In today’s hyper-connected world, securing a sprawling ecosystem of heterogeneous devices without slowing down business operations is mission critical. Visibility gaps and unmanaged endpoints have become prime targets for attackers, and traditional security models often fall short in addressing these risks.
This isn’t hyperbole. The abundance of unique, industry-specific digital assets is jaw-dropping. Our researchers at Vedere Labs keep close tabs on “extended IoT” and have discovered far-reaching device sprawl. In our analysis of 10 million devices in over 700 organizations, we find:
- 380 device functions – an average of 164 per organization
- 5653 vendors – an average of 1629 per organization
- 3200 operating system versions – an average of 876 per organization
One popular IP camera vendor has 206 unique firmware versions to manage with nearly half (49%) of them finding “end of support” status at the end of this year.
Attackers aren’t waiting for your migration plans.
That’s why Forescout is proud to introduce eyeSentry, a cloud-native solution designed to redefine how organizations anticipate, prioritize, and mitigate cyber threats before they impact their networks.
“With eyeSentry, we’re redefining how enterprises confront hidden risk,” said Barry Mainz, CEO of Forescout. “When unseen devices become attack vectors, the stakes aren’t just data—they’re operational continuity and trust. For over two decades, Forescout has set the standard in device intelligence, and now we’re bringing that expertise to the cloud, giving organizations the visibility and context they need to stay ahead of adversaries, including nation-state actors.”
Go deeper: See exactly where today’s hidden risks are found from Forescout’s Vedere Labs.
Why Continuous Threat Exposure Management Matters
eyeSentry is a strategic response to the evolving threat landscape. It’s an evolution from static defense to continuous, dynamic evaluation.
That’s where continuous threat exposure management (CTEM) comes in. CTEM is a proactive approach that continuously identifies exposures, prioritizes risks, and enables rapid remediation—before attackers’ strike.
eyeSentry operationalizes CTEM by automating real-time device intelligence, risk-based analytics, and threat intelligence and mitigation in a scalable, easy-to-deploy, cloud-native solution.
According to industry research, the number of connected IoT devices is expected to grow by 14% to 21.1 billion in 2025, and will reach 39 billion in 2030, creating a massive blind spot ripe for exploit.
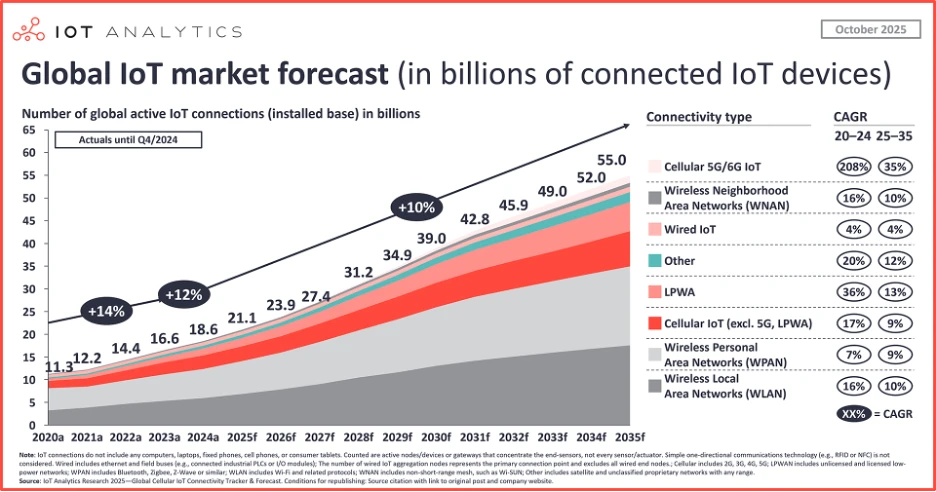
Source: IoT Analytics
Simply put, organizations need solutions that combine automation, intelligence, and human expertise to stay ahead of attackers.
eyeSentry delivers exactly that. It builds on Forescout’s proven leadership in device intelligence and exposure management, extending these capabilities into a dynamic, cloud-native solution that supports a robust CTEM program.
What Does eyeSentry Do?
eyeSentry’s capabilities align with Forescout’s broader mission: to deliver automated cybersecurity at scale, enabling organizations to reduce operational risk while accelerating digital transformation, including:
- Providing comprehensive asset visibility. unifies discovery and classification of every connected device—managed or unmanaged—across IT, IoT, and medical environments, without disrupting critical operations. It incorporates passive and active discovery techniques to provide detailed, context-rich device intelligence.
