Continuous Threat Exposure Management (CTEM)
Proactively Reduce Cyber Risk Across Your Entire Attack Surface
Your security team is drowning in alerts from siloed tools while your attack surface grows daily. Cloud migrations, remote work, IoT deployments, and shadow IT create blind spots faster than traditional security assessments can find them.
Forescout shifts you from reactive firefighting to proactive risk management. Get continuous visibility into what’s actually exposed across every connected asset—managed or not, physical or virtual.
Why CTEM Beats Traditional Approaches
Annual pen tests and quarterly vulnerability scans? They’re already outdated before the ink dries. Your attack surface changes hourly, not quarterly.
CTEM gives you a continuous, risk-based approach that actually keeps up:
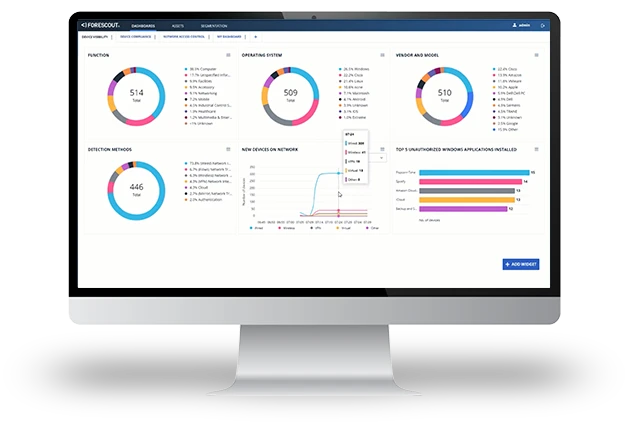
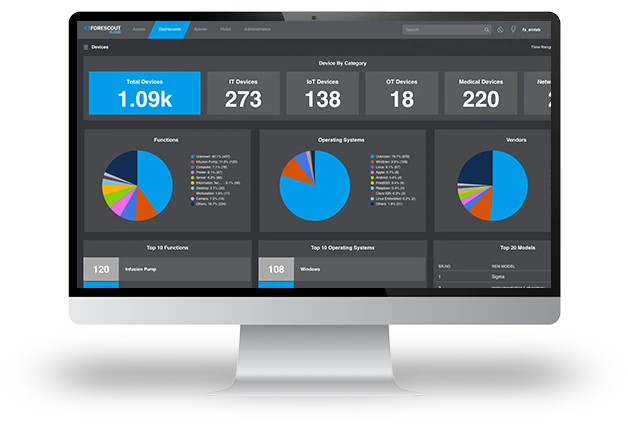
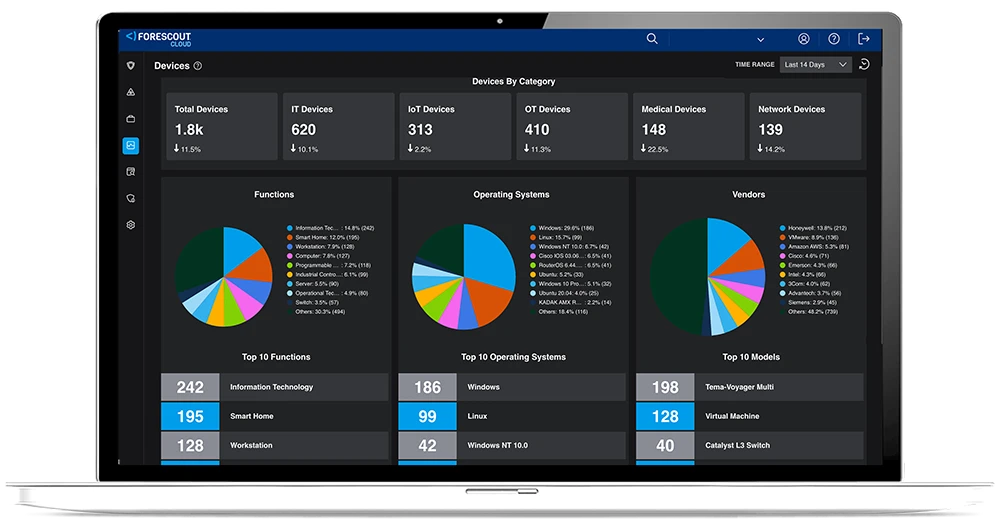
The Forescout 4D Platform™ delivers real-time visibility into your complete attack surface, factoring in asset criticality, active exploits, misconfigurations, and business impact to prioritize what needs fixing first. These insights can also inform downstream enforcement strategies, including Universal Zero Trust Network Access (UZTNA), to reduce exposure and blast radius.
What You Get
Complete Asset Discovery
Persistent inventory with cloud-powered classification for IT, IoT, medical devices, and OT/ICS the instant they connect.
Real-Time Monitoring
Continuous insight into device communications and risky behaviors as they happen.
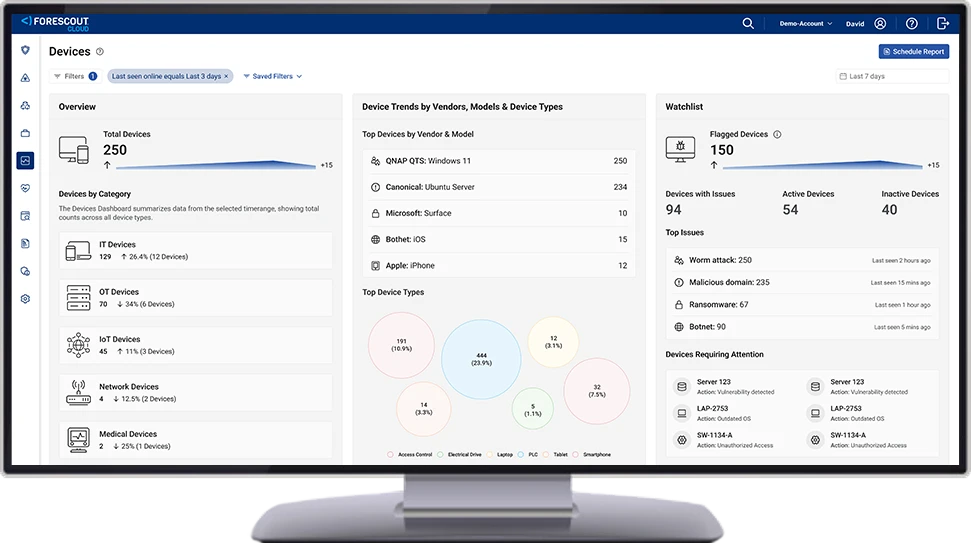
Smart Risk Scoring
Multi-factor scoring using configuration, behavior, and threat intel—including KEVs, EPSS, and IoCs.
Actionable Remediation
Specific plans to close exposure gaps and cut your mean-time-to-resolution.
Operational Efficiency
Real-time asset data available across IT and security teams for both proactive and reactive workflows.
How It Works
- Discover every asset across your environment
- Prioritize risk using agentic AI-powered analytics
- Validate security controls are working as intended
- Mobilize coordinated remediation across teams
This cloud-native platform deploys easily, so you can contextualize threats and make data-driven decisions that actually strengthen your security posture.
Ready to Stop Playing Defense Only?
Cybersecurity is evolving from reactive defense to proactive exposure management. CTEM represents this shift, and Forescout helps you continuously understand, prioritize, and reduce cyber risk in real time.
The Forescout 4D Platform™—including eyeSight, eyeFocus, and eyeAlert— provide comprehensive visibility, threat detection, and response.