CYBERSECURITY A-Z
What Is Hybrid Cloud Security?
Hybrid cloud security refers to the strategies, technologies, policies, and processes used to protect data, applications, and infrastructure operating across hybrid cloud environments. It combines public cloud services (for example, AWS, Microsoft Azure, or Google Cloud) with private cloud infrastructure or on-premises systems, creating a more flexible and distributed IT environment.
Adoption is surging as organizations seek to combine the scalability of public cloud with the control and customization of private environments. Gartner predicts that 90% of organizations will adopt this approach through 2027.i According to the 2025 State of Cloud Security Reportii:
- 54% of organizations have adopted hybrid cloud models
- Over 78% of respondents use two or more cloud providers
- Single cloud adoption is becoming less common, with just 18% relying on a single provider (down from 22% in 2024)
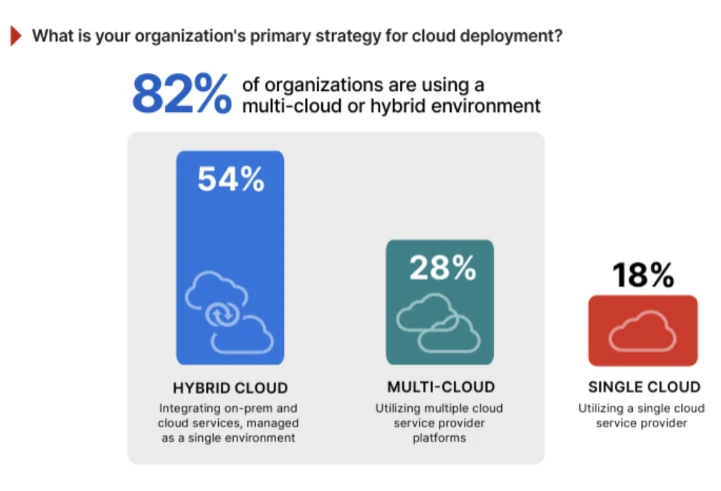
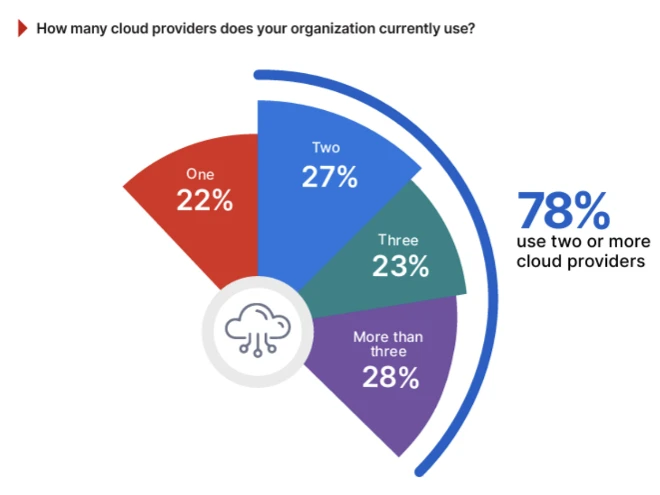
Source: https://www.cybersecurity-insiders.com/state-of-cloud-security-report-2025/
Security is essential for organizations that need to maintain agility and scalability while preserving data sovereignty, meeting regulatory requirements, and securing legacy systems.
Why Hybrid Cloud Security Matters
Organizations are increasingly turning to these strategies to balance flexibility, performance, and control. By blending on-premises or private cloud infrastructure with public services, it enables businesses to scale rapidly while meeting regulatory and operational requirements.
However, it also introduces security challenges. Because it spans multiple platforms with differing ownership and control models, hybrid cloud security must address a unique mix of risks and threats. In this environment, security professionals must manage multiple security architectures, maintain visibility across cloud boundaries, and protect data as it moves between systems. This requirement is complicated by the shared responsibility between cloud service providers (CSPs) and cloud service customers (CSCs).
Common security challenges in these environments include:
- Expanded attack surface: More environments mean more endpoints, more users, and more complexity.
- Visibility gaps: Using different tools and consoles to monitor assets across multiple cloud providers and on-prem environments can be disjointed and inconsistent: 55% of organizations cite loss of clear discernability and control as a key challenge in multi-cloud environments.iii
- Misconfigurations: Inconsistent or insecure configurations across clouds lead to gaps in protection.
