In today’s interconnected world, the proliferation of Internet of Things (IoT) devices presents opportunities and challenges. One significant challenge is the secure onboarding and management of devices that lack traditional interfaces or robust security features, often referred to as “unmanageable devices”. The National Institute of Standards and Technology (NIST) address this issue in its Special Publication (SP) 1800-36 series, “Trusted Internet of Things (IoT) Device Network-Layer Onboarding and Lifecycle Management“. The Forescout 4D Platform™ aligns with NIST’s guidelines, offering comprehensive solutions to effectively onboard and take control of unmanageable devices.
Understanding the Challenge of Unmanageable Devices
Unmanageable devices are typically IoT devices that lack user interfaces, making manual configuration challenging. They often come with minimal security features, increasing the risk of unauthorized access and network vulnerabilities.
In the official paper on the topic, NIST and the National Cybersecurity Center of Excellence authors sum up the security issues in the following way:
“Once a device is connected to the network, if it becomes compromised, it can pose a security risk to both the network and other connected devices. Not keeping such a device current with the most recent software and firmware updates may make it more susceptible to compromise. The device could also be attacked through receipt of malicious payloads. Once compromised, it may be used to attack other devices on the network.”
NIST SP 1800-36 highlights the necessity for scalable, automated mechanisms to securely manage these devices throughout their lifecycles, emphasizing trusted network-layer onboarding and continuous posture assessment. The following is a graphic from the “NIST Cybersecurity for IoT Program”
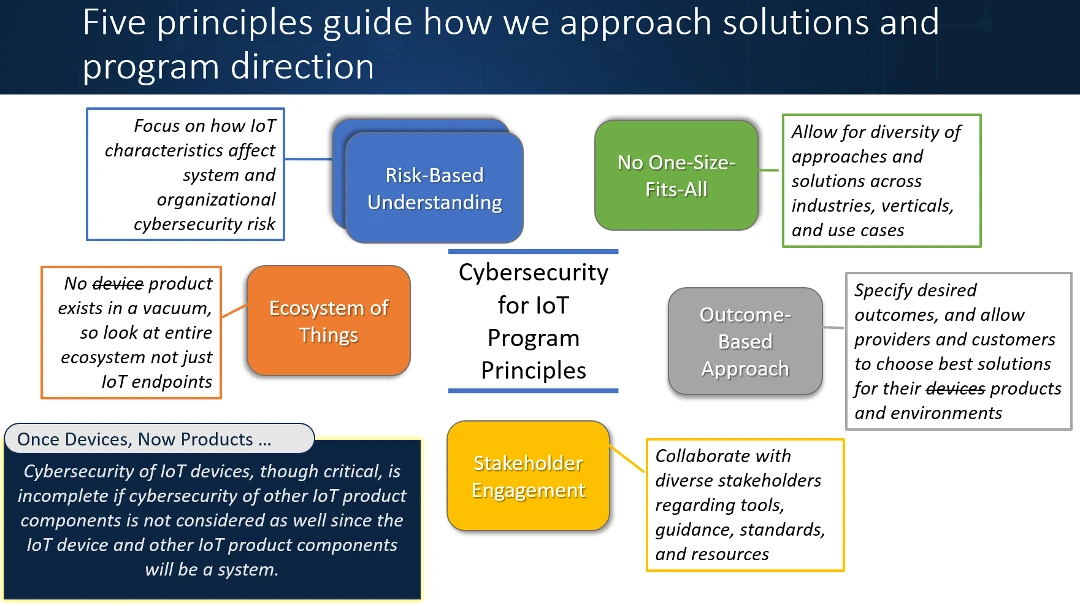
Source: NIST
What are the riskiest devices across IoT and IoMT in 2025? Go deeper in this on-demand webinar with Dr. Daniel dos Santos, Sr. Director and Head of Security Research, at Forescout’s Vedere Labs.
Forescout’s Approach to Secure Onboarding
Forescout’s platform offers a robust framework to address the challenges associated with unmanageable devices across four interconnected principles: Discover, Assess, Control, and Govern:
Leverage Third Party System of Record
Organizations often utilize asset management systems or configuration management databases to store and maintain up to date records of owned devices. Asset owners are responsible for maintaining the accuracy of the data contained therein. Forescout integrates with these systems, such as the ServiceNow CMDB, to obtain visibility into the devices, properties, and status —and prepares for them to enter the network. When devices are deployed, the 4D Platform ensures they properly and securely gain network access.
Automated Device Discovery and Classification
Once on the network, Forescout provides real-time visibility into all devices, including those newly deployed and unmanageable, connected to the network. By continuously monitoring network traffic, Forescout identifies and classifies devices based on their behavior and characteristics, ensuring a comprehensive repository of connected devices which can then be synchronized back into the CMDB. This ensures the CMDB is continuously updated with the current state of the network.
Policy-Based Network Access Control
Leveraging its detailed device inventory, Forescout enforces granular network access policies. For unmanageable devices, this means assigning appropriate network segments and permissions based on their function and security posture, aligning with NIST’s principle of least privilege.
Continuous Monitoring and Compliance Enforcement
Forescout continuously assesses the behavior and compliance status of the connected devices. If an unmanageable device exhibits anomalous behavior or deviates from established policies, Forescout can automatically trigger predefined responses, such as alerting administrators or isolating the device, thereby mitigating potential threats.
