Threat Detection & Response
Cut through the noise with better detection and response to true threats
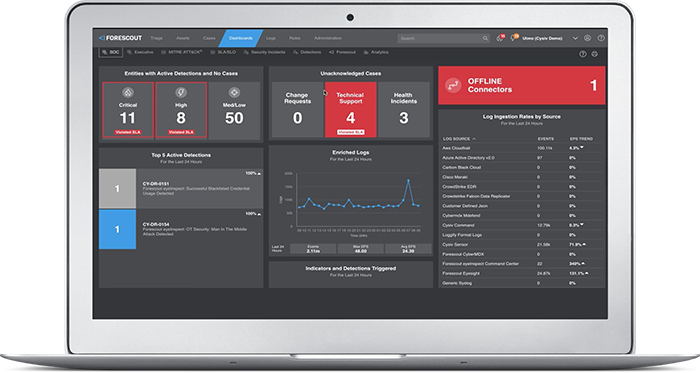
Thwarting sophisticated cyberattacks requires equally sophisticated threat detection, investigation and response capabilities. Your best defense? A Threat Detection & Response solution that enriches and analyzes IT, IoT and OT telemetry from across your entire enterprise, leverages artificial intelligence and other data science techniques to correlate signals and more accurately reveal true threats, and empowers you to respond quickly and appropriately.
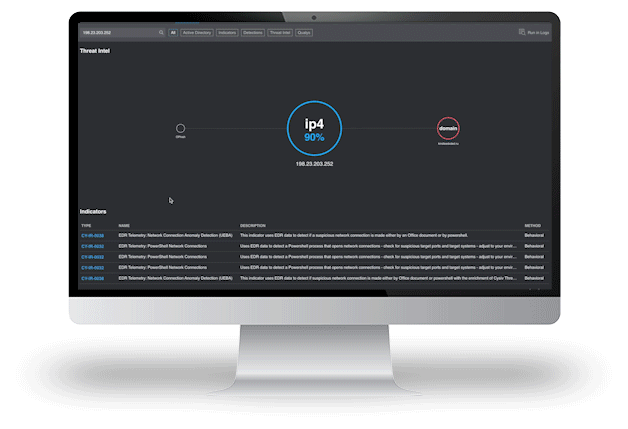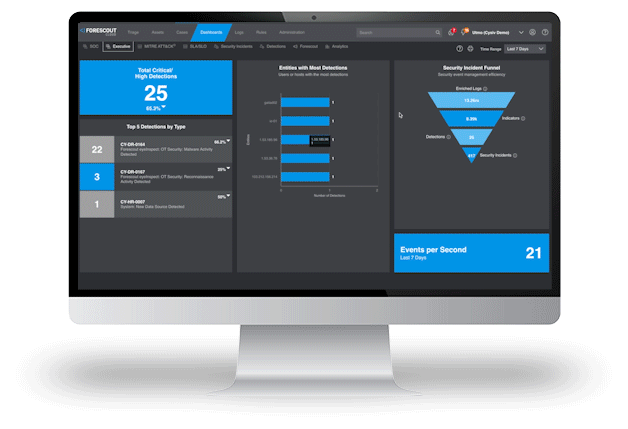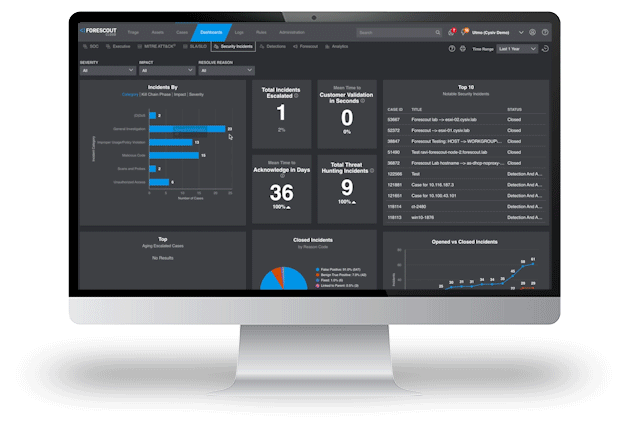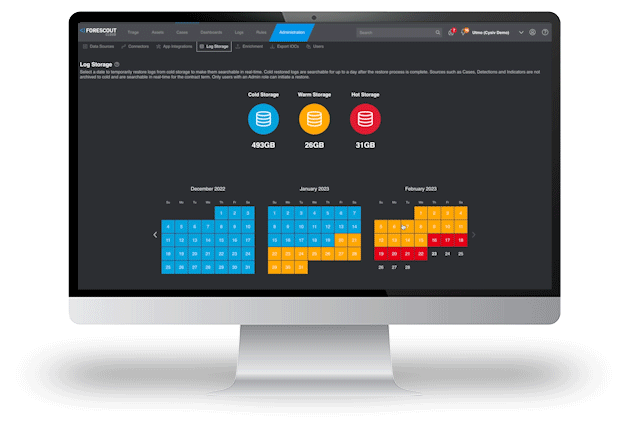
 Vendor and EDR Agnostic Data Ingestion
Vendor and EDR Agnostic Data Ingestion 450x Better Detections
450x Better Detections Full Spectrum Response
Full Spectrum Response Up Front Risk Reduction
Up Front Risk Reduction Simple, Predictable, and Accessible Pricing
Simple, Predictable, and Accessible Pricing