Depending on what the world’s threat actors are up to and whether their activity is detected, CISA may issue a cybersecurity advisory (CSA) every few days or have nothing for a month. It’s hard to predict, and you never know what’s coming your way. One thing is certain: If you managed cybersecurity for a critical infrastructure entity and this #StopRansomware: BianLian Ransomware Group CSA landed in your inbox, you would probably want to take swift action.
The advisory, released by CISA jointly with the FBI and the Australian Cyber Security Centre, details how BianLian has targeted organizations in multiple U.S. critical infrastructure sectors since June 2022, and has also targeted Australian critical infrastructure sectors, professional services and property development. The group gains initial access to victim systems through valid Remote Desktop Protocol (RDP) credentials to log into internet-exposed systems, then uses open-source tools and command-line scripting for discovery and credential harvesting, and exfiltrates victim data via File Transfer Protocol (FTP), Rclone or Mega.
What does a system administrator or security operations center (SOC) analyst do with this information?
Leveraging XDR with cybersecurity advisories to quickly remove blind spots
CISA CSAs are actionable in that they thoroughly document observed activity, including indicators of compromise (IOCs) and tactics, techniques and procedures (TTPs) by attack stage, which are mapped to the MITRE ATT&CK for Enterprise v13 framework. From the advisory, you can click on any TTP and learn all about it on the MITRE ATT&CK site, including mitigation and detection strategies for it and any sub-techniques. But how likely are you to take the necessary actions, and how long would it take to do so?
Extended threat detection and response (XDR) tools are immensely helpful here. Where once you would perhaps add this CSA to a long list of other urgent matters needing further investigation, now you can correlate the TTPs in the advisory with the data sources you’ve configured in Forescout Threat Detection & Response and the logs and network telemetry you’re consuming from them to quickly know whether the detections that need to happen are happening. That’s a critical piece of governance.
Here’s what that looks like in Forescout TDR.
Checking TTP coverage for initial access/attack surface exposure
Forescout TDR features an intuitive MITRE ATT&CK matrix that shows what data sources need to be ingested for broad or specific TTP coverage, to identify potential blind spots that adversaries can exploit and to determine which additional data sources would further elevate your coverage. The TTPs are organized by stage and identified as green if live and configured in TDR, red if the connection is broken or black if the data source is not configured.
Here’s how a SOC analyst would use Forescout Threat Detection & Response to ensure their organization is covered for a specific TTP in this advisory. For this example, let’s look at one of three TTPs used to gain initial access: T1133: External Remote Services. This is all about knowing how many Remote Desktop Protocol (RDP) surfaces in your attack surface are exposed to the internet. You can also watch me demo these steps in the video below:
- In the online CSA, scroll down to the MITRE ATT&CK Techniques section (Table 2) to identify the first CSA you want to investigate: External Remote Services T1133.
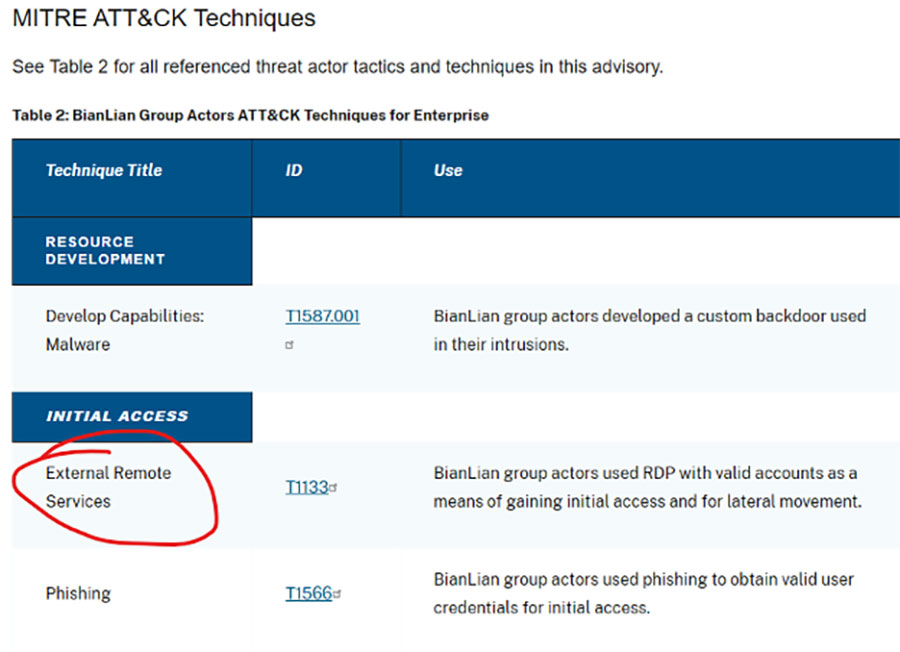
- In Forescout Threat Detection & Response, navigate to the MITRE ATT&CK Matrix dashboard. Locate TTP T1133 in the Initial Access column. Good news – it’s green.
