Major wormable SMBv3 RCE vulnerability hits modern Windows (CVE-2020-0796)
Incident Response Updates:
- Forescout customers using SilentDefense can now detect both vulnerable devices AND exploit attempts targeting CVE-2020-0976. To access Forescout’s latest SilentDefense SD-script, which includes coverage for CVE-2020-0976, ask your OT account representative.
- Forescout customers can identify vulnerable devices by downloading VR SMBGhost in the Forescout Security Policy Template (SPT) v20.0.03.
- Join the Research Discussion on how to control SMBv3 in the Forescout Community.
- The Forescout Windows Vulnerability Database plugin has been updated to include patching coverage of CVE-2020-0796. This provides specific coverage for Managed Windows devices.
Step aside EternalBlue, WannaCry and NotPetya – a new Windows Server Message Block protocol implementation vulnerability has taken center-stage.
The vulnerability, CVE-2020-0796 aka SMBGhost, is remotely exploitable. The issue was escalated in a notifiction by US-CERT following Microsoft’s Security Advisory.
Although there are no known exploits in the wild and barriers to weaponization, multiple security researchers have reported the remotely exploitable issue as one with high long-term impact potential. Currently, the challenge presented by KASLR bypass is the primary blocker to exploitation.
According to Microsoft’s advisory, the issue affects Windows 10 and Windows Server versions 1903 and 1909. The impacted Windows protocol implementation is Microsoft Server Message Block 3.1.1 (SMBv3), which runs over TCP port 445.
Five Fun Facts about the enterprise impact of SMBGhost / CVE-2020-0796
- Overall, 6% of managed Windows devices are vulnerable and have TCP port 445 open.
- 20% of enterprise Windows 10 devices are running Windows versions 1903 and 1909, which are the vulnerable versions.
- Nearly 30% of enterprise endpoints run Windows 10 Enterprise, making it the most popular Windows version in enterprises today.
- Windows 10 Professional (6.9%) is the third most popular version of Windows in the enterprise (Windows 7 comes in second place).
- A negligible number of devices are running the vulnerable version of windows Server (1909 and 1903). As Arun Raghuramu, Senior Staff Security Researcher said: “It’s an interesting case where older is potentially better. Most Windows Server instances are running older versions of Windows that simply don’t have this issue.”
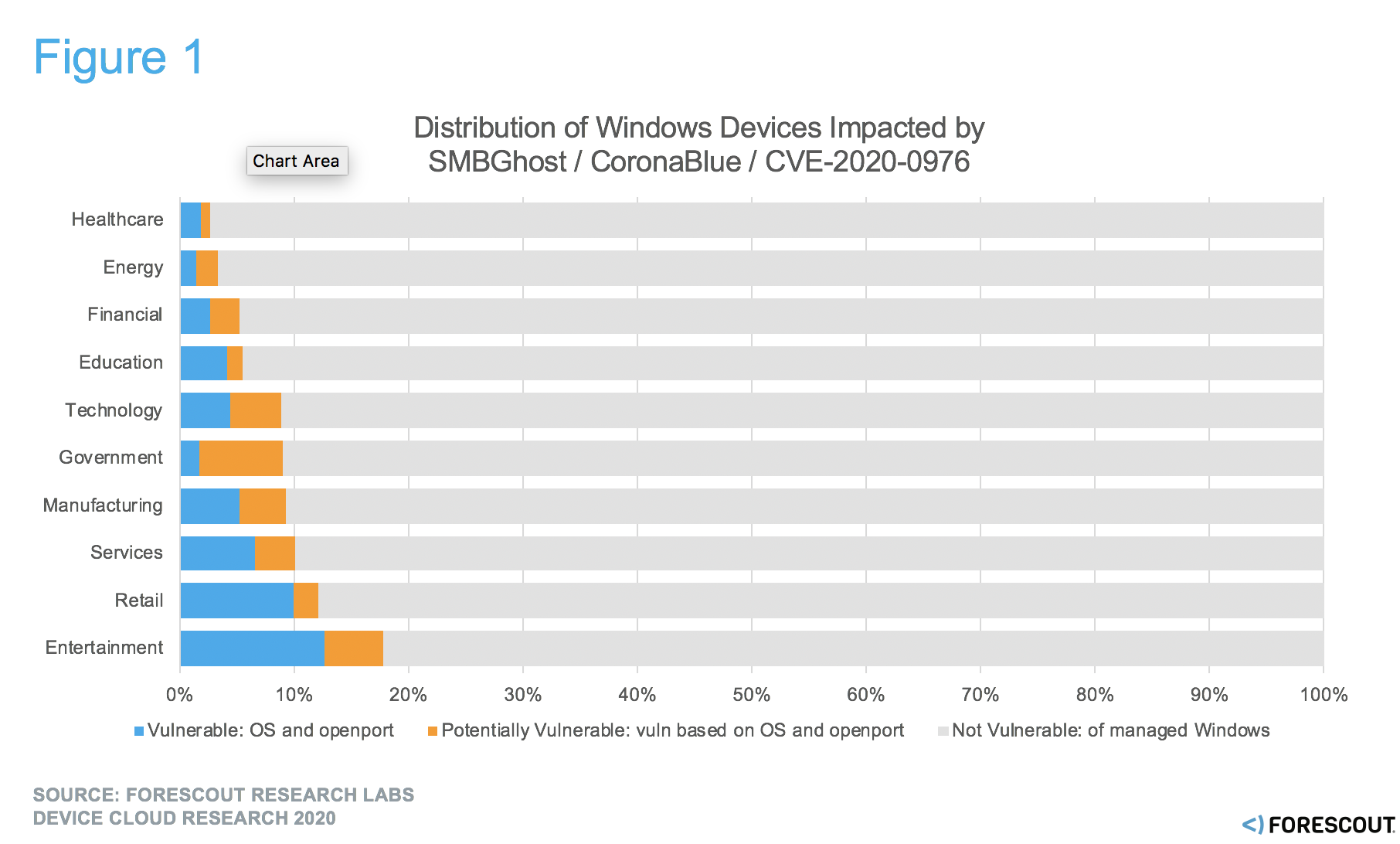
Figure 1. % of Managed Windows device operating systems impacted by need to patch
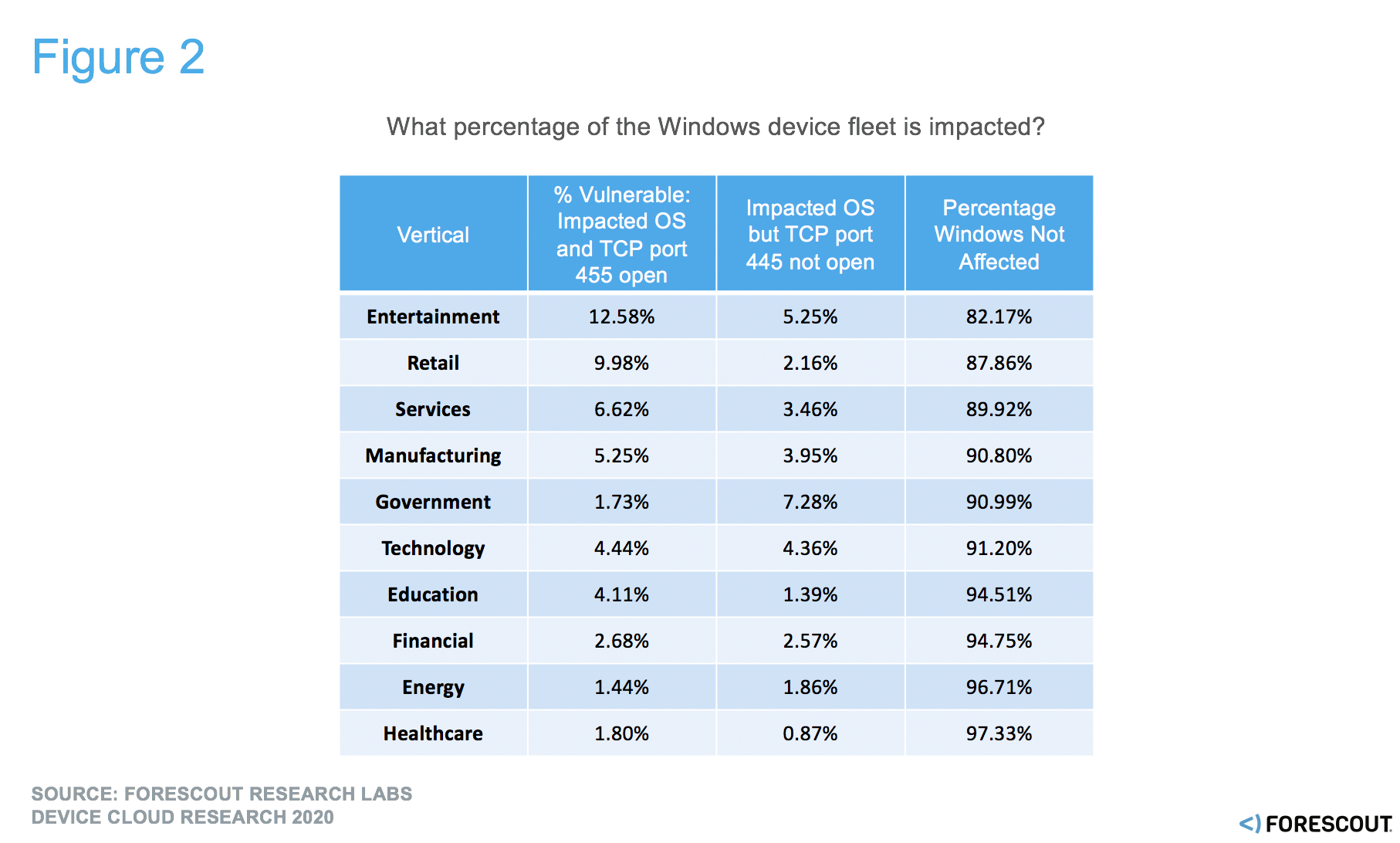
Figure 2. % of Windows devices with operating systems impacted by need to patch
What do we expect?