- Inconsistent access controls: Consistently enforcing least-privilege access and protecting against unauthorized access is difficult without centralized identity management.
- Data movement and privacy: Ensuring compliance with data residency and privacy laws becomes harder as data moves between clouds. 58% of organizations say ensuring data protection and privacy for each cloud environment is a major challenge.iv
- Slow threat response: Siloed systems make it hard to detect, analyze, and respond to threats in real time. In fact, 64% of organizations report having little to no confidence in their ability to detect and respond to threats in real time.
- Cybersecurity skills gap: Many organizations struggle to hire or train staff who can manage hybrid cloud security effectively. Fifty-three percent of organizations cite ‘lack of the right skills’ as a top challenge in securing multi-cloud environments.v
Consider how the complexity and the integration of on-premises and cloud resources makes hybrid cloud environments more vulnerable. Whether through a misconfigured API, weak credentials, or brute force, attackers can gain access and move swiftly and undetected across cloud and on-premises systems.
One increasingly common tactic is Pass-the-PRT (Primary Refresh Token), where attackers use a stolen authentication token from an endpoint to impersonate a user and gain access across environments. This type of North-South lateral movement enables threat actors to escalate privileges and target high-value assets across the entire hybrid infrastructure. Traditional firewalls and legacy security controls aren’t built to contain this kind of movement. And the cybersecurity skills gap and lack of visibility across this expanded attack surface make it difficult to protect data and other valuable assets.
Together, these challenges make it an urgent priority for any organization that need to ensure that assets are protected as they move between environments and that policies are consistently enforced regardless of where workloads run.
Relationship Between Hybrid Cloud Security, Cloud Network Security, and Cloud Security
A robust hybrid cloud security strategy combines principles from both cloud security and network security, while addressing the unique connectivity and visibility challenges introduced by hybrid architectures. Here’s how hybrid cloud security relates to cloud security and cloud network security:
- Cloud Security is the broad discipline of protecting cloud-based assets, applications, and infrastructure across public, private, and hybrid environments.
- Cloud Network Security focuses on securing network traffic, endpoints, virtual private clouds (VPCs), and connections between clouds and on-premises systems.
- Hybrid Cloud Security extends cloud security to environments that span both public cloud and on-premises infrastructure, requiring coordinated policies and technologies across both.
In hybrid deployments, security solutions must work cohesively across public cloud, private cloud, and on-premises without creating operational silos. The challenge lies in integrating security frameworks and tools across multiple clouds and on-prem networks, each with different configurations, controls, and risk profiles.
How Does Hybrid Cloud Security Work?
It works through a mix of tools, policies, and architectural strategies, many of which align with the shared responsibility model promoted by the Cloud Security Alliance (CSA)vi, National Institute of Standards and Technology (NIST)vii, and major CSPs:
- Cloud Service Providers (CSPs) secure the infrastructure (data centers, storage, networking, virtualization).
- Cloud Service Customers (CSCs) secure everything they build or configure on top of it, including applications, data, identities, and endpoints.
The level of responsibility varies depending on the model:
- SaaS: The provider manages most security layers. The customer focuses on access controls and configuration.
- PaaS: The provider secures the platform. The customer secures code and data.
- IaaS: The customer handles nearly all layers, from OS to runtime and networking.
Hybrid cloud security tools integrate across these models, providing knowledge and control through:
- Identity and access management
- Encryption and key management
- Real-time traffic monitoring
- Network segmentation and micro-segmentation
- Automated misconfiguration detection
- Policy enforcement across environments
Best Practices
To ensure a secure architecture, organizations should adopt the following best practices:
- Automate detection and remediation: Use Cloud Security Posture Management (CSPM) tools to identify and fix misconfigurations in real time.
- Implement Zero Trust principles: Use micro-segmentation and adaptive access policies to reduce attack surface and enforce least privilege.
- Leverage AI and ML: Employ machine learning for anomaly detection, threat intelligence, and automated incident response. Forescout AI, for example, synthesizes connected device threats to enhance decision-making and operational efficiency across cloud environments.
- Ensure robust encryption: Encrypt data during transit, at rest, and in use to meet compliance requirements and mitigate exposure.
- Invest in cybersecurity training: Address the cybersecurity skills gap by upskilling existing teams and providing education on managing multi-cloud and hybrid environments.
