Device Security is Critical in Protecting Patient Data and Keeping Patients Safe
From the time of a medical accident, your personal health records are shared across dozens of devices and medical networks before multiplying across provider EHR systems.
The volume of hospital admissions has varied over the years in the U.S., spiking in the early 80s at around 39 million and settling to roughly 37.5 million in 2017. While the admission rates have varied, there’s one thing that has been on a very steady rise: the volume of digital data collected by hospitals and healthcare providers—data that, once collected, seems to take a shadowy journey alongside the patient as they progress from initial contact, to triage, treatment, recovery and eventually departure and aftercare. When a medical emergency happens, patients don’t have time to worry about their data—and they shouldn’t have to—so we examined 75 healthcare deployments with over 10,000 Virtual Local Area Networks (VLANs) and more than 1.5 million connected devices on those networks to uncover the truth about how patient data is obtained, maintained and secured, and determine the impact of the explosion of connected medical devices on patient safety and data security.
The Patient Record Evolution
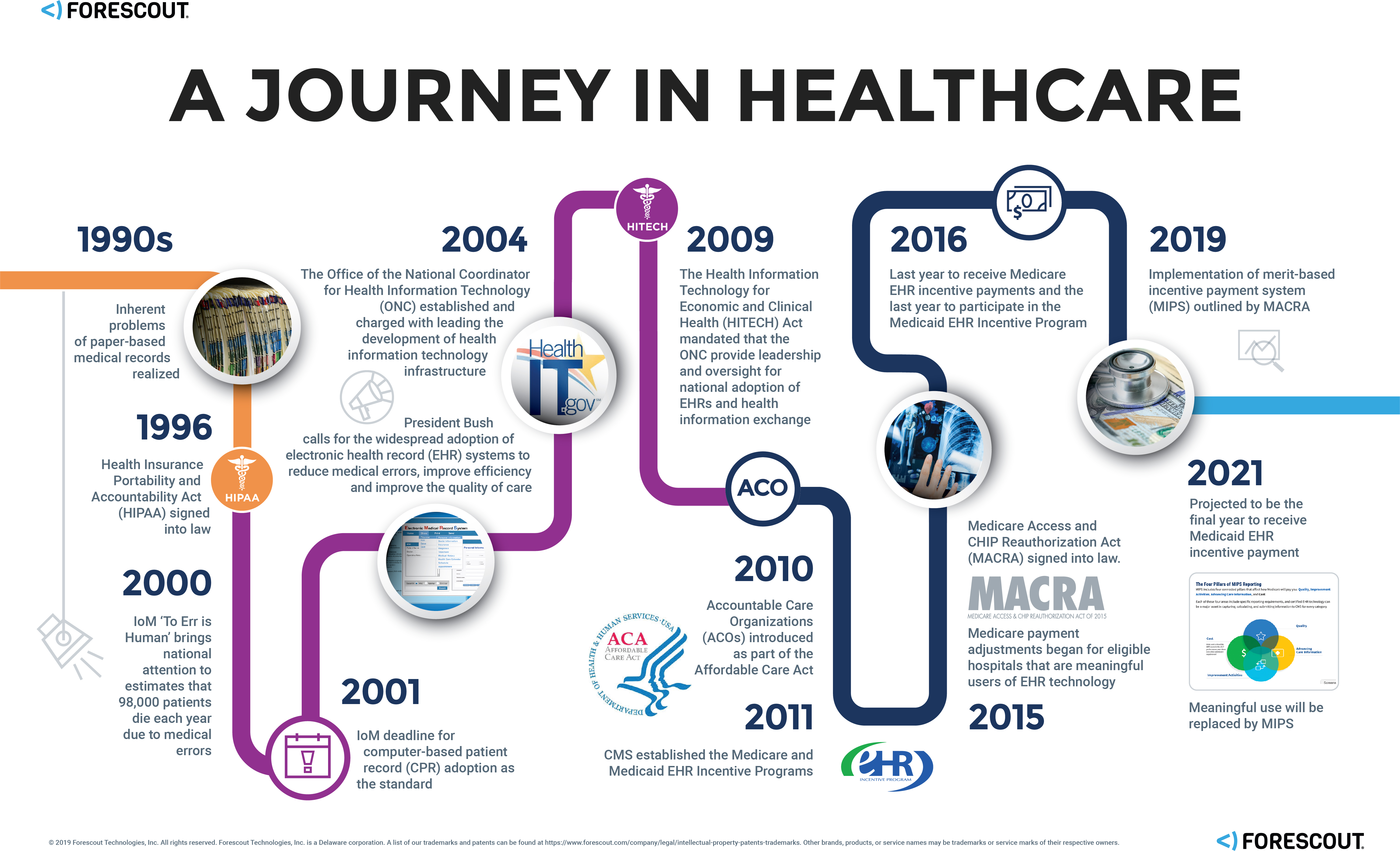
The Internet of Medical Things (IoMT) Explosion
Patient data digitization isn’t the only thing that’s changed; advances in the field of medicine and in information technology (IT) have resulted in the proliferation of connected medical devices, or the Internet of Medical Things (IoMT)—a market that’s expected to reach $136.8 billion worldwide by 2021. From connected pacemakers and infusion pumps to smart beds and patient activity trackers, there have been remarkable medical device innovations in recent years—innovations intended to reduce medical errors, ensure patient safety and improve the quality of care.
