Department of Justice disrupts Moobot botnet commandeered by Russian APT28: analysis of attacks against routers and malware samples
On February 15, the US Department of Justice announced “Operation Dying Ember”: the takedown of a botnet controlled by APT28, the Russian military cyber threat actor also known as Fancy Bear. APT28 was previously known for developing the VPNFilter botnet, which targeted routers and network attached storage devices and was also disrupted by the DoJ in 2018.
The new operation targeting Moobot came about two weeks after the disruption of the KV botnet, which was in turn built and operated by the Chinese APT Volt Typhoon.
What is interesting in this new APT28 case is that instead of building a botnet from scratch, the threat actor leveraged an existing cybercriminal botnet: the Mirai variant known as Moobot.
In this blog post, we summarize what is publicly known about the APT28 Moobot campaign and present an analysis of related events targeting Forescout’s Adversary Engagement Environment (AEE).
A summary of the APT28 Moobot campaign
According to the DoJ notice, the takedown operation happened at an unspecified date in January and the APT28-controlled botnet consisted of thousands of Ubiquiti Edge OS routers that were hijacked to build a “global espionage platform.” Cybercriminals first installed Moobot on routers that used default administrator credentials. These credentials were not mentioned by the DoJ, but are available on public documentation: “ubnt”/”ubnt”
APT28 then leveraged Moobot to download their own malicious files into the victim routers and repurposed the botnet for espionage, conducting spearphishing and credential harvesting campaigns as well as exfiltrating stolen data.
Analysis of attacks against Ubiquiti routers on Forescout’s AEE
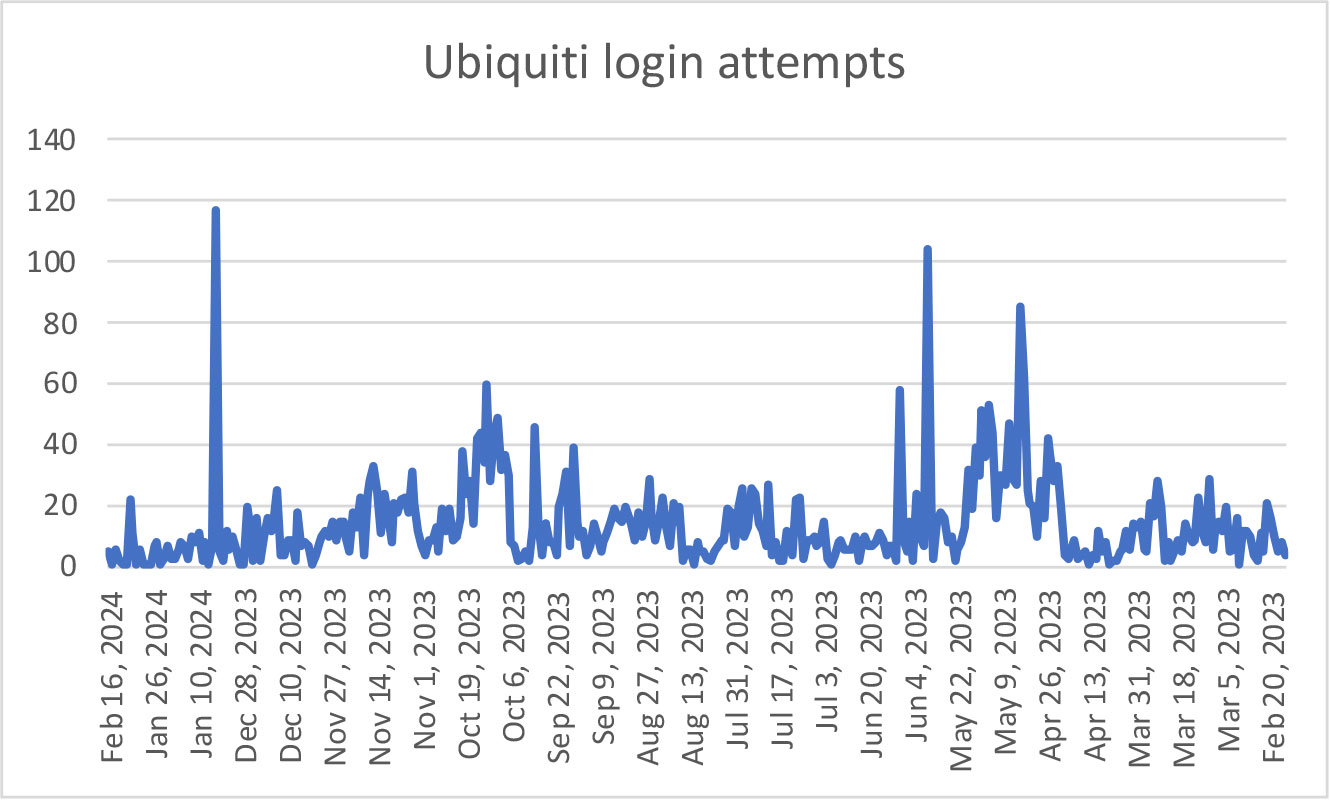
We registered 4,815 attempts to login with “ubnt” credentials on the AEE between 15 February 2023 and 16 February 2024 (the day after the announcement of the operation). The highest peak of attempts was on January 5, 2024 (which was possibly before the takedown operation) where we saw 117 attempts. Other relevant peaks were in May 31, 2023 (104 attempts) and May 4, 2023 (85 attempts).
