Key Findings
- In 2024, there was a 71% increase in threat actors targeting manufacturing.
- Between 2024-2025 Q1, there were 29 active threat actors in manufacturing:
- 79% of those were cybercriminals
- 45% were ransomware gangs
- Most active: RansomHub with 78 victims, including large data thefts
- We analyzed 17 incidents to derive common tactics, techniques and procedures and discovered:
- An increased use of Initial Access Brokers
- Exploitation of vulnerabilities in specific applications:
- VPNs
- Remote access solutions
- File transfer applications
- The use of legitimate remote monitoring and management tools for persistence and execution.
- A shift from malware obfuscators to EDR bypass tools
- The use of custom malware alongside living-off-the-land techniques
Recommendations
- Inventory and harden assets, especially those that are internet-facing
- Enhance visibility and detection, including managed and unmanaged assets
- Secure the IT/OT boundary with segmentation and threat detection
- Address supply chain risk with requirements for third-party providers
- Implement and test backup and recovery
- Follow focused threat intelligence for better threat models and playbooks
- Secure emerging technologies with dedicated risk assessment
The manufacturing sector has consistently ranked among the most heavily impacted by ransomware groups, and other threats, such as data breaches. The sector includes a wide range of industries — from automotive and electronics to chemicals and heavy machinery.
In our 2024 Threat Roundup, manufacturing ranked fourth among the most targeted critical infrastructure sectors in 2024 — while the number of threat actors increased by 71%. Given this major increase, we decided to look closer.
Here, we drill down into the cyber threat landscape for the manufacturing sector with an outlook into future threats, and our recommendations for risk mitigation. Emerging technologies, eg. digital twins, IIoT, 5G, and AI, all bring new security implications — and gaps in threat detection.
Cybersecurity in Manufacturing: Threat Landscape, 2024-2025 Q1
Threat Actors
Using data from our Threat Actor Knowledgebase, we identified 121 actors that have historically targeted manufacturing. Drilling down into those active between 2024 and 2025 Q1, we identified 29 actors.
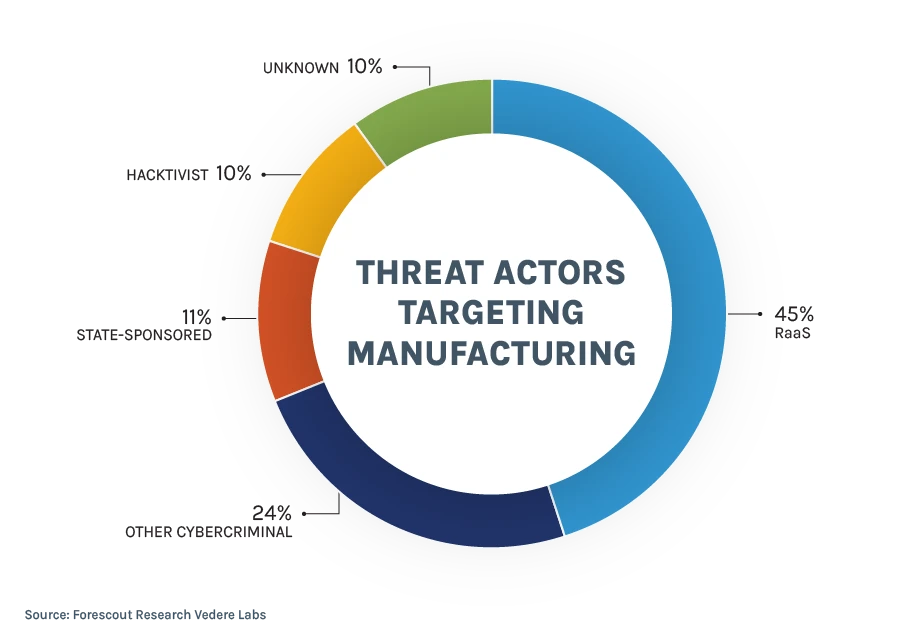
Clearly, most actors targeting the sector are cybercriminals, especially those in the Ransomware as a Service (RaaS) category. At the top was RansomHub, which claimed 78 global manufacturing victims in 2024 — and was responsible for large data thefts in the sector. Other highly active RaaS groups include Akira, LockBit, Play, and Clop.
Even with high-profile law enforcement operations, such as Operation Cronos, targeting some of these huge groups, they continued to operate either with the same name or by rebranding. Code reuse and affiliate sharing also contributed to the fragmentation of the RaaS ecosystem — with some groups emerging from other groups that disappeared.
Other relevant groups but with less activity in manufacturing include: Fog, Medusa, Qilin, BlackSuit, 8Base, Hunters International, Black Basta, Snake/EKANS, INC ransom, BianLian, Metaencryptor, Sarcoma, Space Bears, Everest, Ghost (Cring), Dragonforce, Frag, and Lynx.
