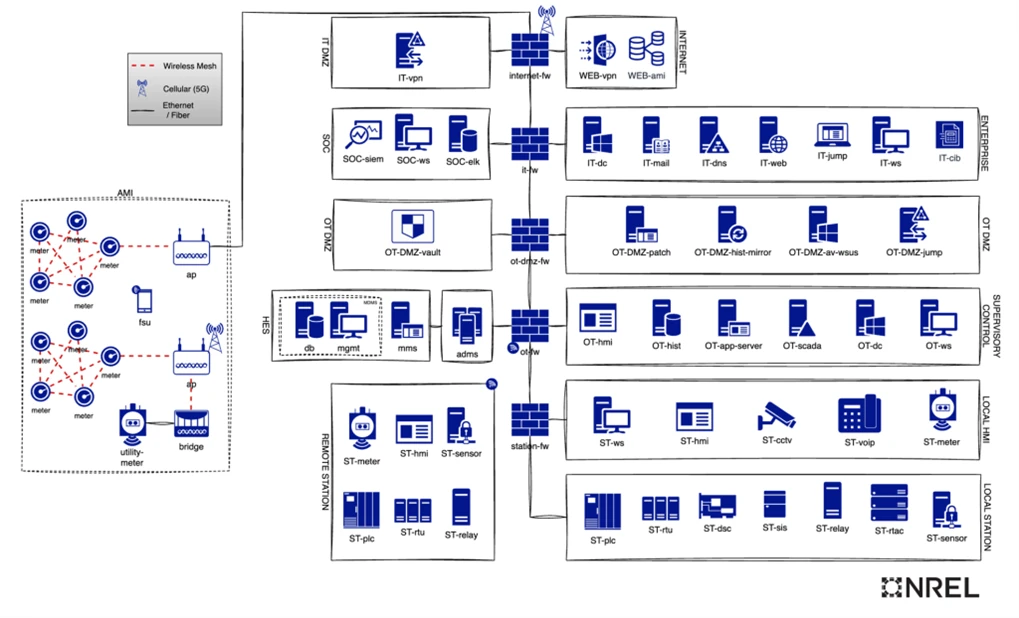
Source: National Renewable Energy Laboratory (NREL)
4. Manage & Centralize Data
CISA emphasizes the importance of managing data quality and lifecycle changes. Pull in vendor manuals, configuration specs, maintenance records-keep everything in a secure, centralized repository. This isn’t just inventory-it’s intelligence. Without ongoing updates, inventories lose value.
The Forescout 4D Platform™ integrates with CMDBs to ensure deduplicated, normalized data is available across the enterprise. As assets are added, updated, or retired, Forescout ensures the inventory remains accurate, enabling better planning and fewer surprises during audits or incident response.
5. Implement Life-Cycle Management
Assets don’t live forever. Define stages-from acquisition to decommissioning. Plan for maintenance, backups, replacements, retirements. That’s how you keep the inventory alive and useful. An inventory isn’t an end state – it’s a foundation for stronger defenses. CISA highlights using the inventory to prioritize risk management, vulnerability patching, maintenance, and supply chain planning.
With our platform, organizations can move beyond visibility to action. For example, eyeInspect-detected vulnerabilities and threats can automatically drive response actions, either within the Forescout suite or via integrations with 3rd party solutions. This closes the loop, enabling organizations not only to identify risks but also to defend against them effectively. The inventory can also be utilized to make determinations around device accesses and traffic segmentations.
See exactly how our technology works — on your own time and on your own terms in this self-guided demo.
What Comes Next: Turning Inventory into Impact
CISA doesn’t stop at asset discovery. Their guidance pushes you further into five essential post-inventory actions:
- OT Cybersecurity & Risk Management
Cross-check your inventory with CISA’s KEV Catalog, prioritize security fixes by criticality, and build layers like segmentation, access controls, and monitoring. - Maintenance & Reliability
Integrate asset data with your maintenance plans-spare parts, patch workflows, secure procurement (“secure by design”). - Performance Monitoring & Reporting
Track process health (temperature, pressure, flow) and network diagnostics. Report proactively, and make sure someone owns that inventory. - Training & Awareness
This is a shared responsibility. Make sure everyone understands why asset visibility matters and how to use the tools. - Continuous Improvement
Build feedback loops, track changes, audit regularly. Your inventory should evolve-not age.
Bottom Line
This isn’t just bureaucratic fluff. It’s a survival strategy. CISA’s OT asset inventory guidance arms you with visibility, context, and control. From defining your scope to establishing continuous feedback, each step builds toward a resilient OT environment where security and reliability go hand in hand.
Let’s get started, because if you don’t know what’s on the network, you’re not managing risk, you’re inviting it.