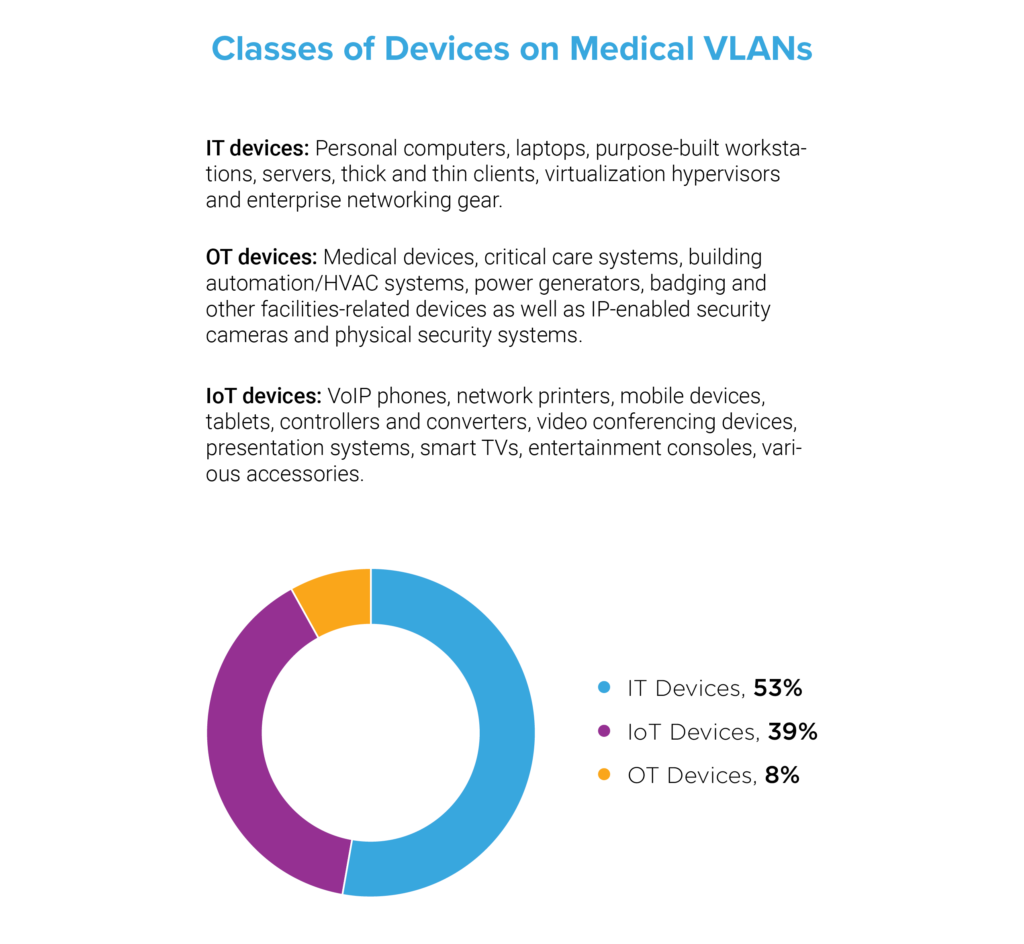
Device Proliferation and the Convergence of IT, OT, and IoT
We investigated the volume and variety of medical devices on healthcare networks in our sample and found that 53 percent were IT or traditional computing devices—personal computers, laptops, purpose-built workstations, servers, thick and thin clients, virtualization hypervisors and enterprise networking gear. Next, we found that 8 percent were operational technology (OT) devices—a collection of connected medical devices and critical care systems as well as building automation/HVAC systems, power generators, badging and other facilities-related devices as well as IP-enabled security cameras and physical security systems. Finally, we found that 39 percent were IoT devices—devices beyond the categories of IT and OT such as network printers, mobile devices, tablets, video conferencing devices, smart TVs and entertainment consoles. These findings indicate that, despite the proliferation of connected medical devices, nearly half of the devices on medical networks are non-traditional assets. There are simply more VoIP phones, connected printers, computer accessories and IoT gadgets than there are actual medical devices. Yet, each type of device, regardless of classification, presents a unique risk.