Across these groups, multi-platform ransomware is now standard across targets of Windows, Linux, and ESXi systems. We present detailed capabilities of some of these actors at the end of this blog.
Other types of actors that targeted the sector include:
- Hacktivist groups, such as Handala, Kill Security, CyberVolk and Cyber Army of Russia Reborn, who deployed ransomware or conducted disruptive attacks against OT systems in manufacturing organizations. These groups often align with geopolitical conflicts.
- State-sponsored groups, such as APT28 and Volt Typhoon, specifically target OT/ICS environments, including those in manufacturing-related sectors. Another state-sponsored actor, Emperor Dragonfly, was observed deploying RA World ransomware following espionage activities.
Common TTPs and Observed Trends
Out of the hundreds of incidents affecting manufacturing companies, we analyzed a subset of 17 to derive common TTPs and decipher evolving trends.

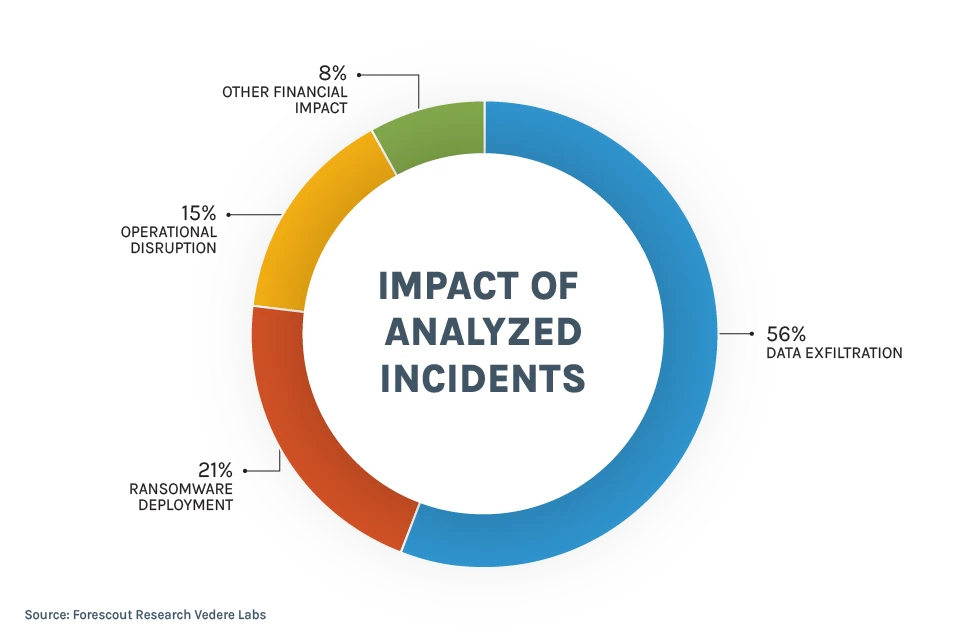
Data exfiltration was the most common impact, including: intellectual property of affected organizations, and sensitive personal data of employees and customers —social security numbers, bank account details, and passports. Across the cases we analyzed, there were more than 3.3TB of data stolen. RansomHub was responsible for the largest exfiltration cases of 2TB and 487GB.
The main TTP trends we observed in the period were:
- Initial Access: Increased use of IABs and exploitation of vulnerabilities in specific applications, such as VPNs, remote access solutions, and file transfer applications.
- Persistence, Execution, and C2: Legitimate tools used for remote monitoring and management (RMM) have seen significant increase for persistence and execution. Often, tasks are executed using native functionality of the RMM tool, such as opening a shell to execute commands. Other techniques such as user creation, scheduled task and web shells remain prevalent.
- Privilege Escalation: The use of Cobalt Strike for post-exploitation has reduced, but it is still seen for credential dumping and access token manipulation.
- Defense Evasion: There has been a notable shift from obfuscators to EDR bypass tools, such as KillAV, TrueSightKiller, and EDR Kill Shifter, alongside ‘bring your own vulnerable driver’ (BYOVD). These tools are used to disarm endpoint telemetry and are now standard ransomware precursors, replacing former activities like event-log purging and obfuscation.
- Discovery: Threat actors have moved to using Active Directory Service Interfaces (ADSI) due to advances in detecting pre-built PowerShell tools for internal discovery.
- Exfiltration: Data exfiltration is now a standard practice among most groups and some show preference for specific tools, such as Rclone or MEGA.
Go deeper: See all the mega trends happening across many industries, including energy which saw a 93% increase in threat actors.
Watch the Webinar Overview with Daniel dos Santos, Head of Research.