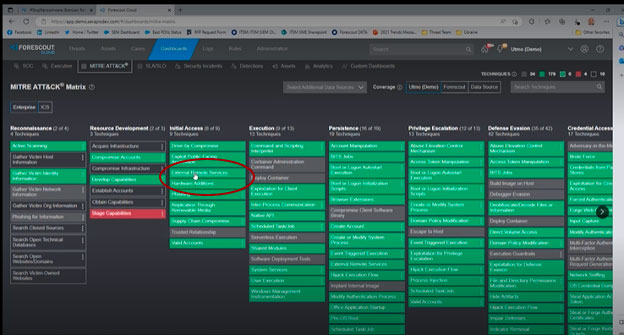
- Click on the TTP to drill into the seven rules that are available to detect it. All seven are checked as enabled – more good news. If there were no checkmark next to a rule, that would mean it’s available but needs to be configured.
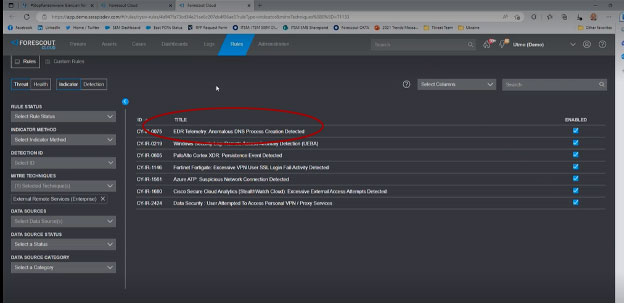
- Click on the first rule in the list, EDR Telemetry: Anomalous DNS Process Creation Detected, to learn its details.
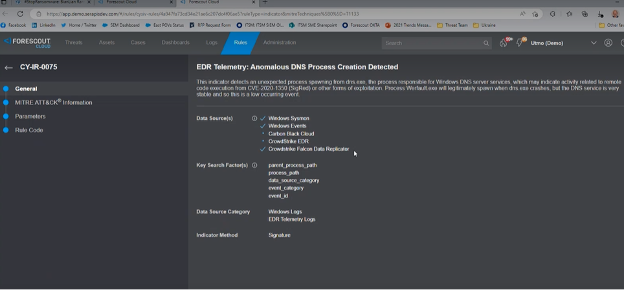
It’s enabled but only being fed by three out of five available data sources. For the best coverage, you need to configure Carbon Black Cloud and CrowdStrike EDR. This is important to realize: just because tools are available in your environment doesn’t mean they’ve been ingested into your threat detection & response tool and properly configured to detect potential attacks. If you don’t want to buy additional data sources, that’s your call. But if you already have them, be sure they’re enabled.
Configuring new data sources for threat detection in seconds
Many SIEMs are notorious for how difficult, costly and time-intensive it is to onboard new data sources. In Forescout Threat Detection & Response, we’ve done the legwork to make onboarding new sources as easy as possible.
Out of the box we provide connectors to ingest more than 170 vendor- and EDR-agnostic data sources. Once the data is flowing, it is automatically normalized using a common information model (CIM) into our data lake. This heavy lifting on our part helps ensure that you extract maximum detection value to support your most important use cases and can defend your environment from the TTPs targeting your industry.
Adding a new data source takes a few seconds. To enable the Carbon Black EDR in our example, simply click on that data source, select a connector from the list, identify the port where the data is coming from and download the connector. The connection is immediately established.
Defending against threat actors who are creatures of habit
The time-to-value and efficiency gained from having all these data sources ready to plug and play for your SOC analysts is exponential. Whether you’re going through the TTPs in a CSA targeting your industry or evaluating new data sources and security tools more broadly, leveraging the MITRE ATT&CK matrix to gain assurance that you have adequate coverage is a game changer.
Without it, you probably have myriad tools and intelligence sources that could provide the coverage you need for various TTPs, but you have no way to verify that they do – or pinpoint what you need to do to get there.
Instead of running down individual CSAs, it’s best to step back and defend more widely against adversaries that are known to target your sector. Threat actors are creatures of habit: they will use the same, well-documented TTPs to gain initial access, establish credentials, and so on, that they’ve been successful with until their operations are significantly disrupted. With that information in hand:
- Open the MITRE ATT&CK matrix in Forescout Threat Detection & Response.
- Click on one of the known TTPs to drill down into the associated indicators.
- See which tools and data sources Threat Detection & Response needs to ingest to detect them.
- If something is available in your environment but not enabled, select the right connector.
- If something isn’t available but needed, model how much coverage you would gain if you purchased it.
- Repeat with other TTPs.