It’s time to recognize official security vulnerability catalog systems aren’t enough. There are too many gaps in the named security vulnerability process. And plenty of vulnerabilities do not receive the attention they deserve.
Some vendors silently patch issues while others leave vulnerabilities in a reserved state. There is not one source of information that contains every vulnerability being exploited.
The result? Major gaps in time and your security team’s responsiveness and effectiveness. Vulnerabilities are being discovered, weaponized and exploited in the wild faster than ever. Last year, there were 97 zero days exploited. In 2024, we’re already up to 31 zero days in May.
In our new report “Exposing the Exploited”, Forescout Research – Vedere Labs analyzes the landscape of exploited vulnerabilities and shows that there is a world of issues not captured by CISA’s Known Exploited Vulnerabilities (KEV). Defenders need other sources of threat intelligence to ensure more complete protection.
Gaps in CISA KEV and other vulnerability naming catalogs
Vulnerabilities with no CVE identifiers and CVSS scores that do not reflect real risk are well-known in the security industry. Exploit predictions are useful to understand what may happen in the future.
But what about currently exploited vulnerabilities in the wild that aren’t recognized this way?
Vedere Labs is not second-guessing each official vulnerability group’s mission or mandate – or its challenges. But we would be remiss in our duties as a research organization if we did not address the elephant in the room: The speed of accurate vulnerability information matters. CISA KEV is helpful. It is the most well-known catalog for exploited vulnerabilities, but it comes with some limitations.
Exposing the Exploited offers a comprehensive view of vulnerabilities being exploited in real-world scenarios. Furthermore, this research sheds light on lesser-discussed vulnerabilities, going beyond the hype surrounding widely exploited ones.
Main findings of our exploited vulnerabilities research
- Nearly 90,000 vulnerabilities are without a CVE ID — and the number increases every year
- There were more than 21,200 issues discovered in 2023 with an unassigned CVE ID
- Up 4% from 2022
- And up 45% from 2021
- 44% of the vulnerabilities without a CVE ID can be used to gain access to a system
- 37% have high or critical severity
- 45 exploited vulnerabilities did not have a CVE ID (2.15% of the total)
- A total of 2,087 distinct exploited vulnerabilities were seen across four databases:
- CISA KEV, AttackerKB, Shadowserver, VL-KEV
- No database alone contained all the information
- CISA had 50% of the total exploited vulnerabilities (1055)
- 47% are seen in only one database (968)
- Only 4% are seen in all four (90)
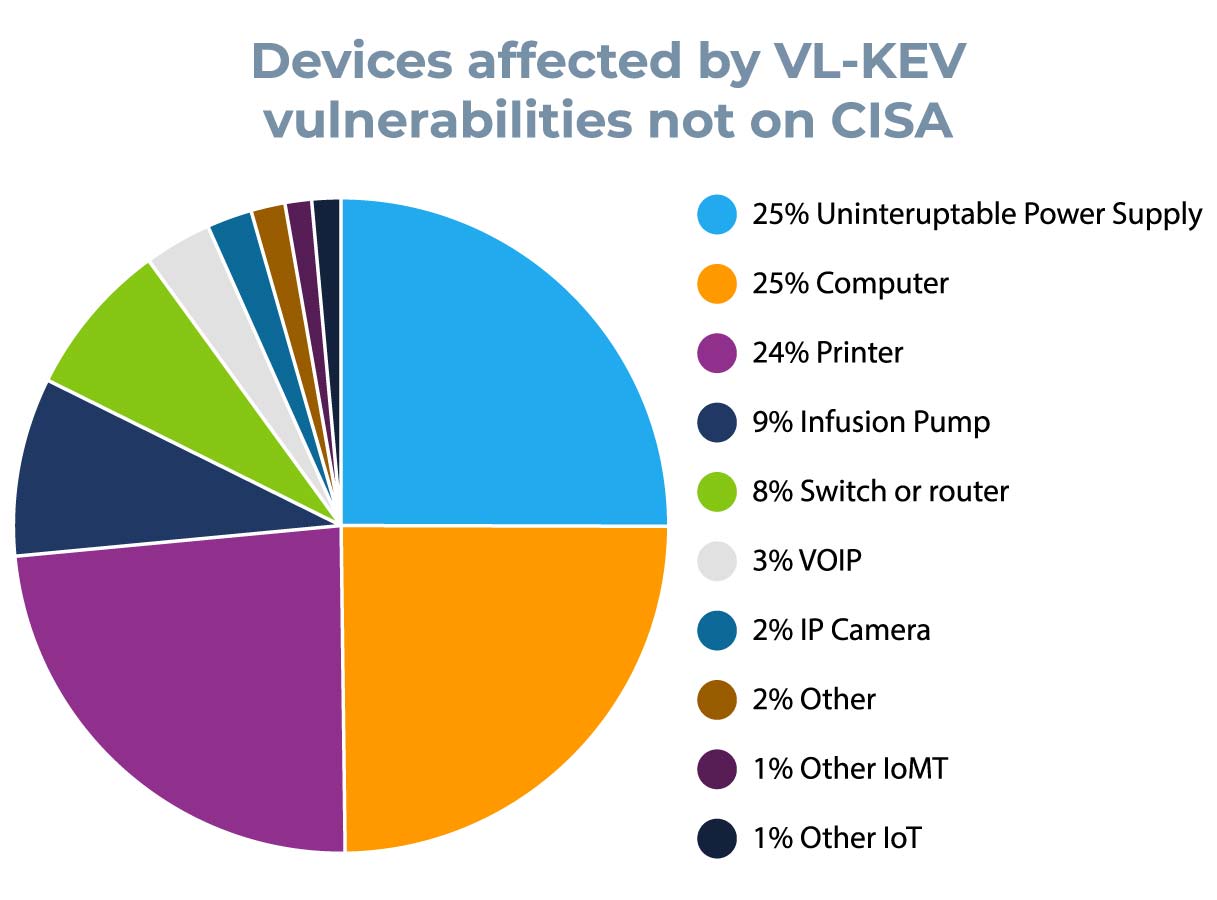
- Thousands of devices on our customer networks are affected by 28 vulnerabilities in our catalog (Vedere Labs Known Exploited Vulnerabilities – VL-KEV) that are not tracked by CISA. Most of these devices were:
- Uninterruptible power supplies (UPS)
- Computers, printers, infusion pumps
- Network equipment
- Hundreds of these devices are exposed to the internet
Access the report for a complete list of all our research findings – including the most common targets and payload patterns.
The importance of vulnerability selection transparency — and threat intelligence
Given the ever-growing number of vulnerabilities found and exploited by malicious actors, organizations need help to understand what to prioritize. CISA KEV is an important resource to help with this prioritization by identifying vulnerabilities that have been or are being exploited. But it suffers from issues, including a lack of transparency on the selection of vulnerabilities.
Our report shows that there are many exploited vulnerabilities not captured in CISA KEV that affect real organizations. Since no single database includes every exploited vulnerability, security teams must rely on multiple sources.
Keep in mind that a list of exploited vulnerabilities is not useful if it cannot lead to risk mitigation. For example, a device running a vulnerable HTTP server version, but configured with that service disabled does not present an immediate risk. Organizations need a way to:
- Automatically identify assets on a vulnerable network
- Identify issues currently being exploited
- Automatically understand the context in which these assets may be vulnerable
Only with the full picture of what a device is, how it is configured, and how it behaves on the network can a database of exploited vulnerabilities be effectively used for patching prioritization and risk mitigation. This is especially true for OT networks where patching is a time-consuming effort that needs to be carefully planned.