Alignment with NIST SP 1800-36 Guidelines
Forescout’s capabilities closely align with the recommendations outlined in NIST SP 1800-36:
Trusted Network-Layer Onboarding
NIST emphasizes the importance of establishing trust between IoT devices and networks during the onboarding process. Forescout facilitates this by verifying device identities and ensuring they meet security requirements before granting network access, thereby preventing unauthorized devices from infiltrating the network.
Lifecycle Management
Beyond onboarding, NIST highlights the need for ongoing management of IoT devices to maintain security throughout their operational life. Forescout addresses this by continuously monitoring device behavior, enforcing compliance with security policies, and providing automated responses to detected threats, ensuring that devices remain secure from deployment to decommissioning.
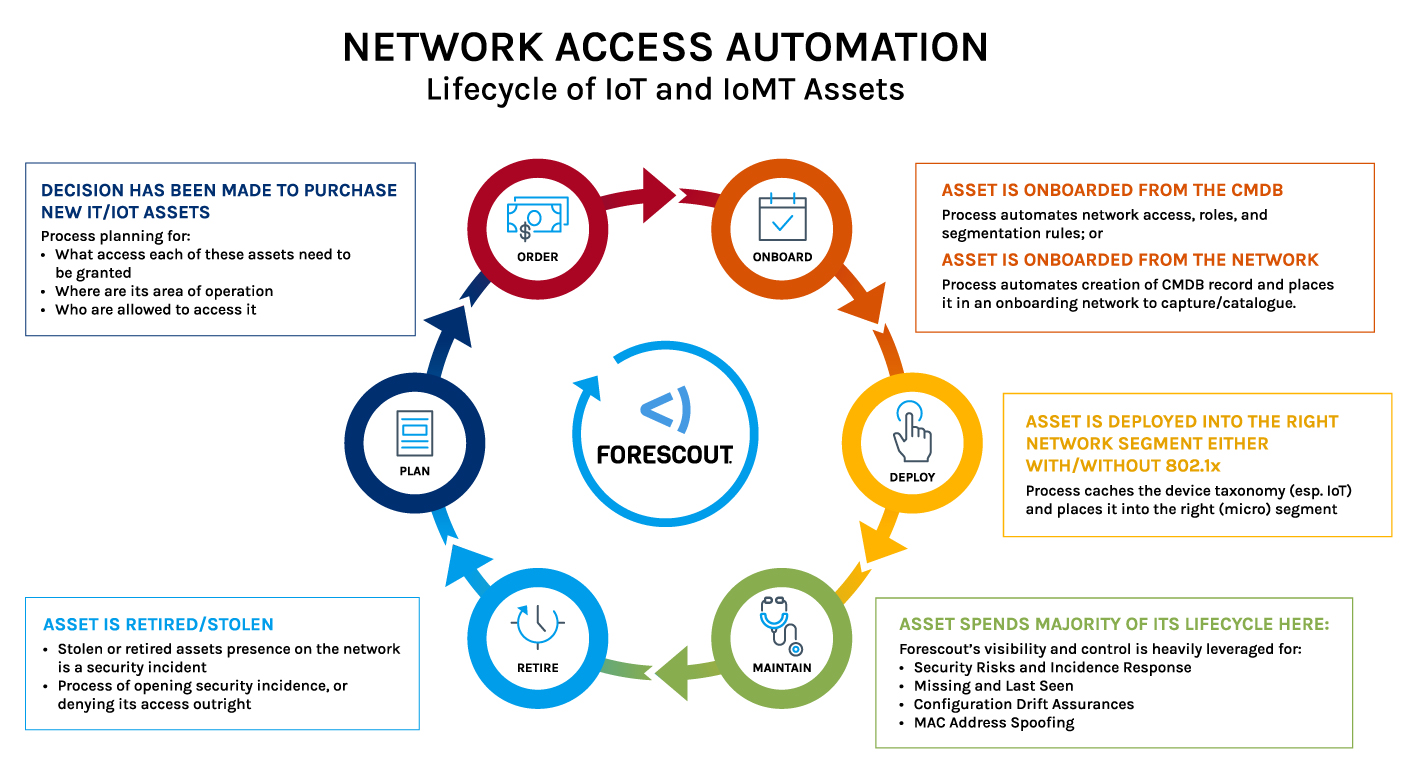
Case Study: Enhancing IoT Security with Forescout
Consider a healthcare organization deploying numerous medical IoT devices that lack traditional management interfaces. Using Forescout, the organization can either:
- Automatically discover these devices as they connect to the network, classify them based on predefined policies, and assign appropriate network access controls, or
- Query third party systems to obtain devices that are not currently deployed and can ensure they’re accurately and securely placed into the proper network location.
Continuous monitoring ensures that any deviation from expected behavior triggers immediate alerts and remediation actions, thereby safeguarding patient data and maintaining compliance with healthcare regulations.
The secure onboarding and management of unmanageable IoT devices are critical components of a robust cybersecurity strategy. Forescout’s platform offers comprehensive solutions that align with NIST’s guidelines, enabling organizations to confidently integrate these devices into their networks without compromising security.