The Modern Patient Experience
The patient healthcare path can be categorized at a high level as inpatient care and outpatient care, where the primary difference is determined by length of hospitalization. Inpatient care requires overnight hospitalization—for things like major surgery or where continuous monitoring is required. Outpatient care, however, is usually done quickly and allows the patient the comfort of recovering from home and typically includes basic procedures such as biopsy, arthroscopy and gastric bypass, to name a few.
As an example, when someone is involved in a car accident, first responders arrive on the scene and within a matter of seconds, the person involved in the accident becomes a connected patient. They are moved to a collapsible wheeled stretcher, loaded into an ambulance, and delivered to the local hospital, and connected to a variety of devices at each stage. Upon initial contact at the scene, vitals are collected, along with patient name, address and anything else readily available from their billfold or purse. In another scenario where an accident takes place at a personal residence, paramedics may not only check the patient’s body for identification, but they may also check a cell phone for identifying information, or a refrigerator for recently used medication. In both of these scenarios, the EMTs are collecting personally identifiable information (PII) that may eventually be linked to that individual’s EHR.
These outpatient scenarios are uniquely different from the inpatient scenarios where a patient has the opportunity to research their healthcare provider, schedule an appointment, and provide healthcare information and PII upon the request of the provider. However, regardless of whether a patient receives in- or outpatient care, they will be connected to a number of medical devices.
How many devices are patients connected to, anyway?
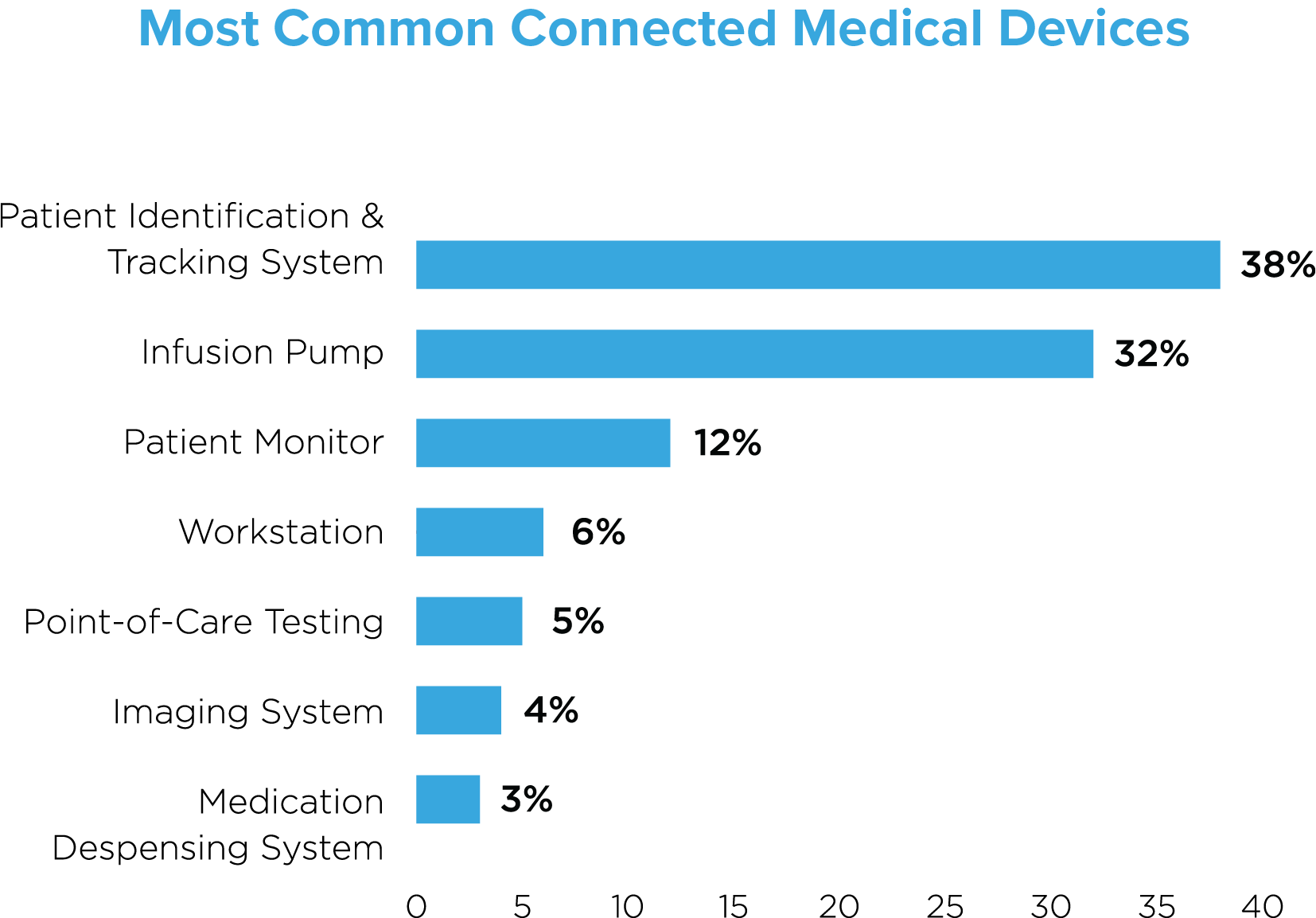
From smart medical beds to assist with patient monitoring, infusion pumps to deliver medicine automatically and mobile beacons for smart transit, to blood glucose monitors, ingestible sensors and closed-loop (automated) insulin delivery, there’s a seemingly endless number of connected medical devices that patients may encounter. Every patient journey is different, but patient needs no longer only dictate treatment—they also determine what patients are connected to and how their data is shared. A patient requiring robotics surgery, for example, may be connected to significantly more devices than a patient being treated for a common cold.
Our research across 75 active deployments found that patient identification and tracking systems constituted the majority of devices (38%), followed by infusion pumps (32%) and patient monitors (12%). These top three devices are typically assigned to individual patients, reflecting a 1:1 patient to device ratio. The other commonly identified devices—workstations, point-of-care testing devices, imaging systems and medication dispensing systems reflect a one-to-many patient to device ratio.