- Prioritizing which assets are most at risk. Leveraging advanced analytics, organizations can focus on what matters thanks to automated ranking of exposures based on threat intelligence, known vulnerabilities, and business impact.
- Performing automated assessments of your security controls, so you can verify that security safeguards are implemented correctly, operating as intended, and producing the desired outcomes.
- Detection and response to advanced cyber threats, reducing alert fatigue and maximizing resource efficiency
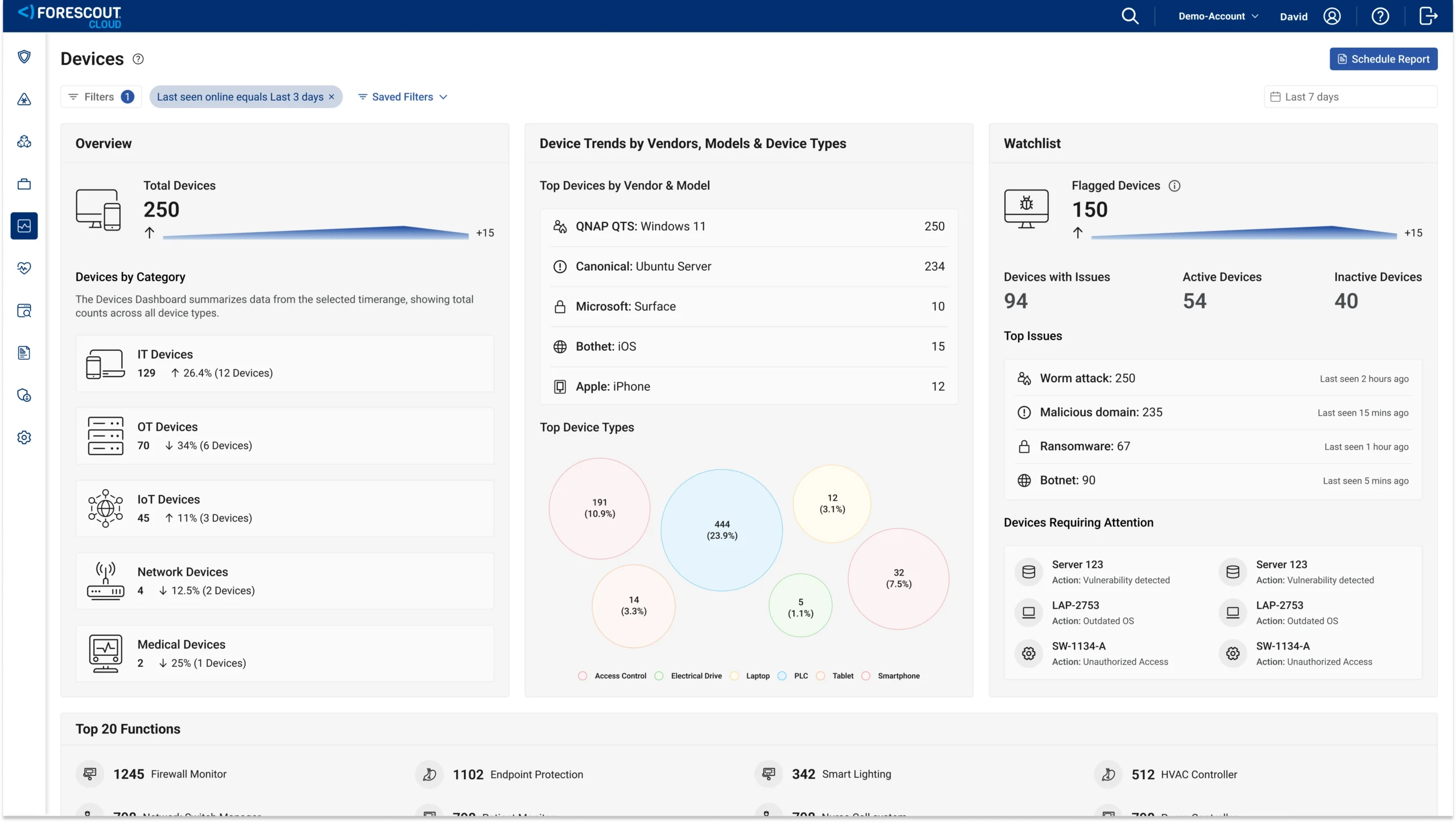
Here is eyeSentry. Here is the main dashboard:
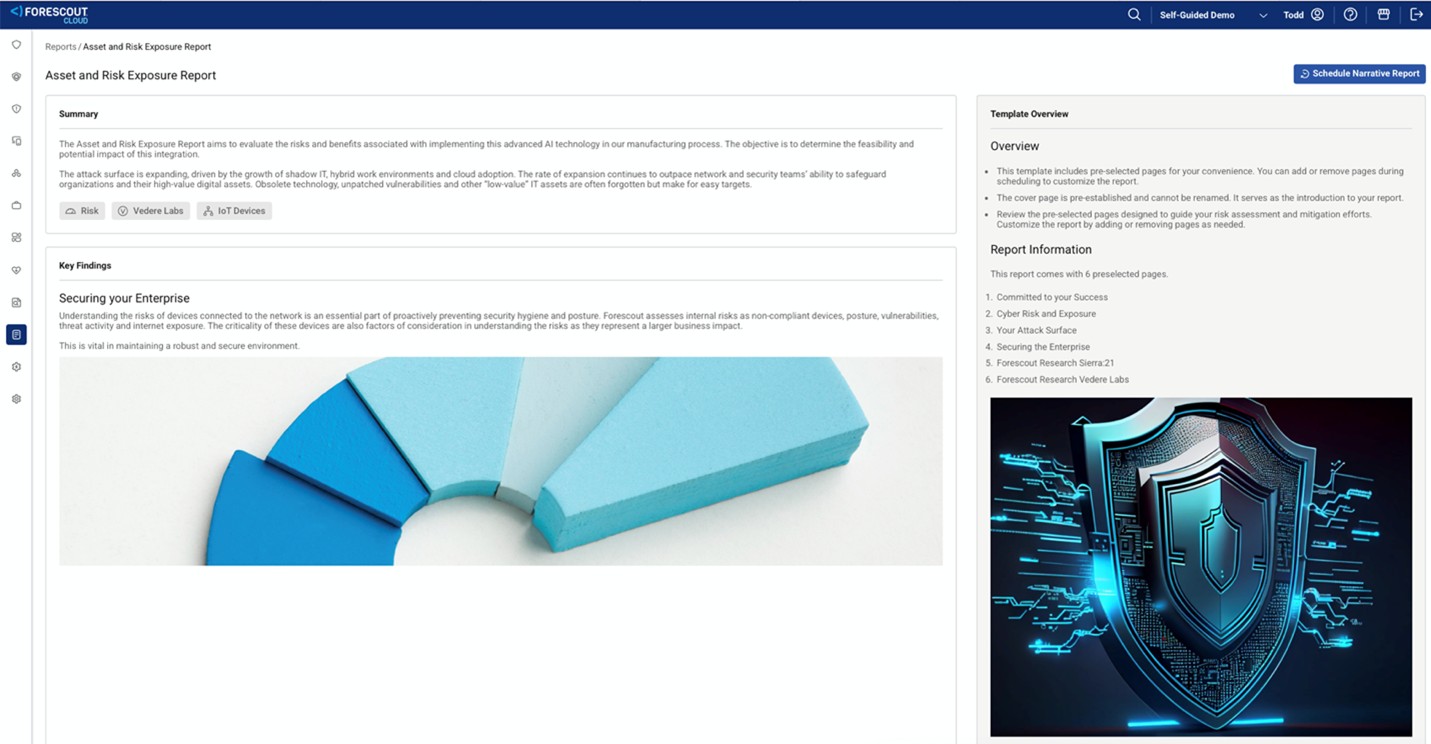
Here is the reporting dashboard powered by AI:
Continuous threat exposure management follows a pivotal shift within the cybersecurity industry. It signals a movement toward proactive exposure management—a model that anticipates threats rather than merely reacting to them.
For organizations, this means:
- Greater resilience against sophisticated attacks.
- Improved compliance with evolving regulatory mandates.
- Operational efficiency, as security becomes an enabler rather than a barrier.
Looking Ahead
The journey starts here. In the coming months, you’ll gain access to new features, expanded partner integrations, and practical resources designed to help you get the most out of eyeSentry. Look forward to actionable insights, technical guidance, and real-world success stories that show how you can turn cybersecurity from a reactive task into a strategic advantage for your organization.
Join the Movement
Follow Forescout on LinkedIn for updates and explore how CTEM and eyeSentry can transform your cybersecurity strategy:
Get the CTEM Solution Brief
Get the eyeSentry Datasheet
Get the Gartner CTEM analyst report
Get our e-Book: “Build Operational Resilience with Continuous Threat Exposure Management (CTEM)”
Go deeper: See why CTEM is the future of proactive cybersecurity.