- Unify visibility and controls: Centralize security monitoring and policy enforcement across all cloud environments and on-premise systems.
- Adopt shared responsibility practices: Understand and implement the security controls appropriate to each cloud service model (SaaS, PaaS, IaaS).
- Conduct regular audits to test incident response plans: Continuously monitor, test, and improve cloud security posture through auditing, red teaming, and simulation.
These practices align with NIST’s Cybersecurity Framework (CSF)viii and special publications like NIST SP 800-210ix that focus on access control and governance in cloud systems.
What Types of Hybrid Cloud Security Solutions Are Available?
Securing these environments requires a holistic approach that includes real-time visibility, identity and access management, data protection, compliance enforcement, and network segmentation across all connected systems. Organizations can choose from a variety of solutions that enable detection, prevention, and response:
- Cloud Security Posture Management (CSPM): Detects and remediates cloud misconfigurations and compliance risks.
- Cloud Workload Protection Platforms (CWPP): Protect workloads across hybrid infrastructure with runtime protection.
- Cloud Infrastructure Entitlement Management (CIEM): Manages identities and entitlements across multiple cloud platforms.
- Identity and Access Management (IAM): Controls user access across cloud and on-prem systems, often with MFA and RBAC.
- Zero Trust Network Access (ZTNA): Enforces identity-based access controls and assumes no implicit trust.
- Network Segmentation and Micro-segmentation: Restricts lateral movement in hybrid networks and isolates sensitive systems.
- Secure Access Service Edge (SASE): Combines networking and security for secure cloud access across distributed users.
- AI/ML-driven threat detection: Uses artificial intelligence to analyze traffic, detect anomalies, and respond in real time.
How Forescout Helps
We offer the comprehensive Forescout 4D Platform™ to strengthen hybrid cloud security across all domains:
- Threat Detection & Response: Forescout delivers AI-powered, real-time insights about connected devices and potential causes of incidents, along with recommended remediation steps.
- Cyber Asset Inventory: Provides a unified view of all assets – including cloud workloads, virtual machines, and IoT devices – with contextual data like location, OS, vulnerabilities, and communication patterns.
- Continuous Monitoring and Risk Management: Identifies vulnerabilities across hybrid environments and prioritizes remediation efforts to reduce the attack surface.
- Automated Remediation: Automates enforcement actions such as quarantine, segmentation, or blocking based on policy violations or threat detection.
- Network Access Control (NAC): Enforces access policies across hybrid environments by detecting and controlling who connects to a network.
- Segmentation Management: Accelerates the design and rollout of segmentation policies, simulates outcomes before implementation, and reduces misconfiguration risks.
- Zero Trust Assurance: Applies continuous verification and adaptive access controls, limiting exposure and preventing lateral movement.
To learn more, visit the Forescout 4D Platform.
[i] Gartner (2024). Gartner Forecasts Worldwide Public Cloud End-User Spending to Total $723 Billion in 2025, November 19, 2024. Accessed April 4, 2025 from the following source: https://www.gartner.com/en/newsroom/press-releases/2024-11-19-gartner-forecasts-worldwide-public-cloud-end-user-spending-to-total-723-billion-dollars-in-2025
[ii] Cybersecurity Insiders (2025). 2025 State of Cloud Security Report, n.d. Accessed April 3, 2025 from the following source: https://www.cybersecurity-insiders.com/state-of-cloud-security-report-2025/
[iii] Ibid.
[iv] Ibid.
[v] Ibid.
[vi] Cloud Security Alliance, Search Results for “shared responsibility.” Accessed April 3, 2025 from the following source: https://cloudsecurityalliance.org/search?s=shared+responsibility
[vii] NIST. Shared Responsibility Model prototype-shared-responsibility-model Reference, n.d. Accessed April 3, 2025 from the following source: https://pages.nist.gov/OSCAL-Reference/models/prototype-shared-responsibility-model/shared-responsibility/
[viii] NIST (2024). The NIST Cybersecurity Framework (CSF) 2.0, February 26, 2024. Accessed April 3, 2025 from the following source: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf
[ix] NIST (2020). NIST SP 800-210, General Access Control Guidance for Cloud Systems, May 15, 2020. Accessed April 3, 2025 from the following source: SP 800-210, General Access Control Guidance for Cloud Systems | CSRC