The table below lists the most common TTPs observed in manufacturing incidents in this period.
| Tactic | Technique | Examples | Frequency |
|---|---|---|---|
| Initial Access | T1190: Exploit Public-Facing Application | Exploiting vulnerabilities in VPNs, file transfer applications, RDP, Exchange and SharePoint using Metasploit or exploit scripts. |
High |
| T1566: Phishing | Spear phishing emails with malicious links to fake login pages or malicious document attachments. SocGholish framework. |
High | |
| T1078: Valid Accounts | Compromised credentials from IABs, phishing or breaches on VPNs and RDP. | High | |
| T1133: External Remote Services | Accessing exposed RDP or VPN services. | High | |
| Execution | T1059: Command and Scripting Interpreter | PowerShell, cmd.exe and Python. | High |
| Persistence | T1136: Create Account | Creating new local or domain admin accounts using net user and Active Directory tools. | Medium |
| T1219: Remote Access Software | Deploying legitimate tools like AnyDesk, ConnectWise or SimpleHelp for persistent C2. | Medium | |
| Privilege Escalation | T1003: OS Credential Dumping | Mimikatz, Cobalt Strike hashdump, LSASS dumping. | High |
| Defense Evasion | T1562.001: Disable or Modify Tools | Disabling AV/EDR via PowerShell scripts, tools such as KillAV and TrueSightKiller or BYOVD. | High |
| T1027: Obfuscated Files or Information | Base64 encoding, code obfuscators such as PyObfuscate and GoObfuscate. | High | |
| T1070: Indicator Removal | Clearing logs such as PowerShell history and wevtutil, deleting tools. | Medium | |
| Various Living off the Land (LOTL) techniques | Using built-in tools such as PowerShell, WMI, PsExec, RDP, certutil, schtasks, nltest, Adfind | High | |
| Lateral Movement | T1569.002: Service Execution | Using PsExec for remote command execution. | High |
| T1021: Remote Services | Moving via RDP or accessing admin shares (SMB). | High | |
| Cobalt Strike (Various Techniques) | Using Cobalt Strike framework for C2, lateral movement, execution. | Medium | |
| Collection | T1560.001: Archive via Utility | Compressing stolen data using 7-Zip or WinRAR. | Medium |
| Exfiltration | T1567: Transfer Data to Cloud Account | Using Rclone, MEGAcmd, AxCopy and cloud provider tools such as AWS CLI to exfiltrate data. | Medium |
| Impact | T1486: Data Encrypted for Impact | Core ransomware payload execution. | High |
| T1490: Inhibit System Recovery | Deleting Volume Shadow Copies, targeting backups via vssadmin.exe, wmic.exe, bcdedit.exe. | High | |
| Various OT disruption techniques | Halting production, manipulating HMIs and causing physical effects via ransomware impact or OT-specific malware. |
Medium |
Cybersecurity in Manufacturing Outlook
Our analysis of the manufacturing threat landscape in 2024 and 2025 Q1 has revealed key trends such as:
- An increase in attacker dwell time
- Use of legitimate cloud services for exfiltration
- Use of custom tools, such as Black Basta’s BRUTED or RansomHub’s Betruger backdoor, and LOTL techniques.
- Hacktivists adopting ransomware and state-sponsored groups targeting OT
We expect these trends to shape the threat landscape in the near future:
- A higher volume of attacks: The evolving RaaS ecosystem indicates that attack volume will likely remain elevated.
- An increase in OT targets: As more attackers gain a deeper understanding of OT environments, we will see an increase in targeting these assets.
- More actions influenced by geopolitics: State-sponsored or hacktivist operations using ransomware-like tactics for disruption may become more common, particularly targeting critical manufacturing sub-sectors.
Furthermore, as more organizations adopt cloud technologies, we may see more attacks leveraging cloud misconfigurations. Compounding these risks, there are other emerging technologies in the sector that will bring new security implications, such as:
| Technology | Security Implications | Detection Gaps |
|---|---|---|
| Digital twins | Risks to data models, potential for sabotage | |
| Industrial Internet of Things (IIoT) | Expanded attack surface, potential for compromise | Lack of endpoint telemetry |
| 5G | New vectors for initial access, C2 and data exfiltration | Encrypted traffic visibility |
| AI/ML in Production | Potential for algorithm manipulation and data poisoning | Algorithm behavior baseline |
These current and upcoming challenges necessitate a proactive and adaptive security strategy for manufacturing organizations based on the following items:
- Inventory and Harden Assets: To address initial access vectors, ensure that you have a full inventory of assets in the network, including their current risk levels and known vulnerabilities. This information can be used to harden assets by:
- Patching vulnerabilities, prioritizing internet-facing systems, especially VPNs, RDP and firewalls.
- Using complex, unique passwords.
- Enabling multi-factor authentication whenever possible.
- Enhance Visibility and Detection
- Enable comprehensive logging in every asset by deploying and configuring EDR or native logging capabilities.
- Use SIEM and threat detection solutions to detect the use of LOTL techniques and anomalous activity.