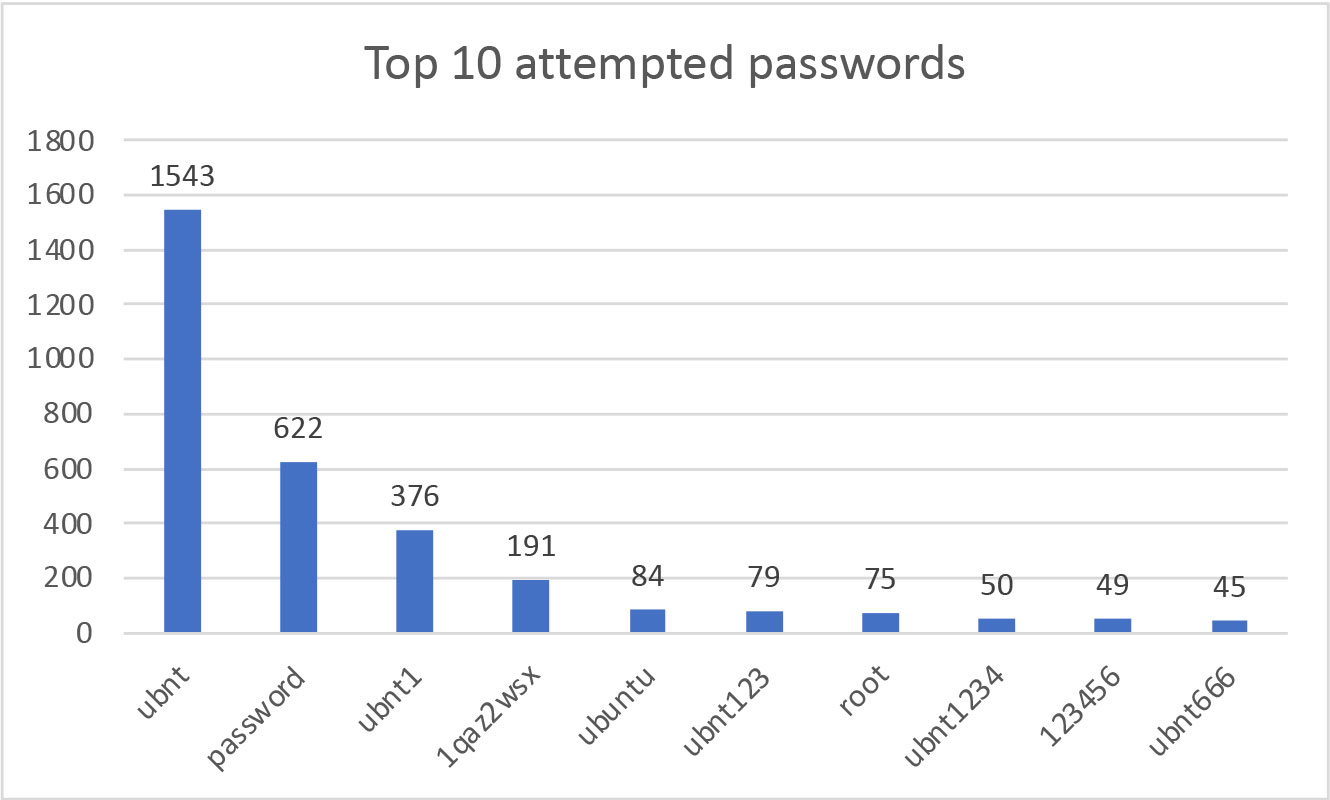
These attempts used 129 different passwords, with the top 10 shown below, which are mostly variations of “ubnt” itself:
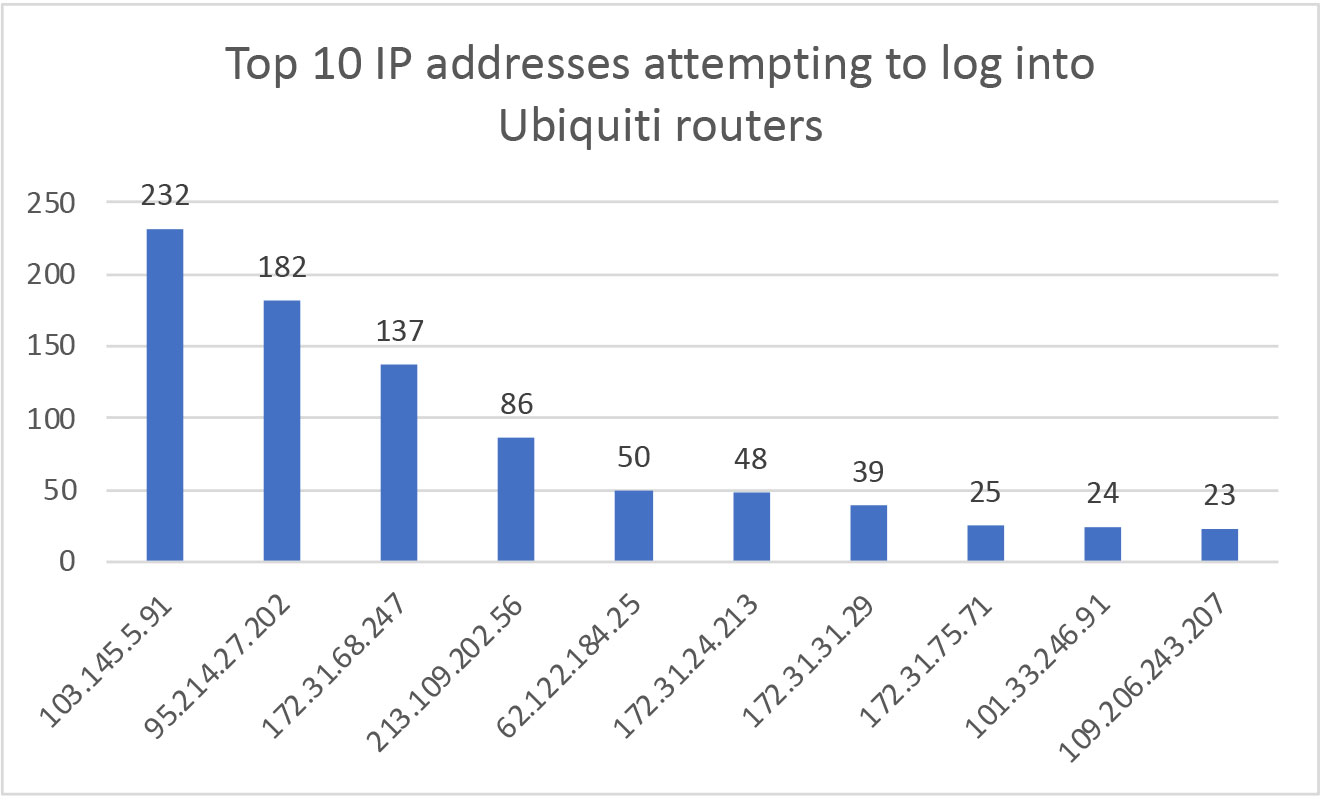
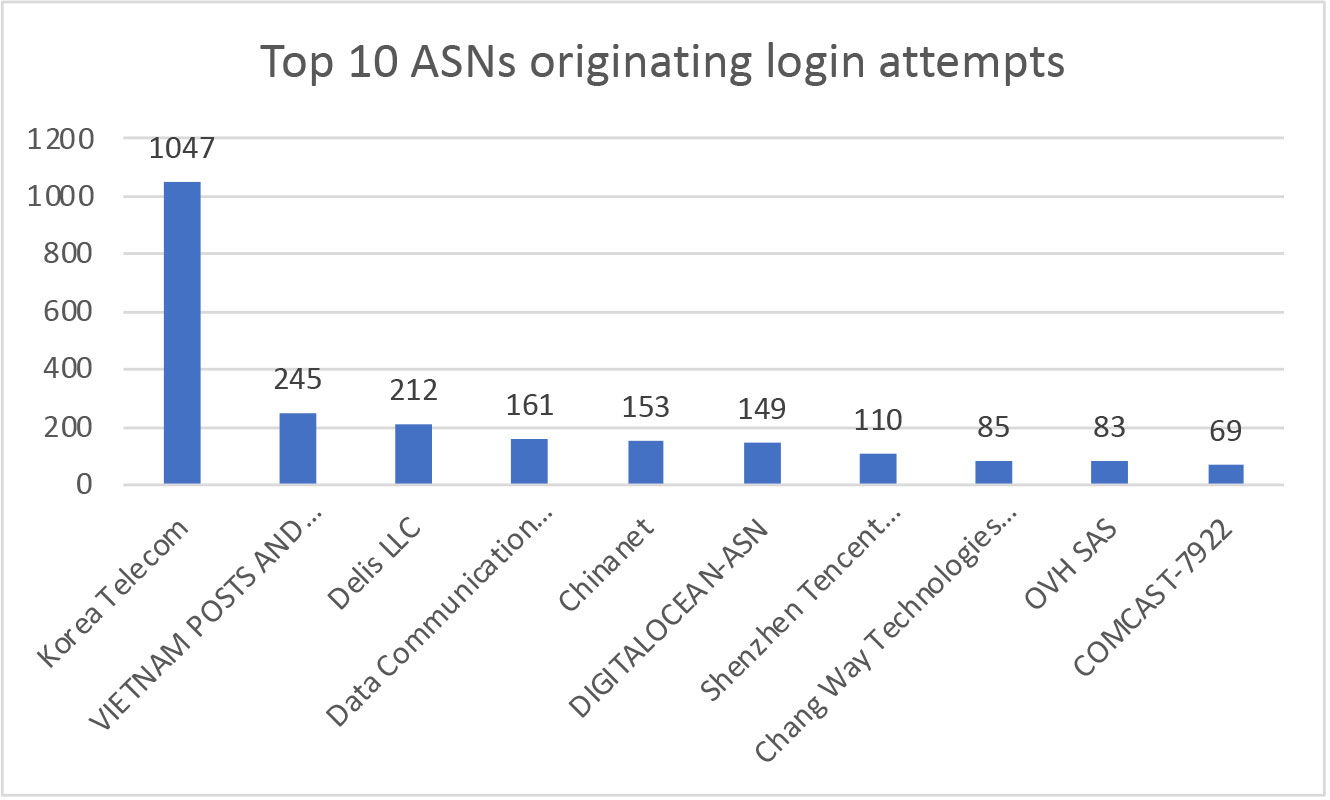
Those attempts came from 1,732 different IP addresses. The top attacking IP address (103[.]145[.]5[.]91) was responsible for 232 attempts (5%) and the top 10 IP addresses, shown in the figure below, did 17.5% of the attacks.
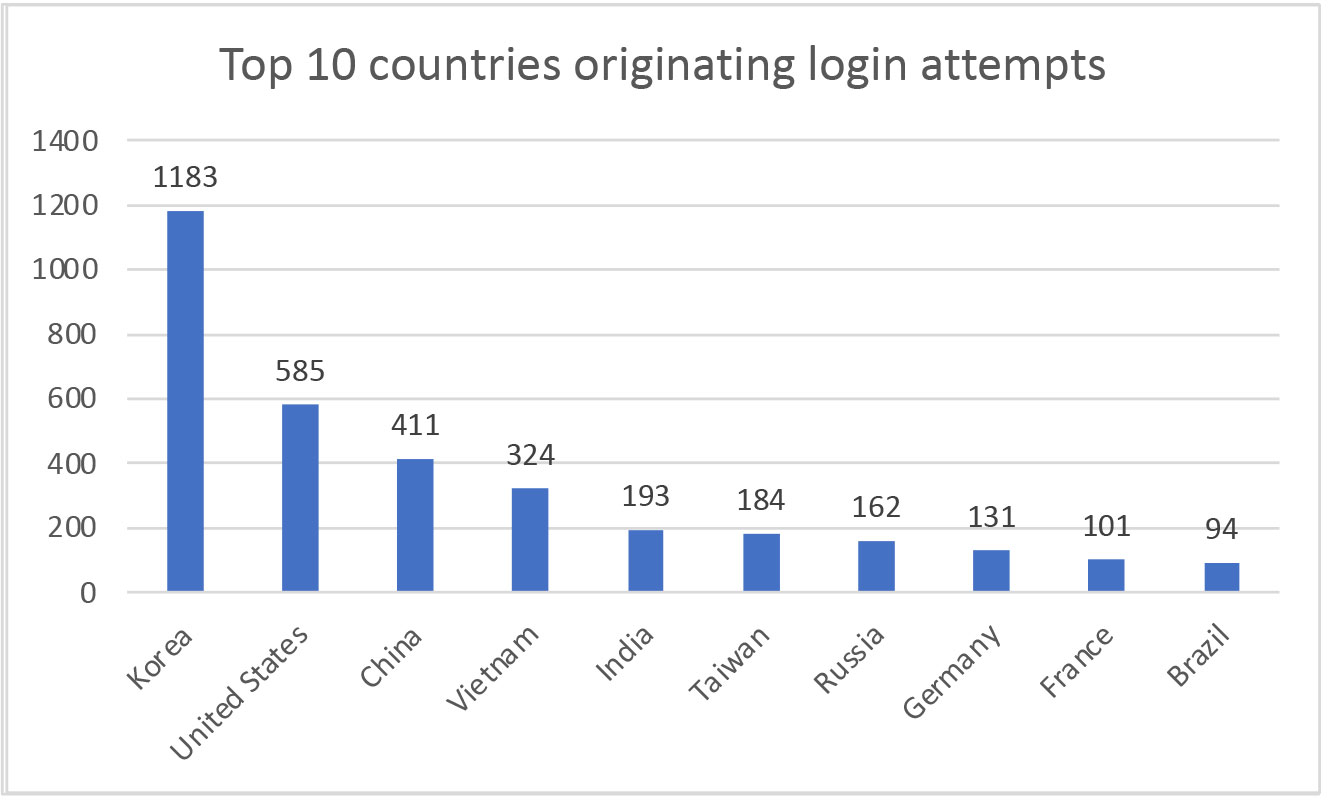
Login attempts came from 101 countries. The country originating most login attempts was Korea, while Russia was the top 7 country with 162 attempts.
Most of the IP addresses attempting logins were managed by ISPs, which indicate they could come from compromised devices, but some belonged to hosting providers, such as DigitalOcean and OVH, which indicates leased criminal infrastructure.
