2025H1 Threat Review
Vulnerabilities, Threat Actors, and Ransomware
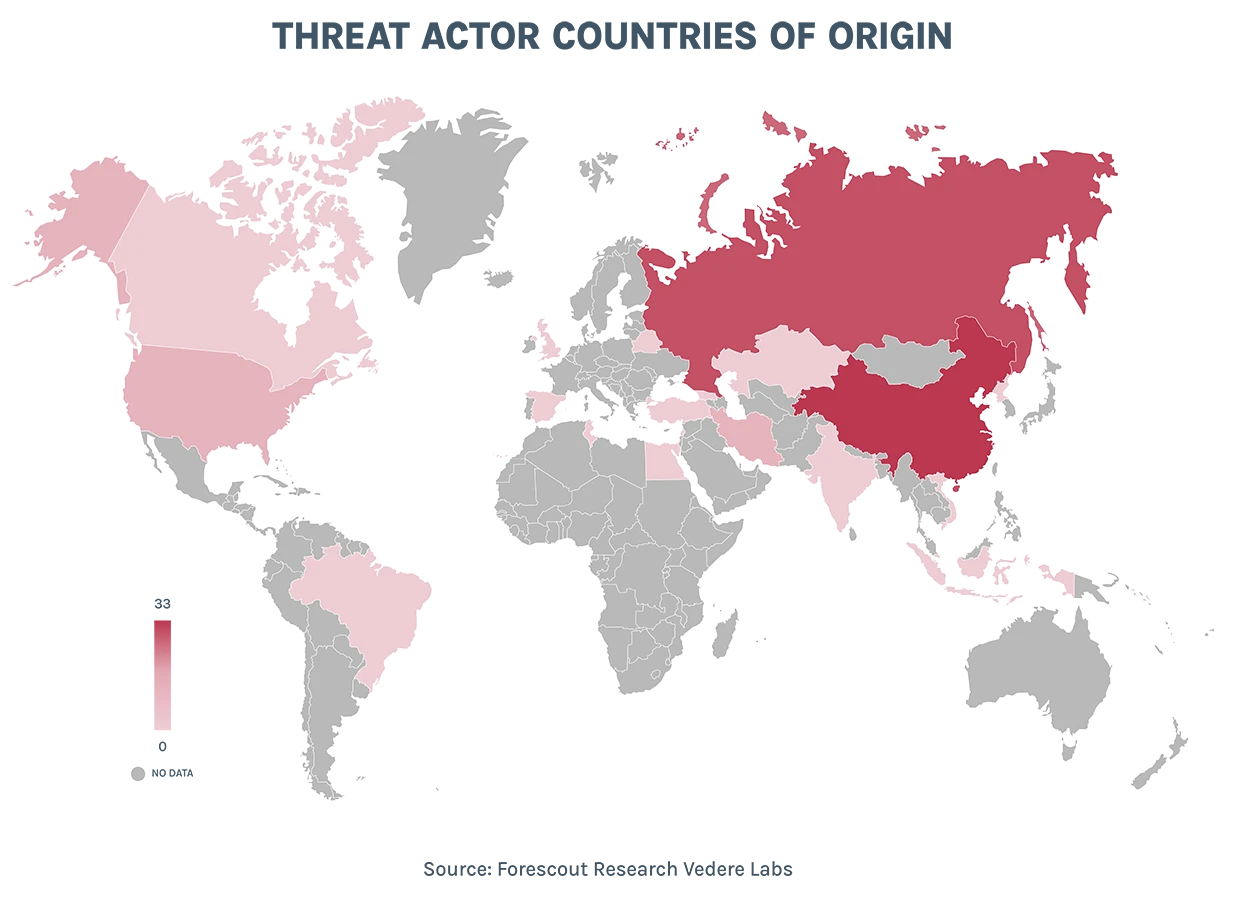
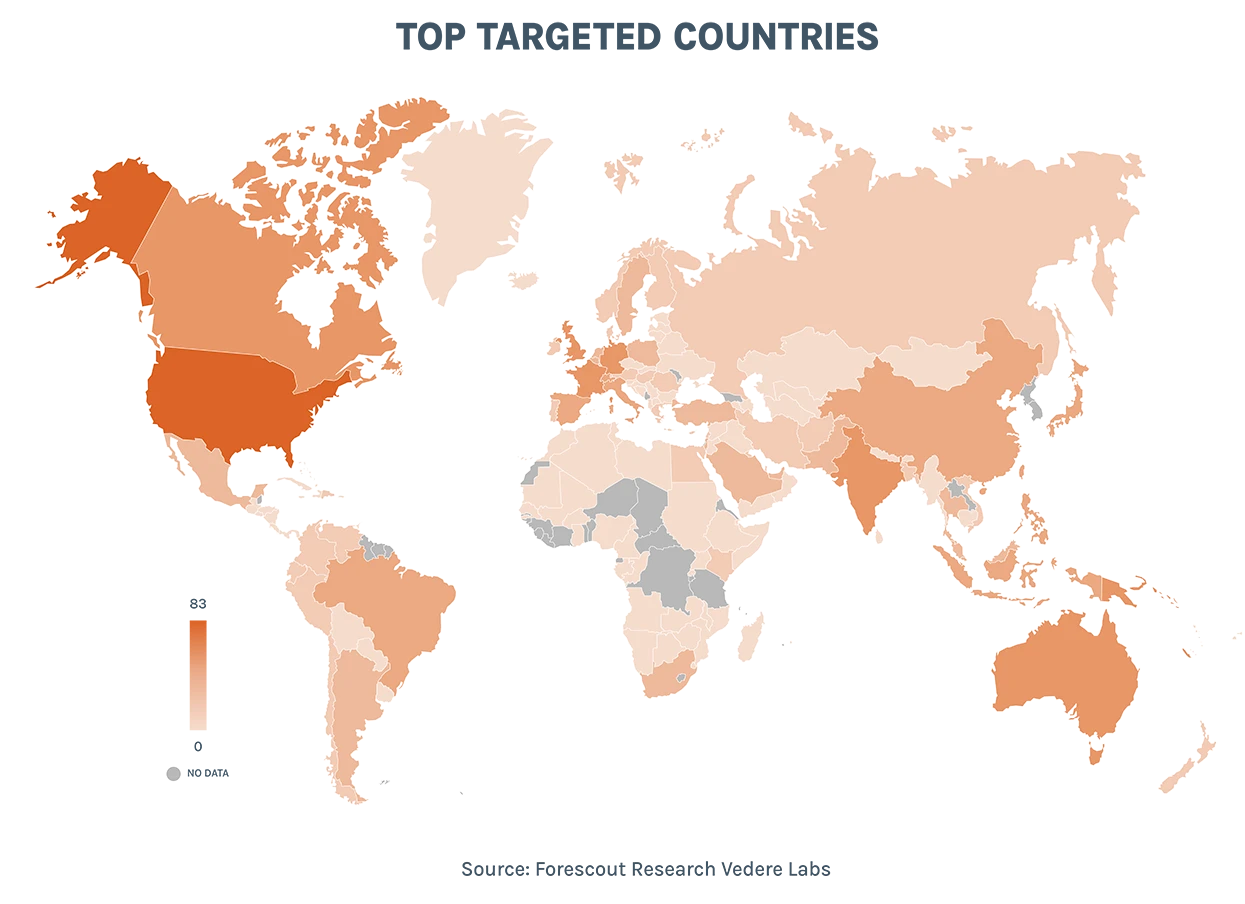
Once again, Forescout Research – Vedere Labs widens its mid-year lens with a macro look at the most pressing cybersecurity risks to date. From 3,649 ransomware attacks to state-sponsored intrusions to new trends in lateral movement, here are the new threat patterns and cyber attack behavior you need to know right now.