EHR records multiply thanks to Health Information Exchange (HIE)
In our model patient journey, PHI may be collected and shared over dozens of different devices in the initial episode of care (from initial contact to departure from the hospital). But more troubling is the aftermath: records then proliferate as our model patient continues the journey to recovery along an extended continuum of care and visits to many outpatient clinics—records multiply across multiple HDOs who are collaborating in order to maximize the quality of patient care. Unfortunately, the sharing of health data that requires also results in additional patient risks in a never-ending struggle to balance safety with efficiency. The HIPAA minimum necessary standard addresses these complications and is intended to reduce this impact, but unfortunately, by multiplying the number of PHI data stores, exposure invariably increases.
Put simply, patient EHRs are part of a massive data pipeline—but the networks that data routinely and repeatedly traverses commonly fail to implement network segmentation, a security best practice.
Many devices. Many providers. Many patient safety and privacy risks.
The U.S. Food and Drug Administration (FDA) has recognized the rapid growth of connected medical devices in recent years and has provided both pre- and postmarket guidance for the management of cybersecurity in medical devices. Although not legislation, the guidance clearly states that ‘medical device manufacturers (MDMs) and HDOs are responsible for putting appropriate mitigations in place to address patient safety risks and ensure proper device performance.’ However, just last year we saw that third-party vendors working with healthcare providers accounted for 20 percent of data breaches. There are multiple contributing factors, but ultimately there simply isn’t a workflow in place to manage the risks.
As noted above, many devices are dedicated to a single patient—things like infusion pumps—but there are many other devices that are shared among multiple patients. The same is true of devices that aren’t necessarily connected, at least not yet. But, there’s often great care taken with those unconnected devices to ensure patient safety. Nurses put a fresh sheet of wax paper on the examination table between patients, doctors put a soft plastic disposable shield on their otoscope before looking into a patient’s mouth, eyes or ears, and healthcare providers use sterilized syringes and needles on every patient.
None of those unconnected ‘devices’ are carrying patient data, but they are tools used by healthcare providers to ensure patient safety—to execute the healthcare mission. Just as care is given to sterilize those tools, so too should special care be given to secure the devices that are handling PHI and contributing to central EHR records. Patients expect care providers to make patient safety their top concern—they should expect the same when it comes to the security and privacy of their personal healthcare data.