- Secure the IT/OT Boundary: Segment the IT and OT networks and monitor traffic crossing the boundary for exploitation of known vulnerabilities or anomalies.
- Address Supply Chain Risk:
- Establish baseline security maturity requirements for critical software and service providers.
- Monitor for breaches related to third-party tools used within the organization.
- Backup and Recovery: To mitigate the impact of data encryption incidents, maintain immutable, offline backups and test restoration procedures regularly.
- Threat Intelligence: Stay informed on emerging threat actors relevant to manufacturing, including their TTPs and targeted vulnerabilities. Beyond detection, this focused intelligence helps to develop, for instance:
- Threat models for edge devices and OT assets
- OT-specific incident response playbooks that can reduce mean time to respond
- Secure Emerging Technologies:
- Perform comprehensive risk assessments before deploying new manufacturing technologies
- Use the same security maturity requirements of critical vendors for vendors of risky new technologies
- Consider specialized monitoring for novel attack vectors introduced by these technologies
Appendix: Threat Actor Capabilities
| RansomHub | · Ransomware developed in Golang and C++, targeting Windows, Linux, and ESXi systems · Fast encryption using Curve25519, ChaCha20, and AES with similarities to Knight ransomware · Remote encryption capability via SFTP (advertised July 2024) · Initial access via spear-phishing, voice scams, vulnerability exploitation · Lateral Movement via PsExec and PowerShell · Defense evasion using batch files, EDR Kill Shifter (BYOVD), PCHunter · Double extortion · Deletion of shadow copies and backups · Some variants force reboots into Safe Mode for encryption · Betruger backdoor for pre-encryption tasks |
| LockBit 3.0 | · C/C++ ransomware targeting Windows and Linux systems · Strong encryption (AES, RSA) · Double/triple extortion tactics · Initial access via vulnerability exploitation, phishing, compromised credentials · Lateral movement using PsExec, potentially Cobalt Strike, RDP, SMB · Credential access via Mimikatz or built-in tools · Advanced anti-analysis techniques · Disabling security solutions (e.g., TrueSightKiller/BYOVD) · Deleting shadow copies · Modular design with self-spreading capabilities |
| Akira | · Go-based ransomware targeting Windows, Linux, and ESXi systems · Initial access via VPN vulnerabilities (Cisco AnyConnect) · Lateral movement via AnyDesk, RDP, potentially Cobalt Strike · Credential access using Mimikatz, LSASS memory dumps, NTDS.dit extraction · Discovery tools like AdFind, Netscan · Defense evasion via shadow copy deletion, EDR bypassing · Hybrid ChaCha20/RSA encryption · Linux variant avoids encrypting specific system files |
| Fog | · Initial access via compromised VPN credentials (SonicWall) · Standard ransomware kill chain: enumeration, lateral movement, exfiltration, encryption · Exploitation of Veeam vulnerability CVE-2024-40711 · Use of LOLBins |
| Medusa | · Initial access via vulnerability exploitation or phishing · Heavy use of Living-Off-The-Land techniques · Discovery using Advanced IP Scanner, SoftPerfect Network Scanner · Lateral movement via RDP and PsExec · Persistence using legitimate remote access tools · Credential access via Mimikatz · Defense evasion through EDR/AV disabling, PowerShell history deletion · Data exfiltration using Rclone and RoboCopy · Ransomware capable of terminating 200+Windows services/processes |
| Qilin (Agenda) | · Ransomware variants in both Golang and Rust · Multi-platform targeting (Windows, Linux, ESXi) · Vulnerability exploitation for initial access · Double extortion |
| Play (PlayCrypt) | · C++ransomware · Initial access via network vulnerabilities or stolen credentials · Lateral movement using Cobalt Strike, PsExec, SMB/RDP exploitation · Discovery via legitimate tools (Adfind, nltest, WMI) · Credential access via Mimikatz · Persistence via scheduled tasks · Defense evasion through security tool disabling, shadow copy deletion · Double extortion tactics · WinPEAS for privilege escalation enumeration |
| BlackSuit | · Significant code overlap with Royal ransomware · Intermittent/partial encryption for speed and evasion · Initial access via phishing, vulnerability exploitation, RDP, IABs · Lateral movement using PsExec, SMB/RDP exploitation · Persistence via AnyDesk, ConnectWise · Discovery via Advanced IP Scanner · Credential access techniques like Kerberoasting · Double extortion tactics · 7-Zip for data archiving before exfiltration |
| Clop (Cl0p) | · Specializes in exploiting zero-day/recent vulnerabilities in secure file transfer solutions · “Smash-and-grab” data exfiltration followed by extortion · Often operates without deploying encryption ransomware · Quadruple extortion tactics (encryption threat, data leak threat, DDoS, contacting victims’ customers/partners) |
Find our threat analysis valuable? Have it pushed to you every month in our newsletter.