Forescout Researchers expect the issue will remain relevant for the coming months, as the barriers to weaponization and criminal commoditization are reduced.
As managing SMBv3 is uncharted ground, most enterprises are going to be caught unprepared. Enterprises generally suffered through technical challenges related to controlling SMBv1 in response to WannaCry. Now, issues with SMBv3 will lead to frustration, and uncertainty of what to do and how to control the issue at a protocol level.
On the bright side, we don’t expect the long-term impact to be anywhere near as devastating as WannaCry or NotPetya due to:
- Internal discovery by Microsoft granting more time to prepare before day zero.
- Limited use of SMB protocol implementation 3.1.1.
- The generally improved state of device management for modern Windows devices in the enterprise when compared to the state of Windows as of 2017, when WannaCry spread.
- The higher rate at which recent Windows devices are enabled for automatic updates.
- Technical barriers to exploitation.
While some researchers point out the high technical barriers of bypassing KASLR, which is required for full exploitation, ZDNet’s Catalin Cimpanu has tweeted that finding the bug is trivial and PoC exploits will likely arrive soon. In the meantime, security practitioners will be crafting and releasing technical security controls to identify and mitigate the issue.
Recommendations
- Visibility: Use Forescout to identify and classify potentially impacted Windows 10 and Windows Server instances by version number in your environment. Include Windows OS version number in your configuration management database (CMDB).
- Control: Leverage Forescout’s out-of-the-box ability to identify Windows systems with vulnerable registry key settings. Use the ability to retrieve and modify these registry properties to mitigate the vulnerability—Forescout can be used in place of Microsoft’s powershell workaround across the managed device fleet.
- Segmentation: As an ongoing best practice, use Forescout to monitor SMB flows over TCP port 445 – these flows should never exit the corporate intranet, should be monitored for anomalies, and should be controlled via segmentation. Upon detection of violation, enact device restriction policies to mitigate risk to the network and prevent lateral movement.
- Microsoft guidance: Disable SMBv3 compression and preventing SMB traffic from lateral connections and entering or leaving the network. Forescout can be used directly to action this guidance on the network as technical security policy.
Conclusion
Having the capability to control network protocols like SMBv3 is a must-have for enterprise security today. “In real enterprise environments, it’s the visibility into network protocols and flows that gives us what we need to enforce security policy and mitigate the East-West communication of SMB traffic” said Shawn Taylor, Senior Systems Engineer at Forescout.
To discuss device visibility and control in response to emerging threats like SMBGhost / CVE-2020-0796, join the Research Discussion on how to control SMBv3 in the Forescout Community.
References
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV200005
- https://www.us-cert.gov/ncas/current-activity/2020/03/11/microsoft-server-message-block-rce-vulnerability
- https://support.microsoft.com/en-us/help/3185535/preventing-smb-traffic-from-lateral-connections
- https://twitter.com/campuscodi/status/1237737910943780864
- https://www.bleepingcomputer.com/news/security/microsoft-leaks-info-on-wormable-windows-smbv3-cve-2020-0796-flaw/
- https://arstechnica.com/information-technology/2020/03/windows-has-a-new-wormable-vulnerability-and-theres-no-patch-in-sight/