The variety of Moobot samples
Moobot is a Mirai botnet variant that has been active since at least 2019 and spreads mainly over Telnet (credential brute-forcing and default IoT device credentials). Additionally, the botnet has been observed spreading via vulnerabilities on several IoT devices such as Tenda (CVE-2020-10987, CVE-2018-14558, CVE-2017-17215, CVE-2014-8361) and D-Link routers (CVE-2015-2051, CVE-2018-6530, CVE-2022-26258, CVE-2022-28958), Hikvision cameras (CVE-2021-36260) and even 0-days on Chinese DVR equipment, such as UNIX CCTV and LILIN. The botnet has been used mainly in DDoS attacks (including against Ukraine) and the DDoS functionality seems to be no different than in the original Mirai.
We have been observing Moobot as a popular Mirai variant since 2022. There are currently more than 3,000 cataloged Moobot samples, 77 of which have been observed in the first half of February 2024. Those 77 samples were distributed from the following IP addresses and domain names:
- 196.10[.]60
- 9.30[.]146
- 96.2[.]220
- 155.81[.]228
- 116.105[.]27
- 81.39[.]193
- nguyennghi[.]info
They also contacted the following potentially malicious domain names, as well as more than 480 IP addresses, the most popular of which was 103.155.81[.]228
- joshan[.]fun
- awuam[.]com
- qyh.co[.]ua
- srothuynguyen[.]com
- thisone[.]online
- cltxhot[.]fun
Conclusion
The most interesting aspect of this campaign is the reuse of criminal infrastructure by an APT group, especially IoT-based infrastructure. We have discussed in the past how compromised IoT devices could be handed over to other cybercriminals for further attacks (similar to what initial access brokers do with mostly IT devices) and hinted to this possibility as recently as on our analysis of botnets attacking Zyxel firewalls in Danish energy companies.
Seeing this now realized by a threat actor as experienced as APT28 should have organizations concerned. Therefore, we consider the following three risk mitigation recommendations to be crucial for organizations:
- Ensure that you have full visibility of every asset in your network, including unmanaged IoT assets such as routers, IP cameras, network attached storage, DVR, building automation and others that are frequently targeted by botnets.
- Ensure that your IoT devices use strong credentials, do not expose unnecessary services and are patched against known vulnerabilities to prevent them from being compromised by threat actors.
- Segment these devices from the rest of your network to prevent breaches that start on these devices to spread further to critical parts of your organization.